Get insights into the noteworthy cybercrime statistics for the XXI century and find out how the global threat landscape will change in the 2020s.
Back in the day when the new Millennium was around the corner, everyone held their breath expecting the Year 2000 (Y2K) bug that could presumably lead to major disruption of the global computer ecosystem. Thankfully, none of this took place and the claims never lived up to the scary predictions. Instead of a sudden crisis, though, we have been witnessing a gradual escalation of cybercrime during the last 20 years. The damages shaped up to be systemic as data breaches, sophisticated attack vectors, and destructive malware exploded into the wild, turning both end-users and major organizations into potential targets.
It’s an indisputable fact that the XXI century is an era of rampant cyber-attack evolution. It gave rise to extortion through file-encrypting ransomware, the scourge of cryptojacking, ubiquitous adware, scareware, fileless viruses, state-sponsored malware, and info-stealing Trojans that slip below the radar of traditional defenses. These issues have reached unprecedented heights – here are some numbers that will give you the big picture:
- According to ENISA Threat Landscape Report 2018, data theft is the number one threat to corporations, having eclipsed physical theft since 2017.
- In 2017, 93% of all malware detected by AV tools was polymorphic, says Webroot. This characteristic enables harmful code to slide unnoticed into an IT environment.
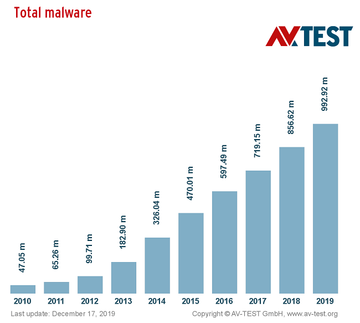
- As per the findings of AV-Test, 136.3 million new malware samples were seen in 2019 alone.
- A study by Imperva reveals that 78% of surveyed organizations fell victim to at least one cyber-attack in 2019.
These statistics are just a sneak peek at the state of the current e-threat landscape. There are plenty of disconcerting trends that demonstrate the heterogeneous essence of the malefactors’ TTP (tactics, techniques, and procedures) and the growingly complex anatomy of cybercrime.
Ransomware ups and downs
The CryptoLocker frenzy that broke out in September 2013 lasted for less than a year, but it became a game-changing wakeup call. This progenitor of all modern ransomware was followed by dozens of copycats and, what’s worse, hundreds of independently developed strains such as the Locky, Cerber, GandCrab, and Dharma lineages.
The fusion of competently implemented cryptography and effective distribution campaigns via phishing and exploits kits allowed the criminals to perpetrate large-scale extortion with personal data as the hostage. The emergence of cryptocurrencies played into the attackers’ hands as well due to the anonymity features making ransom payments virtually untraceable.
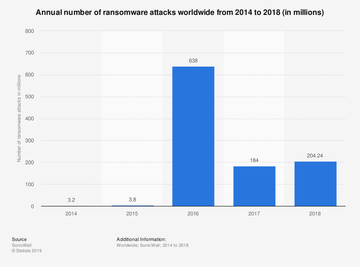
The epidemic had been spreading mayhem at an astonishing rate until early 2017 when telemetry systems of different security vendors started recording a decline. Ransomware infections dropped by 60% overall in a year’s time. Did this nosedive mean that the plague would become obsolete at the end of the day? Not really. The two biggest ransomware outbreaks in history happened during this exact period of the ostensible downswing.
The WannaCry attack that was unleashed in May 2017 polluted more than 200,000 computers around the world in only four days. It took advantage of NSA exploits, EternalBlue and DoublePulsar, to contaminate vulnerable hosts without any noticeable signs of the intrusion. The total losses reached billions of dollars. The damages caused by another raid involving the NotPetya strain as of June 2017 were in the billions as well. Unlike WannaCry, this one provided no recovery options at all and was most likely a state-funded wave of sabotage.
