Learn how to get rid of the Yahoo redirect virus on Mac and stop recurrent unauthorized traffic forwarding in Safari and other browsers on a Mac computer.
Update:
| Threat Profile | |
|---|---|
| Name | Yahoo redirect virus |
| Category | Mac browser hijacker, redirect virus, PUA |
| Related Domains | Search[random]-a.akamaihd.net, default[random]-a.akamaihd.net, lkysearchds[random]-a.akamaihd.net, search.safefinder.com, search.safefinderformac.com, search.anysearchmanager.com, search.chill-tab.com, search.searchpulse.net, search.tapufind.com, searchmine.net, feed.chunckapp.com, goto.searchproonline.com |
| Symptoms | Redirects web browser on Mac to Yahoo via third-party websites, adds sponsored content to search results, causes system slowdown, resists regular removal |
| Distribution Techniques | Fake Adobe Flash Player update popups, malware-riddled bundles, spam |
| Severity Level | Medium |
| Damage | Unwanted changes of custom browsing settings, privacy issues due to Internet activity tracking, search redirects, ads above the fold |
| Removal | Scan your Mac with Combo Cleaner to detect all files related to the browser hijacker. Use the tool to remove the infection if found. |
What is Yahoo Search redirect virus?
When the prerogative of unimpeded web surfing slips out of one’s hands, things quickly get intolerable. In this scenario, doing a search via preferred service or simply launching a browser of choice will return a site the user doesn’t expect to see. If this is the case, the victims should look for malicious code that’s implementing this whole stratagem behind their back. When it comes to Mac computers, there are numerous marginal browser hijackers that never reach sizeable distribution volumes, but there are also major campaigns that last for years and span thousands of machines. The latter holds true for the Yahoo redirect virus, a plague whose prevalence demonstrates how important it is to stick with reasonable online hygiene. The main symptom of this incursion is an annoying web traffic rerouting activity, with the resulting page being search.yahoo.com.
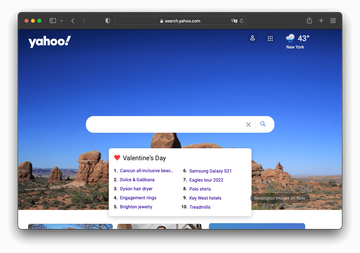
At this point, many readers will probably start wondering why the above-mentioned legit search engine is flagged malicious. As a matter of fact, it’s not – otherwise, the categorization is an utter misconception. Instead, the entire problem is about a perpetrating app that literally enslaves one’s web browser and forwards the bulk of the Internet surfing routine to Yahoo. Online traffic funneling from unique hosts is an extremely valuable asset nowadays, and the cybercrooks have contrived an intricate model to harness and monetize it in their very own, nefarious way. The thing is, before a victim ends up on the reputable Internet giant in question as a result of the hijack, they get routed via a number of intermediary domains, and these hits actually count in the dodgy traffic monetization platform.
The Yahoo redirect virus may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.Malicious apps redirecting to Yahoo
There are several dubious services operating under the wide umbrella of the generic Yahoo Search redirect campaign. Most of them are backed by potentially unwanted apps (PUAs) that claim to enhance Mac users’ web surfing experience but actually turn it upside down. Here are a few examples of these mainstream adware strains:
- Safe Finder (search.safefinder.com, search.safefinderformac.com);
- Any Search Manager (search.anysearchmanager.com);
- SearchMine (searchmine.net);
- Search Pulse; (search.searchpulse.net);
- TapuFind (search.tapufind.com);
- Chill Tab (search.chill-tab.com);
- Kuklorest (search.kuklorest.com);
- Shroomcourt (search.shroomcourt.com);
- Smokyashan; (search.smokyashan.com);
- Feed Chunk App (feed.chunckapp.com);
- Search Pro (goto.searchproonline.com).
