- Mac scareware is getting worse
- Browser redirect viruses are taking the Mac world by storm
- Ad-injectors are prolific, too
- Social engineering dominates the virus distribution landscape
- Mac ransomware is here to stay
- Malware removal from MacBook Air (manual way)
- Get rid of MacBook Air malware virus in web browser on Mac
- Automatic malware removal from MacBook Air
- FAQ
This tutorial covers the prevalent categories of malicious code targeting MacBook Air and includes simple walkthroughs to remove malware from these laptops.
Update:
Mac malware is no longer a marginal phenomenon. The good news is, it’s in a somewhat primitive state compared to Windows viruses so far. The bad news, though, is that the macOS ecosystem is an expanding battlefield, where the adversaries from the deep web are quickly getting better at orchestrating their campaigns. MacBook Air laptops are in the crooks’ spotlight due to their popularity with Apple fans, affordable price and, hence, a great number of these machines scattered all over the world. Looking at the present-day security risks these devices are susceptible to, people familiar with Windows malware evolution may reminisce about the reign of rogue antispyware from the late 2000s. Indeed, counterfeit optimization or security apps are currently gearing up for a rise in the MacBook Air environment.
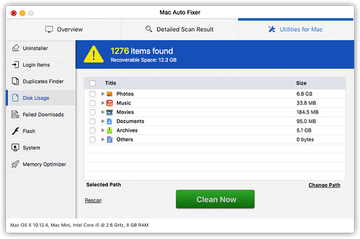
Mac scareware is getting worse
One of the recent examples of this annoying scareware is the program called Mac Auto Fixer (see screenshot above). It is a segment in a lineage of fake utilities, including the ill-famed Advanced Mac Cleaner and Mac Tonic. The culprit typically infiltrates MacBook Air’s by means of a multi-component installation trick. It means you get infected while installing some free application that goes surreptitiously bundled with one or several extra programs, often potentially unwanted ones. This type of software setup logic is one of virus deployers’ favorites, so you’re always better off opting out of the default option in the install client and selecting the custom route instead – this way, you’ll at least be able to see what else is being pushed alongside the solution of choice.
Malware may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.When up and running inside a MacBook Air, a rogue AV or cleaning tool pretends to check the system for issues and returns results with dozens or even hundreds of them. This is a tactic aimed at pressuring the victim into removing the purportedly detected problems, which presupposes payment for the “licensed” version of the impostor. Unfortunately, this category of harmful software is on a dramatic rise these days, so you’d better be on the lookout for it.
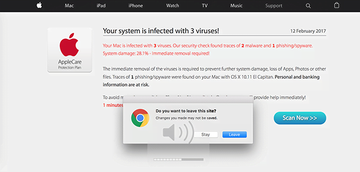
Browser redirect viruses are taking the Mac world by storm
Another major cluster of malware going after MacBook Air machines is browser hijackers. As the name suggests, their goal is to take control of Safari and user-installed web browsers so that a predefined landing page is visited at random or during certain routine actions of the victim. For example, the deceptive site can show up whenever you open the browser, trigger a new tab in it or perform web search. Technically, the infection replaces one’s Internet navigation preferences, such as the homepage, new tab and search, with a specific URL that’s predefined to display some manipulative information. One of the nastiest hijackers of this kind is one that diverts traffic to a page saying, “Your system is infected with 3 viruses!” It attempts to dupe you into thinking that your laptop is malware-stricken and hitting the ‘Scan Now’ button that leads to another dangerous payload.
Today’s most widespread forms of browser hijackers targeting MacBook Air reroute the traffic to Bing or Yahoo without explicitly asking for permission to do so. This scheme piggybacks on the reputation of these trusted search providers to hide a tricky monetization mechanism in plain sight. While the redirect loop culminates with either one of the above-mentioned legitimate services, the browser resolves a series of sketchy URLs for a split second. In the Bing case, these include searchmarquis.com, searchbaron.com, searchitnow.info, and searchsnow.com. The Yahoo redirect virus mostly involves the following interstitial pages: search.safefinder.com, feed.safefinder.com, search.tapufind.com, searchmine.net, search.chill-tab.com, and search.anysearchmanager.com. Threat actors benefit from these hoaxes because they stealthily integrate advertising networks into the web traffic forwarding workflow.