Over the course of 2018-2019, the unnerving ransomware phenomenon shifted from the approach of “casting a wide net” toward a focus on targeting specific high-profile entities such as businesses, healthcare organizations, educational institutions, and governments. Malicious actors conduct reconnaissance prior to an attack to find weak links in the would-be victim’s IT network along with the personnel’s pain points. Then, spear-phishing or RDP (remote desktop protocol) hacks come into play so that the crooks gain a foothold in the environment and execute the malicious data encryption process.
The infection called Sodinokibi dominates the environment of targeted ransomware at this point. Discovered in April 2019, it has compromised dozens of enterprises and local governments, including 22 municipalities in Texas. The ransom demands reach millions of dollars, as was the case in the Texas incident when the malefactors asked for $2.5 million.
Ryuk ransomware is one more strain that zeroes in on large computer networks rather than end-users. The latest newsmaking onslaught took place in mid-December 2019. The predatory program compromised the computer networks of New Orleans, Louisiana, coercing the local officials to shut down the city’s servers and declare a state of emergency.
Obviously, the drop in the number of ransomware attacks is just an evolutionary tweak of this cybercrime model. The mainstream threats have been superseded by advanced nasties whose distributors are very selective in terms of the victims. Some worthwhile statistics reflecting the state of this issue are as follows:
- According to Symantec, enterprise ransomware saw a 12% increase and mobile ransomware grew by 33% in 2018.
- In July 2017 - June 2018, a total of 257 new ransomware lineages splashed onto the scene, as per a report by Secureworks.
- About 70% of all security incidents targeting educational entities in 2018 involved ransomware (ENISA Threat Landscape Report 2018 mentioned above).
- Ransomware accounts for 64% of cyber-attacks against industrial control systems.
- During 2018, 65% of reported ransomware arrived via email spam.
- A whopping 93% of phishing emails tried to deliver ransomware.
Whereas Windows PCs are the primary targets, Macs aren’t safe either. In 2016, a sample of Mac-only ransomware called KeRanger made its debut. It can actually encrypt data on hosts and trigger a full-fledged extortion chain. Another pest called MacRansom, which surfaced in 2017, is even backed by a RaaS (Ransomware-as-a-Service) affiliate platform. The good news for Mac fans is that such campaigns are extremely rare so far, but this could change anytime.
Obviously, ransomware is still a threat. To top it off, the number of organizations that end up paying the ransoms is growing. According to Imperva, 45% of the infected companies succumbed to extortionists’ demands in 2019 – up from 38.7% the previous year. Under the circumstances, data backups continue to be the most effective way of mitigating the damage incurred in a ransomware raid.
Cryptojacking is the new black
With the cryptocurrency industry booming this decade, cybercriminals chose not to miss the hype train. Cryptojacking, a term denoting malicious exploitation of computers or web servers to mine coins, has been on a dramatic rise since ransomware started slowing down. The overlapping of these two trends suggests that some players who used to be in the ransomware business shifted to the more surreptitious model of raking in profits.
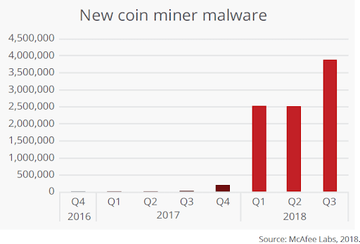
According to McAfee Labs Threats Report, there was a mind-blowing 4,000% increase in the quantity of cryptojacking events in 2018. The common technique is to lace a malware payload with a variant of the XMRig Monero miner and deposit the malicious cocktail onto computers without the users’ awareness.
Although most cryptocurrencies, including Monero and Bitcoin, have lost a good deal of their value since the 2017 peak, stealth coin mining continues to lure criminals and is still a serious concern. In a few incidents that hit the headlines in 2019, the operators of cryptojacking campaigns compromised an international airport’s computer systems, distributed a booby-trapped WordPress plugin, and used a unique worm to infect Docker virtualization containers constituting large enterprise networks.