All of them force hits to their landing pages camouflaged as search providers. Predictably enough, though, none has a real proprietary information lookup feature, primitively redirecting every query to Yahoo. In most instances of this unauthorized redistribution of Internet traffic, there are intermediary URLs resolved en route to the destination. A common example is a.akamaihd.net domain name prepended by lkysearchds[random digits] or similar random-looking string. Another long-standing variant that may briefly show up during the redirect is search3.searchgenieo.com. The logic behind inserting in-between pages of that sort is to bolster the campaign with statistics gathering and black hat SEO activities that help the malefactors propel their shadowy business.

In many cases, the problem co-occurs with covert installation of an adware app from the AdLoad family, also known as Bundlore. This isn’t a coincidence, as this strain is known to tweak its victims’ web browsing defaults. A distinguishing hallmark of this software is its icon whose design includes a magnifying glass symbol. One more pattern is a bizarre name consisting of two vaguely related terms, for instance, CommonResearch, EmergingZip, OpenForMac, and AlgorithmFormula. The app may take the exploitation further by imposing rogue proxy settings to cut off regular connectivity. If so, Yahoo Search is going to be the only site that opens in a web browser, and any attempts to visit other pages are accompanied by error messages saying that the connection is not available.
To partially re-enable Internet access, those affected should go to System Preferences, select “Network”, click the “Advanced” button, pick “Proxies”, and uncheck any activated protocols in there. Although this won’t uninstall the adware, it allows victims to browse other sites, search the web for advice, and download cleaning tools if necessary.
Yahoo redirect virus infection chain
The aggressive phase of the raid is preceded by a furtive infiltration of the underlying malware into the Mac. This is typically an upshot of a bundling technique heavily used by both decent and unscrupulous software developers to cross-promote certain apps coming as part of a bigger installation package. Users don’t read the fine print these days, and that could be a source of serious quandaries.
The Yahoo redirect virus may lurk in multi-pronged setup clients for what appears to be a legit software update or some useful free tool, such as a media downloader or video game. For instance, the fake Adobe Flash Player update popups are known to spread this electronic malady. The express installation option, which is most people’s favorite due to the ease of the setup, will silently pull in the culprit. The next thing you know, Safari, Chrome or Firefox on the Mac will start acting up badly. By the way, with Adobe officially ending support and distribution of their famous and notoriously unsafe solution from December 31, 2020 onward, Mac adware operators are gradually adjusting their schemes to this move. The clever shift is backed by an escalating campaign that disseminates browser hijackers such as the Yahoo redirect virus under the guise of Flash Player Uninstaller popups. This demonstrates bad actors’ agility combined with adaptability to new circumstances.
Once the contamination has taken place on a macOS or Mac OS X system, the redirects to search.yahoo.com are usually triggered according to a specific pattern rather than haphazardly. The victims report their Google searches being forcibly diverted to Yahoo. Simply opening one’s preferred browser is another trigger for the predicament. All attempts to sort it out by defining correct URLs for the corresponding custom browsing settings are futile – the wrong values shortly reappear in there due to the persistent malware activity. Sometimes the defaults may even be right, with the interference taking place at a different layer of the host operating system.
A persevering threat
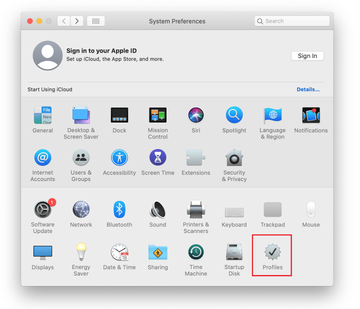
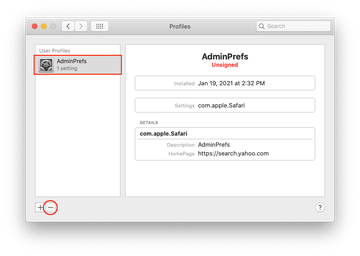
When it comes to persistence, the Yahoo redirect virus goes in lockstep with all potent Mac adware lineages. Once it crops up in a system, it enhances the attack chain by adding a fraudulent configuration profile. This rogue entry is listed in the sidebar of the Profiles page under System Preferences. Its goal is to enforce certain behaviors of different macOS components, including the installed browsers. This way, the malicious code runs with elevated privileges and its impact is impossible to reverse unless the evil profile is erased.