Ad-injectors are prolific, too
There’s one more shade of Mac browser threats that comes down to embedding pesky advertisements into web pages. It’s referred to as adware. These baddies aren’t severe as far as the system-wide impact goes, but the irritation they cause tends to be huge. Ad-injecting viruses flood nearly all web pages you open on a contaminated MacBook Air with numerous popups, pop-unders, coupons, freebies, comparison shopping elements, banners, and in-text links. To top it off, they sort of wrap the visited websites with an invisible virtual coating that, when clicked on with the mouse, invokes scripts triggering full-page interstitial ads. This leads to multiple browser windows opening up behind your back, which in its turn consumes CPU resources you might need for other, benign tasks. Similarly to hijackers, ad viruses usually slither their way into Macs through booby-trapped freeware installs.
Social engineering dominates the virus distribution landscape
In 2020, Mac adware and scareware threats took a major leap in distribution, and the trend continues in 2021. Whereas their operators’ toolkit is versatile, the main vector of the infection is the now infamous fake Adobe Flash Player update campaign. Technically, this hoax is a typical bundling scheme where an installer’s component that appears to be harmless additionally promotes a dubious application behind the scenes. MacBook Air users fall victim to this scam when visiting websites previously hacked by malicious actors or created for the sole purpose of hosting the contagion. A slew of alerts popping up on such pages say the Flash Player is out of date and prompts the user to download and install the latest version. At the end of the day, the ostensibly legit software update turns out to be a wolf in sheep’s clothing as it pushes a piece of companion malware.
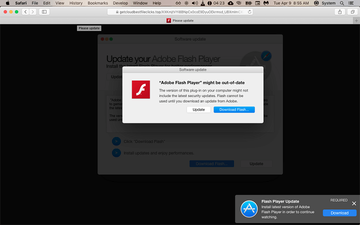
Mac ransomware is here to stay
Ransomware, in the classic sense, isn’t too much of an issue in the macOS world so far, although it exists and appears to be undergoing tweaks and refinements. The so-called FBI or police viruses aren’t really ransom Trojans, because their adverse effect is isolated to browsers only and the fix is as simple as resetting the browser. A much more harmful example is the KeRanger virus that emerged in March 2016, which actually encrypted personal files on a plagued MacBook Air with asymmetric cipher and dropped a ransom note demanding Bitcoins for the RSA decryption key. Although the likes of it never got to massive distribution and their code is typically crude and buggy, blackmail viruses targeting Mac computers are way beyond proof-of-concept nowadays.
