Search Baron virus Mac is a nuisance that diminishes the victim’s browsing experience by redirecting the traffic to Bing, so it is subject to urgent removal.
Update:
| Threat Profile | |
|---|---|
| Name | Search Baron (SearchBaron.com) browser hijacker |
| Category | Browser hijacker, redirect virus, Mac adware |
| IP | 151.139.128.10, 13.32.255.71, 204.11.56.48 |
| Related Domains | searchmarquis.com, hut.brdtxhea.xyz, mybrowser-search.com, search-location.com, searchitnow.info, searchsnow.com, search.3bamfz.com, nearbyme.io, search1.me, search-alpha.com |
| Detection | Avast: MacOS:MaxOfferDeal-I [Adw], BitDefender: Adware.MAC.Genieo.WS, ESET: A Variant Of OSX/Adware.MaxOfferDeal.N, McAfee: RDN/Generic.osx, Microsoft: Trojan:Win32/Bitrep.A, Sophos: Generic PUA PB (PUA), Symantec: OSX.Trojan.Gen |
| Symptoms | Redirects web browser to SearchBaron.com or Bing.com, adds sponsored content to search results, causes system slowdown |
| Distribution | Freeware bundles, torrents, booby-trapped software updates, misleading popup ads, spam |
| Severity Level | Medium |
| Damage | Unwanted changes of custom browsing settings, privacy issues due to Internet activity tracking, search redirects, redundant ads |
| Removal | Scan your Mac with Combo Cleaner to detect all files related to the browser hijacker. Use the tool to remove the infection if found. |
What is Search Baron redirect virus?
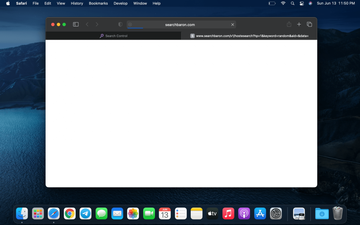
Out of all forms of malicious activity targeting Macs, a browser hijack is one of the most annoying occurrences. It results in the web surfing preferences suddenly slipping out of the user’s control, which entails forcible forwarding of the traffic to unwanted sites. Although this kind of an attack isn’t categorized as severe, it is hugely irritating and requires some thorough cleanup. Few infections from this cluster ever reach the distribution heights that the recently discovered Search Baron virus can boast. It has infiltrated numerous Mac computers over the past few days and caused some major ripples in the security circles. The pest manifests itself by taking over the custom Internet navigation settings to redistribute the victim’s web traffic. When the plagued user tries to visit a random site, the infection first forwards them to searchbaron.com, and then redirects to bing.com.
Inner workings of the Search Baron campaign
At first blush, the logic of this attack doesn’t make much sense. Why give a Mac user’s online preferences an overhaul and then take them to Bing, a legit search engine? The motivation of this shady campaign’s operators is more subtle than it may appear, though. Every time the redirect takes place, it follows a complex path involving in-between domains, such as the known-malicious searchnewworld.com site or pages hosted at AWS (Amazon Web Services) platform. A frequently reported example of the latter is searchroute-1560352588.us-west-2.elb.amazonaws.com. By the way, the use of reputable cloud networks for parking fishy web resources is a way for the cybercriminals to evade blacklisting. These sites aren’t noticeably displayed in the browser along the way, but technically, they are visited as part of the rerouting.
An extra byproduct of the Search Baron browser hijacking wave is that new malicious domains are being added to its operators’ genre down the line. One of the examples in active rotation is the hut.brdtxhea.xyz URL. Specifically, the full string is hut.brdtxhea.xyz/api/rolbng/ffind. Another shift that took place almost a year after the campaign originally exploded into the wild is that the range of cross-promoted entities has been complemented with mybrowser-search.com. As of 2023, these junk domains have been phased out and superseded by search-location.com, nearbyme.io and search1.me. These are bogus services that rely on custom search results outsourced to another engine without providing any value of their own.
The same goes for several more affiliated services that are carbon copies of each other, namely searchmarquis.com, searchitnow.info, and the latest persona called search-alpha.com that splashed onto the scene in early 2023.. Yet another garbage site, searchsnow.com, is part of this syndicate as well, but it lags far behind other spin-offs in terms of the traffic volume driven to it. The architects of this overarching scheme have built a complex network of dubious resources that keeps expanding. The malefactors are thereby skimming ad clicks on search engines and driving traffic to specific pages while making it look like the only resolved site is bing.com. This trick isn’t new, but it keeps fueling the sketchy business model based on intercepting traffic for monetization purposes.