Obviously, the crooks’ repertoire is broadening despite a decrease in the number of attacks overall. A study by ENISA (referenced above) sheds some light on the scope of the issue and the perpetrators’ earnings: in H1 2018, the threat actors made roughly $2.5 billion worth of cryptocurrencies by means of shady mining. Obviously, there is a lot of room for improvement in terms of fending off these disastrous stratagems.
Phishing takes the world by storm
Email-borne social engineering has seen a tremendous increase by the end of the 2010s. Con artists are becoming more proficient in designing phishing emails that look credible enough to dupe recipients into opening them and following the fraudulent recommendations. The scammers’ objectives range from wheedling out sensitive credentials to distributing malicious code such as ransomware, coin miners, and info-stealing Trojans. Here are some stats that will give you an idea of how serious the problem is:
- According to Microsoft Security Intelligence Report Volume 24, the number of reported phishing attempts went up 250% in 2018, reaching 470 billion such emails per month.
- 35% of businesses consider phishing to be the top threat (EY Global Information Security Survey 2018-2019).
- Users targeted in the United States end up opening 30% of phishing emails, and 12% of them click on dangerous links or embedded files, says Verizon in their 2019 Data Breach Investigations Report.
- ENISA analysts found that phishing attacks zeroing in on social media users grew by 300% in 2017.
- According to the FBI’s 2018 Internet Crime Report, the total losses incurred by businesses due to phishing amounted to $1.2 billion during the year.
A peculiar technique that’s gaining momentum is called business email compromise (BEC). These hoaxes focus on compromising top-level executives in an organization. Researchers at Proofpoint recorded 476% more BEC scams in 2018 versus 2017. Obviously, crooks are rethinking their tactics to go after big prey.
DDoS attacks maximizing their reach and power
Distributed denial of service is an old school method of knocking an electronic network offline. Whereas the objectives used to be mostly isolated to outright disruption and ideological motives, this phenomenon has assumed extra flavors in the course of its evolution. The newest tactic is what’s called the ransom DDoS, where cybercriminals render a target service inaccessible and demand money for discontinuing the attack and reverting to normal operation. To add insult to injury, the amplitude and sophistication of these raids have grown considerably over the years. Some of the recent facts regarding this issue are as follows:
- The monthly number of DDoS attacks recorded around the world exceeds 400,000, says Calyptix Security.
- According to a report by Corero, the number of incursions with an amplitude of more than 10Gbps doubled in 2017.
- Telco industry was a sector hit the hardest in H1 2018 (800,000 reported attacks).
- The average DDoS attack lasted for 318 minutes in 2017 (ENISA).
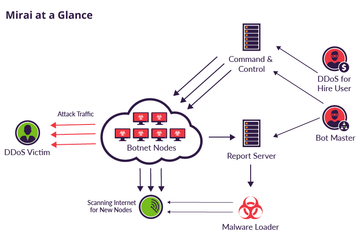
IoT botnets such as Mirai have been a growingly serious concern since about 2016. Notoriously insecure connected devices like smart home appliances are low-hanging fruit for attackers. By easily infecting millions of Internet-enabled gadgets, botnet operators can exploit their combined traffic capacity to fire hefty DDoS onslaughts. This was the case with the 2016 massive cyber-attack targeting Dyn, a major DNS provider.
Windows and Mac adware going big
Also referred to as potentially unwanted applications (PUAs), adware is a collective term denoting malicious code that displays unsolicited ads or hijacks web browsers without the victims’ consent to endorse junk web services. Although these culprits aren’t particularly dangerous, they are extremely annoying and increasingly stubborn when it comes to removal.
According to the 2019 State of Malware report by Malwarebytes Labs, adware is the top threat on the list of consumer detections worldwide. Its quantitative domination stems from the fusion of high moneymaking potential through imposed advertising and the relatively low severity of these infections allowing the campaigns to stay in the limelight of more aggressive counterparts.