No matter what kind of malware might be causing your MacBook Air to act up, you should follow the one-size-fits-all tutorial below to get rid of it and rectify whatever system settings got skewed by the intruder.
Malware removal from MacBook Air (manual way)
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
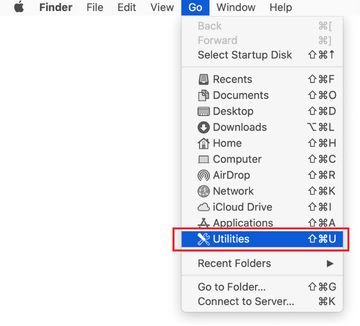
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
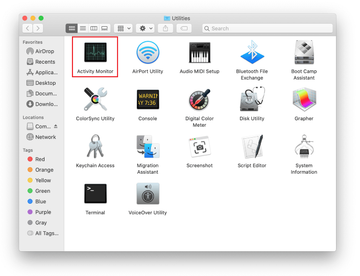
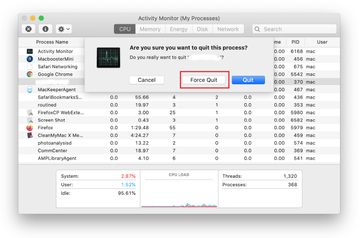
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
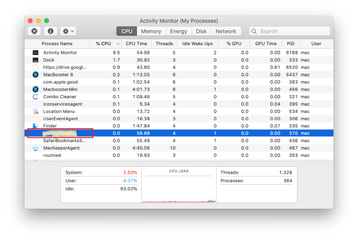
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
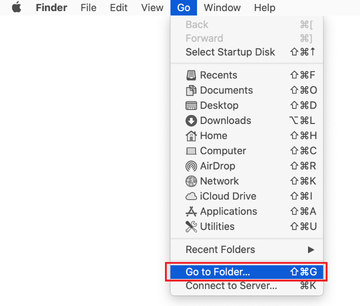
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
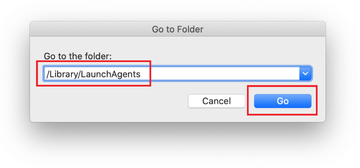
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
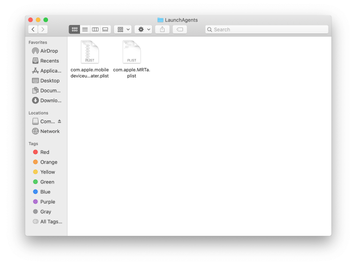
Examine the contents of the LaunchAgents folder for dubious-looking items. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
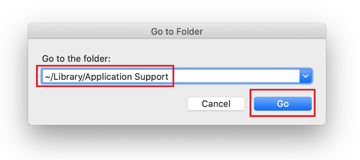
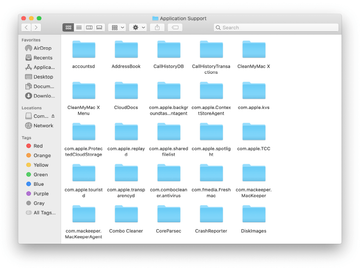
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are SystemSpecial, ProgressSite, and IdeaShared.
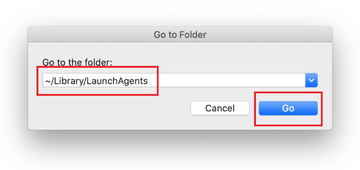
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
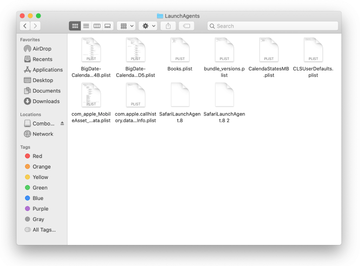
The system will display LaunchAgents residing in the current user’s Home directory. Look for dodgy items related to the virus (see logic highlighted in subsections above) and drag the suspects to the Trash.
Type /Library/LaunchDaemons in the Go to Folder search field.
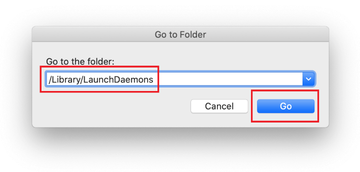
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
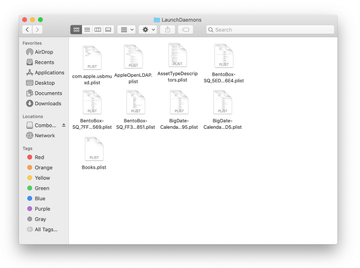
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
Find the entry for an app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

Expand the Apple menu and select System Preferences.
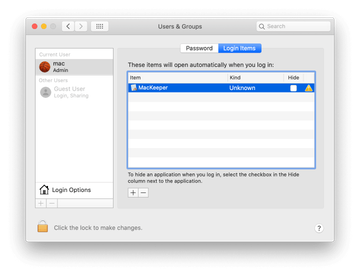
Proceed to Users & Groups and click on the Login Items tab.
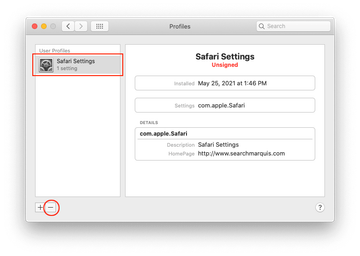
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of MacBook Air malware virus in web browser on Mac
To begin with, the web browser settings taken over by the MacBook Air malware virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Remove MacBook Air malware virus from Safari
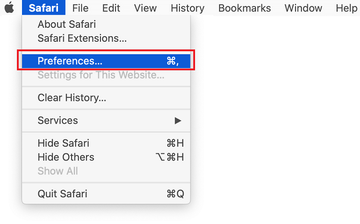
Open the browser and go to Safari menu. Select Preferences in the drop-down list.