Search Baron may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.Personal data harvesting hidden in plain sight
Search Baron browser hijack is so pesky that it overshadows another undesirable quirk of the underlying malicious app. When running on a Mac, the virus additionally keeps tabs on the victim’s online activities by unleashing a proxy module it comes equipped with. It silently monitors what sites are visited and what search queries are entered. On top of that, the infection may zero in on sensitive credentials that the user types to log into their personal web accounts, including e-banking, email, and cloud services. It also fetches details unrelated to web surfing such as macOS version as well as the list of installed applications and security tools.
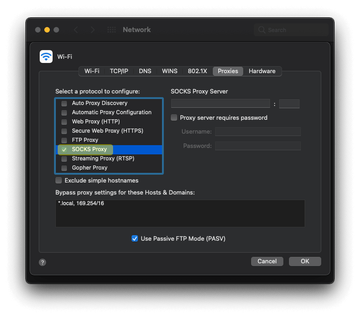
By compiling all these details, the cybercriminals behind Search Baron can form a verbose profile of the unsuspecting target and abuse this information to carry out identity theft and trustworthy-looking phishing stratagems. Chances are that the data will be sold to other threat actors, such as disreputable advertisers or high-profile hacking groups. What’s more, some of this info can be mishandled to identify weak links in the operating system version or third-party software, which is a recipe for exploiting known vulnerabilities to expand the attack surface. To check if this exploitation is underway, go to System Preferences, click Network, select Advanced, hit the Proxies tab, and examine the list of active protocols carefully. If there is a checkmark next to SOCKS Proxy or another suspicious-looking proxy, it means the virus has been quietly snooping on the web traffic.
Distribution tricks
The common entry point for the Search Baron virus incursion is bundling. This is a long-running hoax that lulls people into installing malicious programs. Some eye-catching and usually free apps promoted at various uncertified software portals are at the core of this scheme, making the users think they are lucky to get such a nifty tool at zero cost. However, the installation client may turn out to have extra items under the hood, although there are typically no mentions of this fact. As a result, the to-be prey goes ahead and clicks through the setup wizard’s panes, only to additionally install the potentially unwanted application. Mac users should finally learn the lesson: opt out of the default setup mode when installing freeware and check for unwelcome complementary objects. Reading the fine print can sometimes make one’s day, really.
Search Baron redirect virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
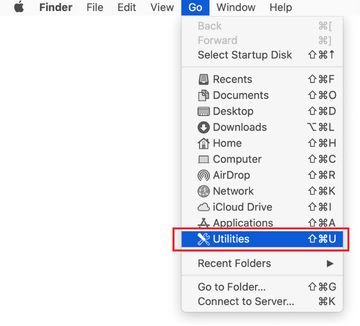
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
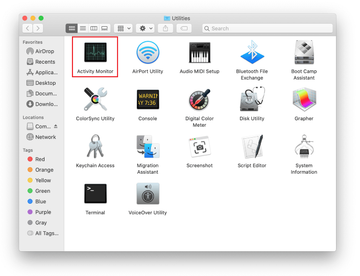
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
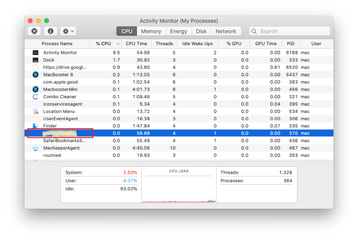
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
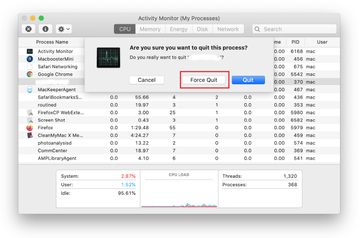
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
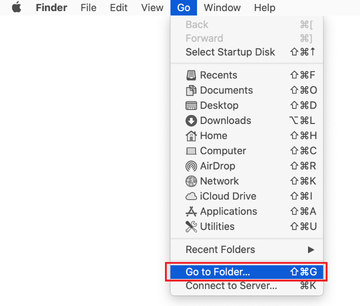
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
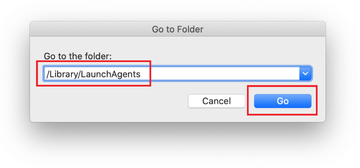
Examine the contents of the LaunchAgents folder for dubious-looking items. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
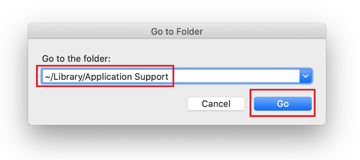
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are UtilityParze, ProgressSite, and IdeaShared.
