Find out how the Search Pulse virus affects a Mac, what loopholes it exploits to propagate, and how to get rid of the annoying browser redirect activity.
Update:
| Threat Profile | |
|---|---|
| Name | Search Pulse (home.searchpulse.net) browser hijacker |
| Category | Mac adware, browser hijacker, redirect virus |
| Detection | Avira: PUA/OSX.SearchProtect.Q, F-Secure: PotentialRisk.PUA/OSX.SearchProtect, Qihoo-360: PotentialRisk.PUA/OSX.SearchProtect |
| Related domains | search.searchpulse.net, lkysearchds1122-a.akamaihd.net |
| Symptoms | Redirects web browser to third-party websites such as home.searchpulse.net, adds sponsored content to search results, causes system slowdown, resists regular removal |
| Distribution Techniques | Malware-riddled app bundles, fake Adobe Flash Player update popups, spam |
| Severity Level | Medium |
| Damage | Unwanted changes of custom browsing settings, privacy issues due to Internet activity tracking, search redirects, redundant ads |
| Removal | Scan your Mac with Combo Cleaner to detect all files related to the browser hijacker. Use the tool to remove the infection if found. |
Finding relevant information on any subject is a piece of cake these days – all it takes is typing the query in a search engine of choice. Which search engine? It’s a matter of personal preferences, habits and perception of convenience. Sometimes, though, users need to see and compare data returned by different services to get the big picture, and that’s the catch that the authors of Search Pulse app are cashing in on. They boil their marketing down to the following perk: people can visit one page, select a search provider out of three available options there, and get the results on the same page without having to use each service separately.
Sounds nifty, but there is a major pitfall in the implementation of this whole idea. The Search Pulse applet penetrates into Mac computers uninvited and it forcibly gives the browsing settings an overhaul without asking for the admin’s consent about driving traffic to home.searchpulse.net. Normal software doesn’t act this way, which explains why lots of users flag this one as a PUP (potentially unwanted program) or even a virus.
Rather than go the route of an informed decision, the penetration of the Search Pulse virus into a Mac resembles a trespass bypassing the victim’s approval. The most likely technique is based on bundling, a software distribution practice that promotes a package of applications as an appendage to the one the user is aware of. In plain words, harmful entities may accompany benign programs during installation in such a way that the targeted person stays clueless about the stratagem until the culprit shows its fangs. A mainstream method employed by the operators of this particular adware campaign comes down to fake Adobe Flash Player updates promoted through popups on breached or malicious web pages. This is exactly what happens in the Search Pulse intrusion scenario. Thankfully, it’s a no-brainer to avoid this infection vector – just choosing “Custom” in the install options will allow for exploring the bundle and deselecting the unwanted items. But, most Mac users go with the flow and never peek beyond the default setup, only to get infected and deal with the consequences.
Search Pulse may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
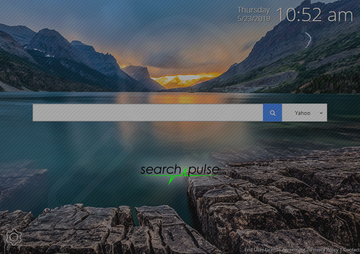
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.When inside, the Search Pulse virus instantly modifies the browser configuration so that the traffic is repeatedly forwarded to home.searchpulse.net, or less often to search.searchpulse.net. In most cases, the pest replaces the admin’s homepage, search engine and new tab settings with the above value. As a result, Safari, Chrome and Firefox will be redirected to the rogue landing page over and over. The site itself has minimalist design. It contains a search bar with the search engine select dropdown next to it, allowing the visitor to choose from Google, Yahoo, and Bing. There’s additionally a current time widget at the top and an option at the bottom for setting a different background. The general impression from the service might be okay, but the very “peculiar” way Search Pulse spreads is a giveaway.
This threat has gained notoriety for its stubborn behavior. Normally, if a Mac user wants to change their browsing defaults, all it takes is going to the settings and selecting the preferred service from a list or typing in the correct URL. In the case of the Search Pulse virus, things are way more complicated than that. It configures the affected browser to resolve a rogue site once launched and also whenever the victim opens a new tab. Strangely enough, the unwanted setting isn’t searchpulse.net proper. Instead, it’s usually lkysearchds1122-a.akamaihd.net or similar-looking domain, with the address being followed by a long string of alphanumeric campaign IDs. The dodgy attributes constituting this site’s URL invoke a further redirect to search.searchpulse.net, and from there to Yahoo most of the time.