Whereas Windows PCs are the usual targets in this context, Mac adware is a rapidly swelling blot on the threat map. It is the second most detected form of offending code in the world across all platforms, says a recent study. Although the data set is restricted to users of a particular security solution, these unsettling findings speak volumes about the emerging menace.
Adware tailor-made for macOS took a major leap with several concurrent traffic redistribution campaigns. One of them revolves around hijacking web browsers and redirecting them to SearchMarquis.com and SearchBaron.com sites. Both are components of a shadowy monetization scheme in which crooks generate profit by inconspicuously tunneling victims’ Internet traffic through a series of ad networks.
This plot also has a flavor of feigned legitimacy. Each instance of the browser rerouting lands users at Bing.com. At first blush, this feels like a glitch with no malicious implications behind it. However, adware makers abuse the trusted search engine to smokescreen their misconduct. A similar quirk holds true for the Yahoo redirect virus whose operators mishandle the Yahoo Hosted Search (YHS) platform as a curtain for skewing infected Mac users’ browser settings and web surfing patterns.
What sets these adware campaigns apart from others is the massive scale of attack and extraordinary persistence of the underlying code. The latter is largely due to the addition of a rogue device profile. This entity crops up on a Mac without the user’s consent and controls web browsing activities down the line.
Mobile malware on the rise
A smartphone is the best thing since sliced bread, no doubt. It’s also a Pandora’s box of exploitation opportunities, though, and cybercriminals appear to have found the right key to break it open. The ubiquity of these devices has caused mobile malware to grow exponentially – here are some statistics showing the current state of things:
- According to a white paper by RSA Security, more than 60% of online fraud involves mobile devices and 80% of these threats emanate from mobile apps rather than browsers.
- Symantec cybersecurity firm claims to have blocked approximately 10,500 dodgy mobile apps per day in 2018.
- As per Mobile Security Index (MSI) Report by Verizon, a third of surveyed organizations dealt with serious security incidents involving a mobile device in 2018.
- ThreatMetrix estimated the scope of mobile fraud in H1 2018 at 150 million attacks, with a 24% year-over-year increase globally (44% YOY growth in the United States).
As more and more digital transactions originate from smartphones and tablets, the soaring of mobile fraud will continue. Since malicious apps are the main source of the issue, threat actors are constantly coming up with new ways to get around the filters of popular application marketplaces such as Google Play and Apple’s App Store. The numbers above show that these sketchy efforts are quite successful.
Cybercrime got a boost during COVID-19 crisis
Pandemic, the resulting infodemic, and cybercrime are overlapping. Unsurprisingly, the coronavirus outbreak has become an impetus for opportunistic threat actors to ramp up their filthy efforts. 2020 saw a massive increase in phishing scams that harness users’ fears of the disease to wheedle out credit card details and other personally identifiable data.
Another trend is the escalating distribution of info-stealing malware such as AZORult whose goal is to get hold of victims’ Bitcoin wallets and passwords. Ransomware operators aren’t on the sidelines of the boom either, capitalizing heavily on double-extortion based on a mix of encryption and data theft. The worst part is that these folks keep attacking hospitals and other COVID-19 response organizations.
Because VPN and video-conferencing services are the strongholds of remote workplace implementation in the tough pandemic times, crooks are increasingly focused on finding and using vulnerabilities in these tools. By and large, cybercrime is trying to make the most of the healthcare emergency in its own wicked way.
What cyber-threats to look out for in the 2020s?
Mankind is on the threshold of a new decade which is going to pave the way for amazing and groundbreaking technologies and, you guessed it, more vectors of cyber-attacks. Some of the old threats will undoubtedly keep making themselves felt, but the 2020s will also become a launchpad for compromise techniques we haven’t seen before. Here are the main predictions of what to expect in the near future security-wise:
1. Targeted ransomware will thrive
There is no evidence indicating a decline of ransomware whose operators pinpoint their targets. The likes of Sodinokibi will continue to spread mayhem in the enterprise environment, for the most part. The average size of the ransom is going to grow, given the high-profile victims in the extortionists’ spotlight (healthcare facilities, city networks, international corporations, etc.). Meanwhile, ransomware will be a lesser threat to individual users.
