The latest macOS Big Sur update patches a zero-day vulnerability used by XCSSET malware to get around Apple’s TCC privacy protection framework.
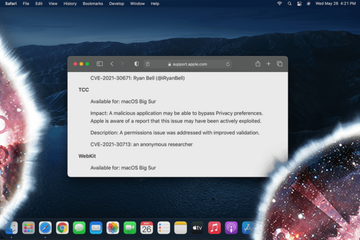
When Apple rolls out security updates for its different platforms, a little bit of scrutiny into their content may reveal the scope of real-world vulnerability exploitation in its ecosystem. This holds true for the macOS Big Sur 11.4 version that went live on May 24, 2021. According to the release notes that cover the security stuffing of this update, one vulnerability stands out from the rest due to a phrase in its description saying, “… this issue may have been actively exploited”. Tracked as CVE-2021-30713, this flaw allows a harmful application to circumvent macOS Privacy preferences. The tech giant has now addressed the bug, but as users linger with applying the update, it will continue to make itself felt.
Vulnerability exploitation vectors
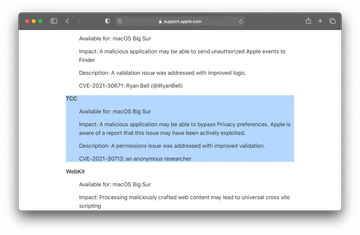
The imperfection in question allows a threat actor to get around Apple’s TCC (Transparency, Consent, and Control) mechanism that kicks in when an app is attempting to perform an action that should require a user’s permission. Effectively, it paves the way for privilege escalation behind the victim’s back. Even more unnervingly, researchers from Jamf found that this particular exploit has been a part of the XCSSET macOS malware’s toolkit. Last year, we posted a write-up about the way this dangerous program poisoned Xcode projects to amass Mac users’ sensitive data on a big scale. It appears that the pest is still going strong.
Bypassing TCC to spy on Big Sur users
The exploitation of the CVE-2021-30713 loophole by XCSSET can lead to serious privacy issues without raising red flags. Malware operators can weaponize it to get full disk access, modify browser sessions, and quietly exfiltrate arbitrary files. Security analysts claim that a recent info-stealing campaign with this malware at its core has been focused specifically on capturing screenshots of the victim’s desktop.
This is a serious encroachment on one’s privacy because it gives the attacker an idea of the user’s activities at any given time while revealing the Dock apps as well as computing and web surfing patterns overall. To stay in the clear, those running Big Sur should download and install the new 11.4 version of the operating system without delay.