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
The system will display LaunchAgents residing in the current user’s Home directory. Look for dodgy items related to Search Baron redirect virus (see logic highlighted in subsections above) and drag the suspects to the Trash.
Type /Library/LaunchDaemons in the Go to Folder search field.
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
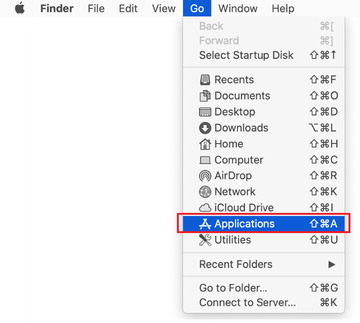
Find the entry for an app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

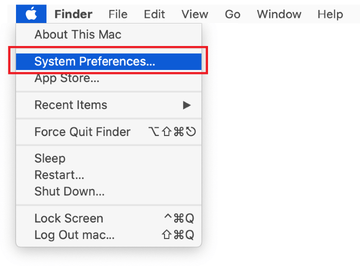
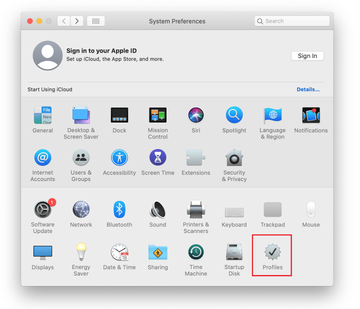
Expand the Apple menu and select System Preferences.
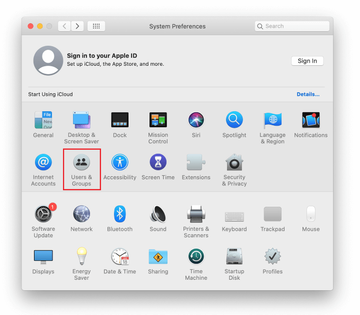
Proceed to Users & Groups and click on the Login Items tab.
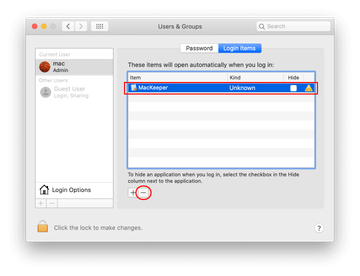
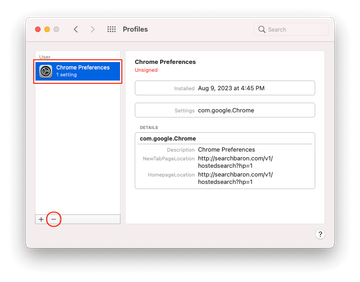
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of Search Baron virus in web browser on Mac
To begin with, the web browser settings taken over by the Search Baron virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Remove Search Baron virus from Safari
Open the browser and go to Safari menu. Select Preferences in the drop-down list.
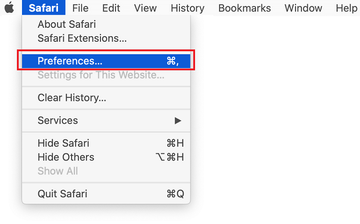
Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
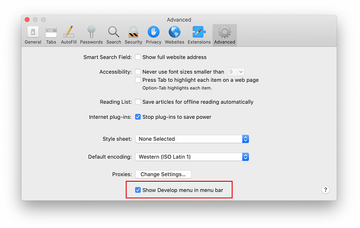
Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
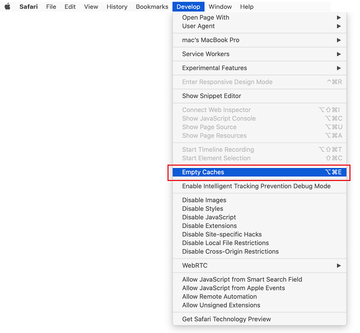
Now select History in the Safari menu and click on Clear History in the drop-down list.