2. 5G security challenges are imminent
The global deployment of 5G networks will call forth a whole new security paradigm, and the risks have yet to be assessed. According to a recent EU report, the biggest menace is about supplier monopoly, which means entire countries will have to deal with a single point of failure (SPOF) problem. The additional concerns include crude maintenance practices, lack of proper software update management, vague security standards, and shortage of well-trained personnel in this niche. Cloud computing that will increasingly rely on 5G is one more area that needs an overhaul in terms of security.
3. Deepfakes gaining traction among crooks
Frauds based on the deepfake technology will turn into a new cybercrime heavyweight. This tactic is shaping up to be a huge source of blackmail and sextortion while also posing a tremendous risk to celebrities and politicians whose reputation can be ruined by a fabricated video in the blink of an eye. For instance, experts believe threat actors will try to leverage deepfakes to play a role in the 2020 U.S. presidential election. The good news is that Microsoft and Facebook have teamed up to develop better mechanisms for identifying deepfakes. Hopefully, such initiatives will work out sometime soon.
4. IoT crime will flourish
Despite numerous security incidents in the IoT realm, the manufacturers of connected devices appear to be still sacrificing the defenses in favor of usability. As a result, a plethora of home automation systems and other Internet-enabled entities are ridiculously easy to compromise, and this isn’t likely to change anytime soon. Tons of smart appliances out there lack proper firmware update mechanisms and therefore don’t get critical vulnerabilities patched quickly enough. In the aftermath of this reckless vendor race aimed at inflating the customer base whatever it takes, IoT malware such as Mirai and VPNFilter will continue to spread like wildfire, fueling botnets and putting users’ privacy at stake.
5. Data breaches will reach new heights
The cloud is where the bulk of data resides these days, and the same will definitely hold true in the 2020s. For the average end-user and enterprise, this is a blessing that makes things easier. However, this paradigm gives cybercrooks a goldmine of opportunities as well. A minor misconfiguration can be a springboard for hackers to access the cloud and steal sensitive information belonging to millions of users in one hit. When it comes to organizations, a common forecast is that a quarter of all breaches will occur outside the perimeter. This is an outcome of the increasingly popular BYOD (bring your own device) approach favored by businesses and a growing number of employees working outside the office.
6. Mac malware is seen as a major concern going forward
Adware and scareware plaguing Mac computers will escalate. This is a reasonable train of thought based on the surge of these infections in the late 2010s. Mac malware will get more evasive and harder to eradicate, with social engineering hoaxes being the primary entry point. Although many users are still skeptical about Mac antivirus tools, having an effective security solution will become the norm in this ecosystem.
7. A spike in identity theft
Stratagems that piggyback on phishing will skyrocket. Cybercrooks are refining their manipulative skills to orchestrate highly effective email hoaxes and social media scams, and this nefarious trend will be the case during the upcoming decade. Fake authentication web pages observed in modern phishing attacks are replicas of their original, with URL spoofing tricks adding an extra sense of legitimacy to the frauds.
Importantly, the present-day identify theft isn’t only about users falling for faux password requests received over email and social networks. It’s also about the ubiquity of mobile payment options. The weak link of point-of-sale transactions, especially ones completed within public Wi-Fi networks, is that a remote observer may be able to intercept confidential info. Man-in-the-middle (MITM) attacks in such scenarios will most likely evolve, too.
Final thoughts
With so many awesome technological advances at everyone’s fingertips, there are also plenty of risks stemming from them. Cybercrime of the new decade will throw down the gauntlet we should be prepared to take up. It’s hard to foresee all the threats that will surface in the 2020s, but masterminding countermeasures for the obvious ones is half the battle.