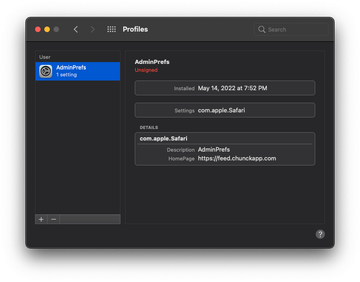
Speaking of which, the only thing that may hamper this stage of the cleanup is that the name of the offending object varies from case to case and therefore it could be hard to pinpoint. Therefore, the victims should follow their intuition and look for a profile that looks out of place. An entry named AresLookup or AdminPrefs is an example of a profile created by Yahoo redirect virus as part of the attack (see image above). It manages browser settings to the extent where manual modifications are disabled. An extra symptom is the emergence of recurrent popup dialogs asking the victim to grant the profile network access permission. Selecting the suspect and clicking on the minus icon is half the battle and will pave the way to successful removal of the infection.
One more tier of persistence and at the same time a telltale symptom of this infection is the onset of a new enterprise policy in the web browser. For instance, most victims encounter a message that says “Managed by your organization” in the Google Chrome settings pull-down menu on Mac. This is another manifestation of legitimate features being mishandled in malware campaigns. Under the circumstances, the cure should synchronously cover several areas of the affected system, as shown in the cleanup part below.
Yahoo Search redirect virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
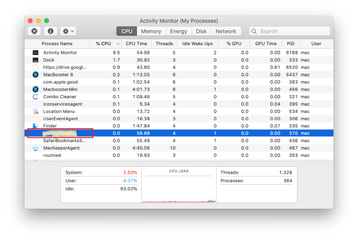
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
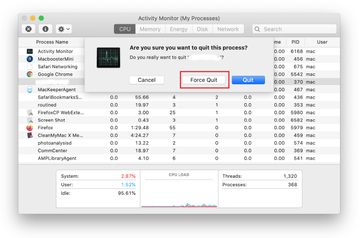
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
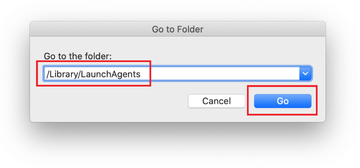
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
Examine the contents of the LaunchAgents folder for dubious-looking items. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
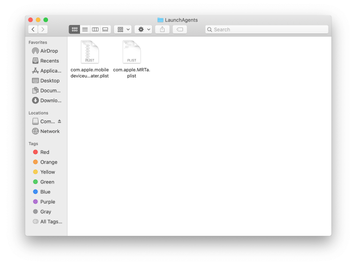
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
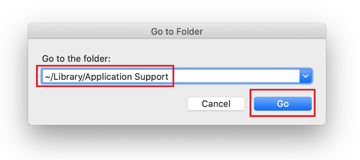
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are SystemSpecial, ProgressSite, and IdeaShared.
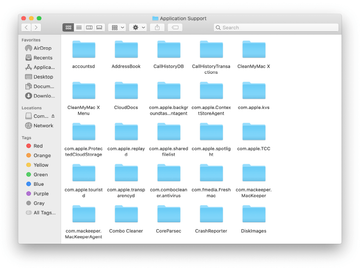
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
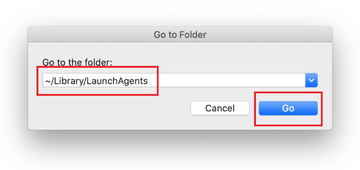
The system will display LaunchAgents residing in the current user’s Home directory. Look for dodgy items related to Yahoo redirect virus (see logic highlighted in subsections above) and drag the suspects to the Trash.