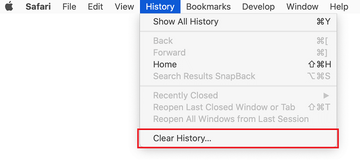
Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
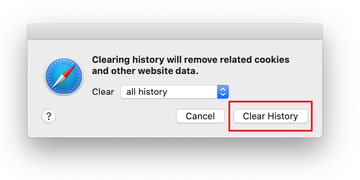
Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
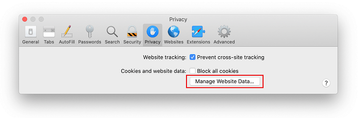
The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
Restart Safari
- Remove Search Baron in Google Chrome
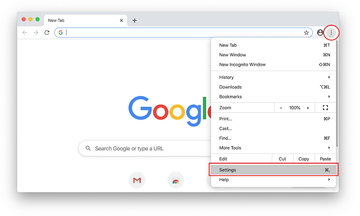
Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
When on the Settings pane, select Advanced
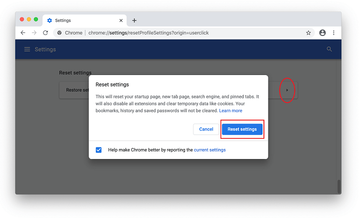
Scroll down to the Reset settings section.
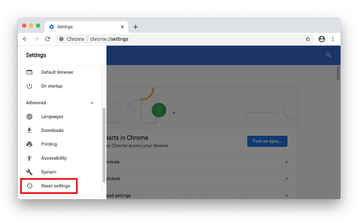
Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Remove Search Baron from Mozilla Firefox
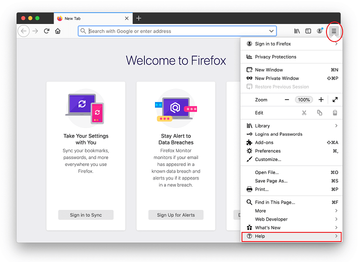
Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
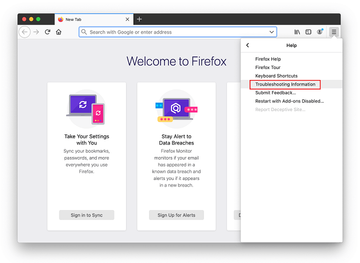
When on the Troubleshooting Information screen, click on the Refresh Firefox button.
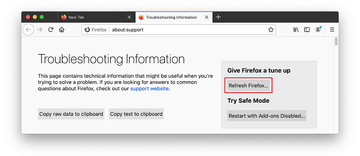
Confirm the intended changes and restart Firefox.
Get rid of Search Baron malware using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Search Baron virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Search Baron issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Search Baron threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
FAQ
How do I stop Search Baron?
The crucial prerequisite of stopping Search Baron redirects in a web browser is to get rid of the malicious app that makes this activity happen in the first place. Otherwise, even if you thoroughly clean up Safari, Chrome, or Firefox (depending on which one is affected), the hijack will keep occurring because the adware is still on board triggering its sketchy commands to re-install the rogue browser plugin.
Since this infection is preassigned to thwart regular uninstall attempts, the first thing on your to-do list is to terminate its process in the Activity Monitor. It’s not necessarily manifested as Search Baron proper, so you should look for a suspicious executable with an unknown User ID next to it. Also, high CPU consumption is a common red flag.
Once you force quit the harmful process, go to the Applications folder and find Search Baron (or SearchBaron) in there. Send it to the Trash without a second thought. Then, access your Login Items screen under System Preferences and minus out the rogue entry to prevent it from being launched at boot time.
Now that you have removed the adware, proceed to fixing the browser that’s acting up. The most dependable approach is to restore its settings to their factory state (see instructions in the guide above). The disadvantage of this technique is that you will have to go through a somewhat tedious process of customizing the browser afterwards. To save yourself the trouble of applying all the personalized settings from scratch after the reset, consider disabling the Search Baron extension first and see if this fixes the problem. If it does, you’re good to go. If the redirects are still occurring, then the reset is your only option.