The above-mentioned persistence of this whole misconfiguration is all about the fact that the appropriate settings fields are grayed out and inactive, and therefore the victim cannot replace them with the right values easily. This is an outcome of a whole separate vector of Search Pulse’s tactic. It creates a new user profile in the host Mac without asking for the admin’s approval, which allows the pest to impose arbitrary system parameters while providing no simple way to override them. In most attack instances, the name of this entry showing up in the Profiles interface under System Preferences is techSignalSearch. Users should keep in mind that this should be an empty list unless they add anything there or the Mac is part of a network managed by an organization. If none of these conditions is the case, then the occurrence is a telltale sign of adware activity and the object should be deleted without a second thought. It’s also noteworthy that the attack is accompanied by a peculiar malicious process running in the background. This executable is visible in the Activity Monitor. In many recent cases, it’s called “productevent”. Therefore, to start the fix it’s necessary to terminate this process so that it doesn’t interfere with the subsequent cleaning steps.
To top it off, the app may collect personally identifiable information about the victims and their Macs, such as visited sites, searches made, IP addresses, and other sensitive data. Unscrupulous vendors tend to retain such details and sell them to advertisers or cybercrooks. Obviously, Search Pulse doesn’t belong inside a Mac unless it was wittingly installed, which is hardly ever the case. So, if redirects to home.searchpulse.net or search.searchpulse.net are giving you a hard time, be sure to follow the steps below and remove the infection.
Search Pulse redirect virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
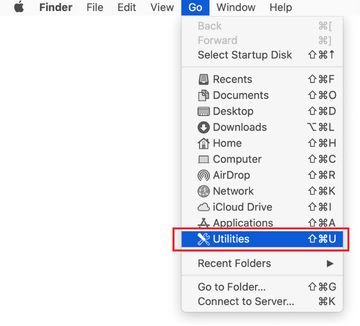
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
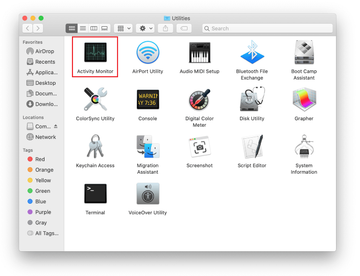
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
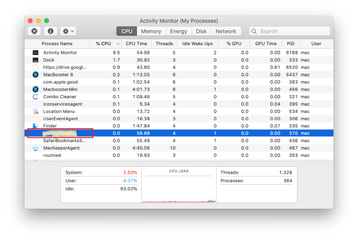
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
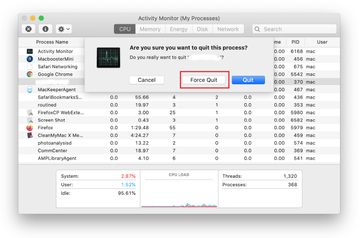
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
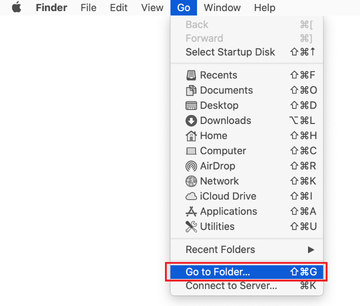
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
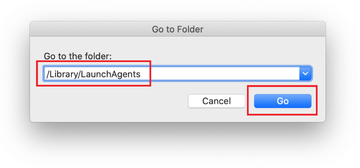
Examine the contents of the LaunchAgents folder for dubious-looking items. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
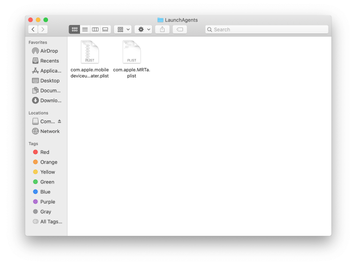
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
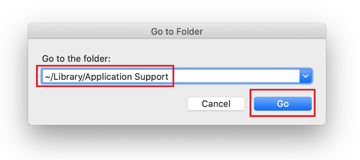
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are SystemSpecial, ProgressSite, and IdeaShared.
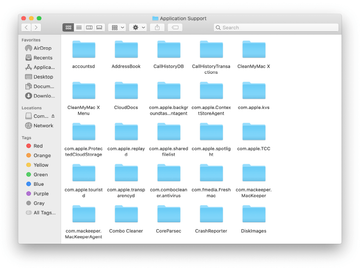
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
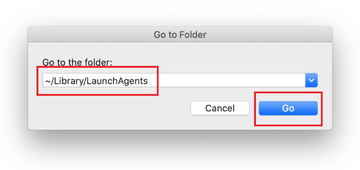
The system will display LaunchAgents residing in the current user’s Home directory. Look for dodgy items related to Search Pulse virus (see logic highlighted in subsections above) and drag the suspects to the Trash.
Type /Library/LaunchDaemons in the Go to Folder search field.
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
Find the entry for an app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

Expand the Apple menu and select System Preferences.