Type /Library/LaunchDaemons in the Go to Folder search field.
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
Find the entry for an app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

Expand the Apple menu and select System Preferences.
Proceed to Users & Groups and click on the Login Items tab.
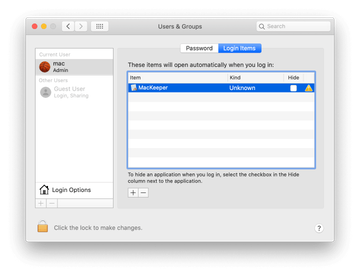
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include AresLookup, TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of Yahoo redirect virus in web browser on Mac
To begin with, the web browser settings taken over by the Yahoo redirect virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Remove Yahoo redirect virus from Safari
Open the browser and go to Safari menu. Select Preferences in the drop-down list.
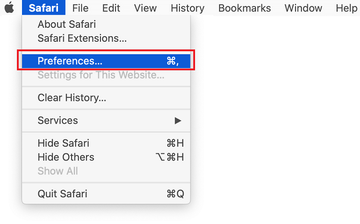
Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
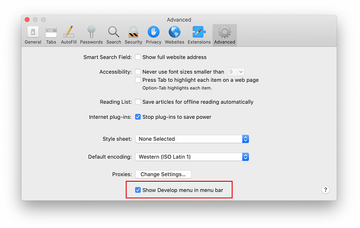
Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
Now select History in the Safari menu and click on Clear History in the drop-down list.
Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
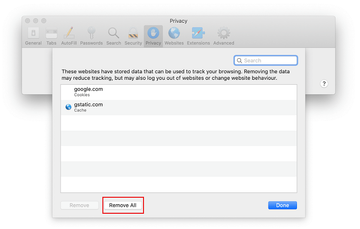
Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
Restart Safari
- Remove Yahoo redirect in Google Chrome
Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
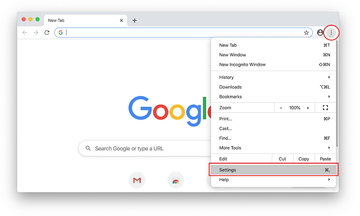
When on the Settings pane, select Advanced
Scroll down to the Reset settings section.
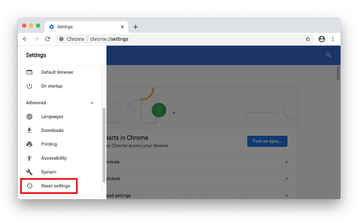
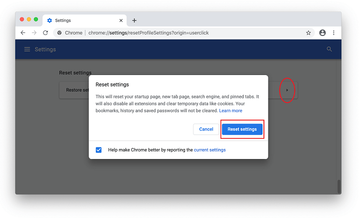
Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Remove Yahoo redirect from Mozilla Firefox
Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
When on the Troubleshooting Information screen, click on the Refresh Firefox button.
Confirm the intended changes and restart Firefox.
Get rid of Yahoo redirect virus Mac using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Yahoo redirect virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Yahoo redirect issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
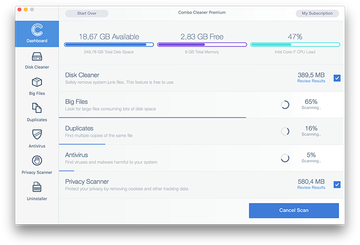
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Yahoo redirect threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
FAQ
How do I stop Yahoo from hijacking my browser in Safari?
The only effective way to stop the browser hijack in its tracks is to eliminate the root cause, that is, a piece of malware that’s wreaking havoc with your Internet preferences. Reverting to the correct Safari settings is going to be an unsuccessful move as long as the infection stays up and running inside your Mac, because it will re-enable the traffic-tweaking triggers over and over.
Another quirk of the virus is that the rogue landing page may not show up in the default search engine or homepage area under Safari preferences. Despite this, every Google search will be returning Yahoo in a recurrent fashion. The most likely reason is that the culprit invokes a covert redirect script, which complicates the fix considerably.