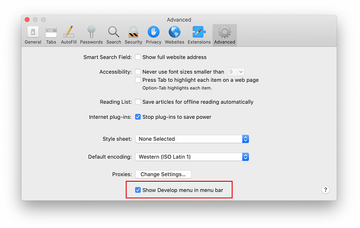
Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
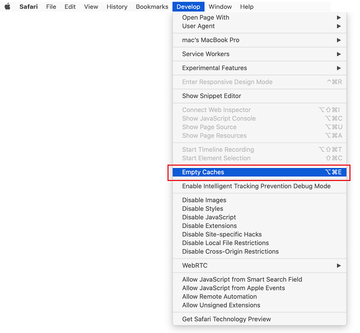
Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
Now select History in the Safari menu and click on Clear History in the drop-down list.
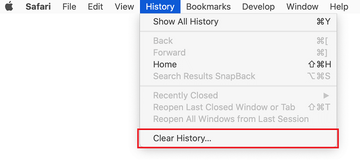
Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
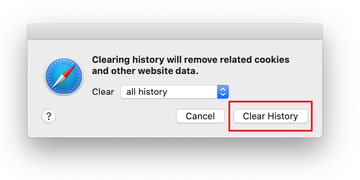
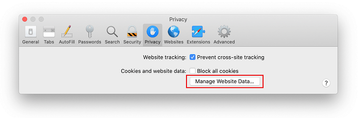
Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
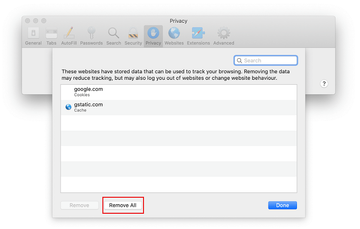
The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
Restart Safari
- Remove MacBook Air malware in Google Chrome
Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
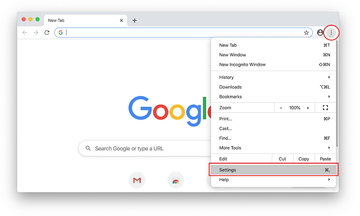
When on the Settings pane, select Advanced
Scroll down to the Reset settings section.
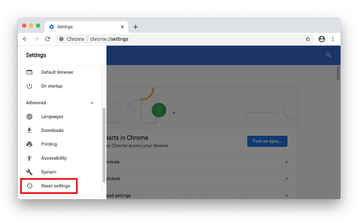
Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
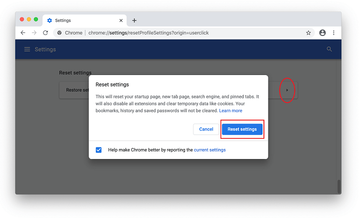
- Remove MacBook Air malware from Mozilla Firefox
Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
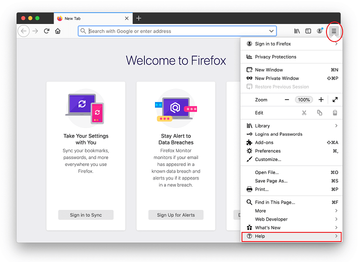
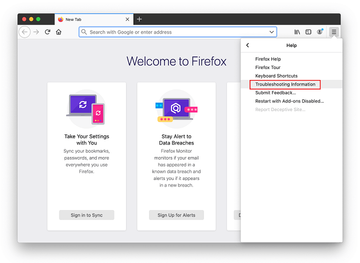
When on the Troubleshooting Information screen, click on the Refresh Firefox button.
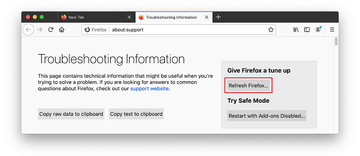
Confirm the intended changes and restart Firefox.
Automatic malware removal from MacBook Air
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove MacBook Air malware virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the MacBook Air malware issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
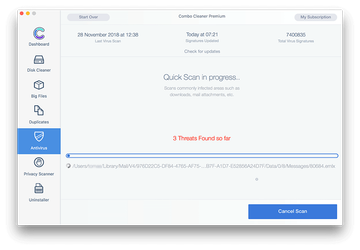
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
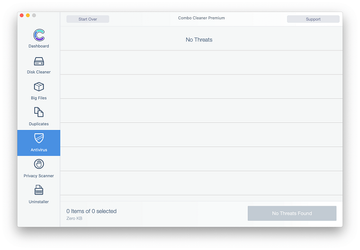
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove MacBook Air malware threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
FAQ
How do I check for malware on my MacBook Air?