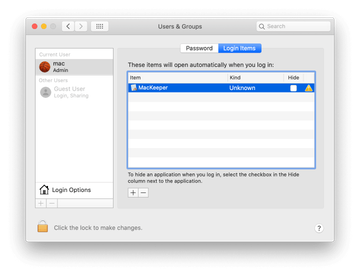
Proceed to Users & Groups and click on the Login Items tab.
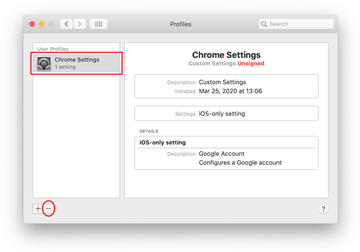
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of Search Pulse virus in web browser on Mac
To begin with, the web browser settings taken over by the Search Pulse virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Remove Search Pulse virus from Safari
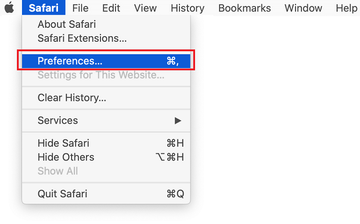
Open the browser and go to Safari menu. Select Preferences in the drop-down list.
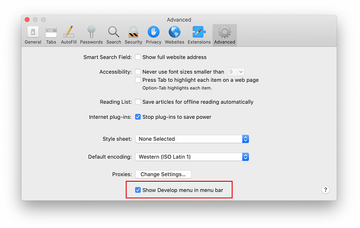
Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
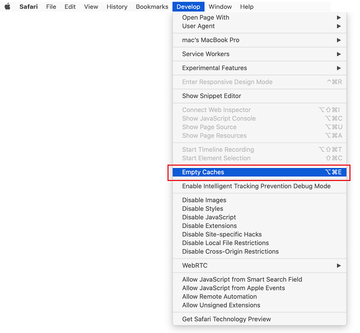
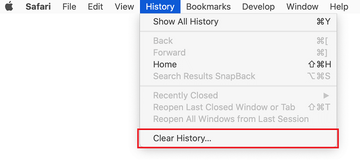
Now select History in the Safari menu and click on Clear History in the drop-down list.
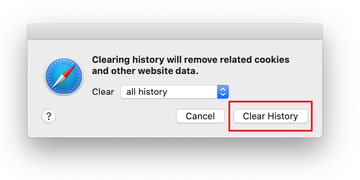
Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
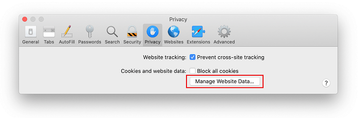
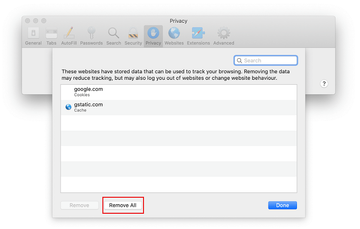
Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
Restart Safari
- Remove Search Pulse in Google Chrome
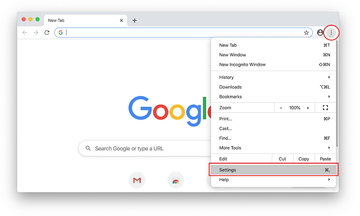
Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
When on the Settings pane, select Advanced
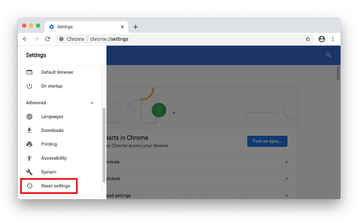
Scroll down to the Reset settings section.
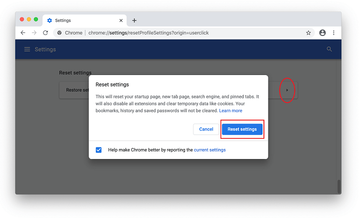
Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Remove Search Pulse from Mozilla Firefox
Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
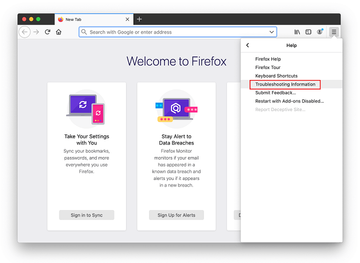
When on the Troubleshooting Information screen, click on the Refresh Firefox button.
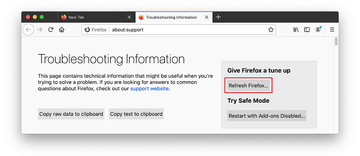
Confirm the intended changes and restart Firefox.