That being said, to prevent Safari from being redirected to Yahoo you need to leverage a two-step troubleshooting procedure. First, uninstall the malicious app – you can follow the manual guide above to do it or resort to an automatic cleaning utility.
Then, check Safari for extensions you don’t remember adding and remove the unfamiliar ones. Also, make sure your default search provider setting is correct. If none of that helps, use the steps listed in the tutorial to delete Internet cache and other data stored by websites.
How do I get rid of Yahoo search engine on Mac?
As outlined in the previous answer, browser troubleshooting alone is a no-go unless you remove the underlying virus first. You should stick to the cleanup walkthrough covered in the article to make the infection vanish.
Importantly, be sure to peek into your Login Items by going to System Preferences – Accounts. In many cases, the victims have a rogue entry named ‘Mac Mechanic’ in there – if found, delete it right away. This is a fake system utility that may have promoted the Yahoo redirect virus into your Mac in the first place.
In order to sort out the search engine replacement issue, go to your browser’s preferences screen and ascertain that the right search provider is selected as the default one. Additionally, disable suspicious browser extensions if spotted. A more thoroughgoing fix is to reset the affected web browser to its original state and redefine your custom settings afterwards.
How do I switch from Yahoo to Google on my MacBook Air/Pro?
If you are faced with a virus scenario, switching from Yahoo to Google as your preferred search engine is a much more complex procedure than tweaking these settings manually. You need to additionally get around the malicious app’s interference so that the benign changes take effect for good.
Here are the components and paths on your MacBook Air or MacBook Pro to scour for the potentially unwanted program: Activity Monitor, Applications, and Login Items. Anything that clearly doesn’t belong there should be deleted.
It’s not until the redirect virus has been removed from your Mac that you can get down to rectifying the browser settings. See the guide’s section called ‘Get rid of search.yahoo.com redirect virus in web browser on Mac’ for the appropriate instructions. Having completed these steps, go ahead and assign Google as your default search engine in the browser of choice.
Is search Powered by Yahoo a virus?
Not necessarily. It depends on the methods leveraged to promote such a web service. Obviously, it takes enormous efforts and human resources, plus a lot of time to create and maintain a fully-fledged search engine. Only major companies can afford it. Meanwhile, the entities that wish to include a search feature in their online service can choose to outsource the functionality to Yahoo.
However, malware developers are known to abuse the Powered by Yahoo framework on a large scale. Their potentially unwanted apps forcibly change users’ Internet preferences so that the browser returns Yahoo search results combined with ads that normally don’t belong there. This explains why such an approach tends to call forth malicious inferences. The truth is that the inscription “Powered by Yahoo” becomes a sort of red herring in these traffic monetization campaigns.
Why does my search engine keep going to Yahoo on Mac?
This shouldn’t be happening unless you knowingly specify it as your default search provider. That’s how it’s supposed to be in an ideal world. In real life, though, a web browser may be subdued by a virus that drives traffic to Yahoo without the user’s blessing. Simply put, if you haven’t changed your web surfing preferences recently but keep going to Yahoo after entering searches in the address bar, a strain of malicious code is to blame.
The Yahoo redirect threat prowls its way into Macs via combinations of several programs masqueraded as single-app installers. Such a bundle is designed specifically to hush up its true composition. Unsurprisingly, most users go with the flow and accept the “Recommended” setup mode, only to discover shortly that Safari, Chrome, or Firefox repeatedly resolves Yahoo instead of Google or another service of choice.
Zooming back into the root cause for this weird browser activity, it usually starts with the user’s blunder. Authorizing an instance of software installation without exploring what else might be inside is risky business. It leads to the infiltration of a Mac virus that reorganizes your default Internet settings, adds a configuration profile to keep the rogue settings in effect, and redirects to Yahoo via auxiliary URLs hooked into a massive traffic monetization venture.