There are two ways: one is to inspect your MacBook Air for traces of malware manually, and the other is to use a cleaner that will automatically do it for you. Obviously, the former method is only appropriate if you are tech-savvy and know how and where to look. The latter is more effective because the odds of the tool failing to spot malicious files, including hidden ones, are very low.
If you choose to take the manual route, you’ll need to examine the running processes for suspicious items in the Activity Monitor for a start. The next stage is to check the following system folders for recently added entries that look out of place: LaunchAgents, LaunchDaemons, and Application Support. Note that Mac malware may create harmless-looking files with random names, so you’ll have to follow your intuition in some cases to pinpoint the bad ones.
Peeking in the Applications folder to scour it for potentially unwanted software is one more important step to take. Plus, adware threats often create dubious device profiles that control system behavior, so heading to the Profiles feature under System Preferences is on your checklist as well. You should also go to browser settings to see if any sketchy extensions are installed. See detailed instructions in the guide above to vanquish the culprit manually.
If this looks a bit too complicated, then try an automatic antimalware tool that will scan your Mac for infections with no strings attached. Be advised that whereas the scan feature is free, you will need to register the licensed version to get rid of the detected threats.
How do I get rid of malware on my Mac for free?
There are hardly any alternatives to manual removal if you need a free fix. As outlined in the previous answer, you’ll need to do your homework and traverse multiple macOS components and directories for files deposited by malware. Deleting each one of these items by hand is what does the trick. This could be easier said than done, though. The possible roadblocks revolve around the notorious persistence of some modern Mac malware families and the fact that the pest may reinstall itself if you skip some of its files lurking deep down the system.
Mac adware and scareware tends to drop its components into the overarching Library path, namely its structural elements such as LaunchAgents, LaunchDaemons, and Application Support. Another obvious place to look is the Applications folder. Anything that doesn’t belong in these locations should be sent to the Trash. You also need to force quit the harmful process in the Activity Monitor, eliminate the unwanted login item from Users & Groups, and purge a dodgy entry from the Profiles interface on your Mac.
An extra layer of the cleanup may be required if you’re confronted with a browser hijacker or an ad-injecting virus. If this is the case, you’ll need to find and uninstall the associated browser add-on. Another option is to reset the browser to its original defaults and then re-specify the correct Internet preferences such as the homepage, search provider, and new tab page.
How do I get rid of malware on Safari?
Here’s an important prerequisite for effective cleaning at the browser level: you must remove the underlying malware from the system first. If you don’t, then all your further efforts may be futile because the threat will most likely reinstall the unwanted browser extension and reapply the fraudulent settings.
With that in mind, you can remove malware on Safari by tidying up a number of its areas one by one. Start by emptying caches via the Develop drop-down in the browser menu. If it’s not listed there, go to Safari Preferences, click on the Advanced tab, and check the box next to “Show Develop menu in menu bar”. Then, you need to clear all browsing history and remove all website data. The point-by-point instructions are provided in the article above.
How do you know if your MacBook is infected with a virus?
Few Mac viruses run silently in the background without manifesting themselves. So, there are usually plenty of red flags you should learn to identify. There are generic symptoms such as system slowdown and a noisy fan due to unusually high CPU usage causing the hardware to overheat. Aside from these, the giveaways largely depend on the type of malware that has infiltrated your MacBook.
If it’s adware or a browser hijacker, then your default browser (Safari, Google Chrome, or Mozilla Firefox) will be incessantly redirected to websites you never intended to visit. In some situations, you will be seeing a plethora of ads such as in-text links, popups, banners, and too many sponsored links above search results. The twisted browsing preferences, including your homepage and default search engine, may be grayed out and impossible to change manually.
A scareware attack is accompanied by annoying scan screens and follow-up alerts that try to dupe you into thinking your MacBook is awfully misconfigured, severely infected, and crammed up with memory hogs and unneeded files that should be deleted urgently. Sometimes browser redirects are added to the mix for more pressure.
If you notice any of these telltale signs of virus activity, be sure to check your MacBook for known threats and get rid of the culprit if found. The article above will walk you through the removal of common forms of Mac malware.