Get rid of Search Pulse virus using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Search Pulse virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Search Pulse issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
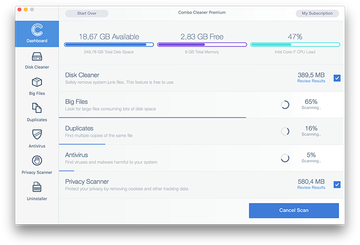
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Search Pulse threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
FAQ
What is Search Pulse on Mac?
Search Pulse is marketed as a browser extension that supposedly adds some flexibility to a Mac user’s web routine by providing a choice of the preferred search engine within a single page. Whereas these claims are true to a certain extent, the techniques used to distribute the app and the browser add-on’s behavior when it’s running on a computer are unacceptably intrusive. It changes the homepage, new tab page, and default search engine settings to home.searchpulse.net or search.searchpulse.net without asking for the admin’s permission. Furthermore, it’s impossible to undo these tweaks via the common configuration methods because the program creates a device profile re-enabling the rogue settings over and over.
Another giveaway of Search Pulse app’s foul gist is that it’s installed on a Mac by means of shady methods that have hardly anything to do with ethics. It gives the user a very faint chance to decide whether or not to install it, sneaking into hosts through multi-element freeware installers whose default mode doesn’t mention the full structure of the bundle. As a result, people don’t realize that the pest is in until the above-mentioned symptoms start manifesting themselves. So, in a nutshell, Search Pulse is an adware threat that bypasses authorization when infiltrating a Mac and takes over the unsuspecting user’s browser.
What is http://search.searchpulse.net?
It’s a landing page Search Pulse virus imposes on the infected Mac users beyond their consent and awareness. The victims keep visiting search.searchpulse.net because the underlying extension replaces their actual browsing preferences with the unwanted URL as part of the compromise. Although the unscrupulous developer’s logic is to provide bells and whistles that purportedly streamline one’s Internet search activities, the outcome is just the opposite. The user is stuck with the wrong set-up and cannot easily revert to how it was prior to the incursion. In other words, the permanent redirects to search.searchpulse.net forcibly become the norm nobody can possibly put up with.
Despite the fact that the web page in question isn’t harmful, it’s a critical link in the attack chain and therefore should be regarded as a wakeup call for thorough system cleanup from malicious code. When running a search query with this sketchy service, the victim usually ends up on Yahoo which is used as a smokescreen to hide intermediary advertising networks in plain sight. Therefore, Search Pulse operators monetize the hijacked traffic while trying to make the hoax look like a trivial misconfiguration.
How do I get rid of Search Pulse extension on Google Chrome?
Before you set out to remove Search Pulse extension on Chrome, there is a quirk of this parasite to take into account. If you open the browser’s settings pane, the ‘Search engine’ and ‘On startup’ sections will contain the following notice: “Search Pulse is controlling this setting”. It means that the core malware has added a configuration profile that disables the regular mechanisms of changing your web surfing defaults
To circumvent this hurdle, you should go to the System Preferences screen on your Mac, select Profiles, and delete the profile that ended up there behind your back. The next step is to open the Activity Monitor and stop the process used by Search Pulse virus. Its name varies, but it could be something like “productevent” or entry that doesn’t look like a benign system executable and consumes a good deal of the CPU. Then, go to Applications on your Mac and move the Search Pulse app icon to the Trash.
Now that the malicious hindrance has discontinued, you can safely remove the unwanted extension on Chrome. To do this, click the ‘Customize and control Google Chrome’ icon, click ‘More tools’ and select Extensions. Find Search Pulse on the list and click the ‘Remove’ button. Then, proceed to ‘Settings’, define the correct preferences there, and restart the browser.
How do I get rid of Search Pulse malware on Safari?
First things first, you can’t fix the Search Pulse issue on Safari by simply adhering to the traditional uninstall procedure. If you try to enter your valid Internet preferences, you’ll discover that the rogue settings are sort of hard-coded in Safari. To top it off, attempting to disable Search Pulse extension turns out to be a waste of time because it will be re-emerging off and on. The source of all these roadblocks is a malicious device profile created by the virus in the course of the initial attack. It holds sway over a number of system settings, including Safari defaults.
Back to the question, to address the Search Pulse problem on Safari you need to jab out the meddlesome configuration profile first. You can spot it under Profiles tab in your System Preferences. Select the culprit and click the ‘minus’ icon. Next, go into the Activity Monitor, find a suspicious entry under the running processes, and terminate it. Go on to Applications and drag Search Pulse to the Trash.
As the infection is no longer throwing a wrench in the works, go to Safari settings and click ‘Extensions’. Find “Search Pulse 1.0”, select it, and click ‘Uninstall’ button. Then, hit the ‘General’ tab and enter your correct homepage as well as the new tab website. Finally, click the ‘Search’ tab and choose your preferred search engine.