How do I get rid of malware on MacBook?
It depends on the type of malware that has infected your MacBook. In adware scenarios like the Search Baron attack, a combo of force-uninstalling the harmful app and resetting the affected web browser will do the trick. Keep in mind that unlike regular software, such PUAs (potentially unwanted applications) tend to be stubborn and therefore removing them from the Applications folder alone might not be enough.
To get around this persistence, quitting the unwanted process in the Activity Monitor should be your first move. Then, delete the bad entry from Applications and Login items. Finally, trash the respective browser extension. However, in many cases this is futile and you need to reset the browser to its original defaults.
Sometimes you should additionally examine the following directories for hidden malware files: /Library/LaunchAgents, ~/Library/LaunchAgents, /Library/LaunchDaemons, and /Library/Application Support. The malicious objects will look like com.MCP.agent.plist or similar, with the name of the infection (or its acronym) being part of the entry. This extra step is often required in situations where a scareware program hits a computer and displays phony alerts to convince you to buy its license.
If you are experiencing malware symptoms on your MacBook but cannot find all components of the offending program, then it could be a good idea to use a reputable security tool that will automatically identify and root out the threat.
How do I remove Search Baron from Safari?
In order to remedy Safari browser affected by the Search Baron virus, try to hunt down and delete the associated extension for a start. Click the Safari menu icon and select ‘Preferences’ in the drop-down menu. Hit the ‘Extensions’ tab on the resulting screen and find a rogue helper object called Search Baron. Be advised that the name may be different, so you should look for an item you don’t remember adding to Safari. Once found, go ahead and remove the culprit. Restart the browser and check it for symptoms of the hijack.
If redirects to searchbaron.com, and then to bing.com, are still the case, you should take your efforts up a notch and reset the browser. Here is the walkthrough you need to follow:
- Go to Safari’s ‘Preferences’ and select the ‘Advanced’ tab. Turn on the following option: ‘Show Develop menu in menu bar’
- A new item called ‘Develop’ will appear in the Safari menu bar. Click it and select ‘Empty Caches’
- Check if the Search Baron problem has been fixed. If it hasn’t, go to History in the Safari menu bar and click ‘Clear History’
- Select ‘all history’ in the follow-up dialog box and hit the ‘Clear History’ button again
- If the issue is still there, go to ‘Preferences’ again and click the ‘Privacy’ tab. Proceed to an option that says ‘Manage Website Data’. Click ‘Remove All’ and then the ‘Done’ button
- Restart Safari.
Bear in mind that these will only address the Search Baron hijacker attack if you have removed the potentially unwanted application beforehand. See the tutorial above and previous answers to learn all the relevant how-to’s.
How do I remove SearchBaron from Chrome?
If Google Chrome is repeatedly forwarding your traffic to SearchBaron.com, it means a dodgy extension has been surreptitiously added to the browser. Therefore, the logic of the fix is to find and eliminate this entity. Before you proceed, be sure to address the root cause of the hijack by removing the actual adware from your Mac, otherwise the perpetrating extension will be reinstalled shortly.
To sort out the problem in Chrome, try to get rid of the SearchBaron extension first. Here is the procedure:
- Click the ‘Customize and control Google Chrome’ (⁝) icon and select ‘More Tools’ – ‘Extensions’
- On the ‘Extensions’ screen, look for SearchBaron or another dubious-looking entry that doesn’t belong there
- Toggle it off and click ‘Remove’
- Restart Chrome.
Check if the redirect problem has been fixed. If it’s not, you will have to reset Chrome to its original defaults. This will delete your personalized settings, but compared to the SearchBaron frenzy, it’s the lesser of two evils. Adhere to the following steps to do it:
- Click the ‘Customize and control Google Chrome’ (⁝) icon and select ‘Settings’
- Pick the ‘Advanced’ option and scroll down to the ‘Reset settings’ subsection
- Select ‘Restore settings to their original defaults’
- On a dialog that will appear, click the ‘Reset Settings’ button
- Restart your Chrome browser. The problem shouldn’t be making itself felt anymore.
Why is Bing hijacking my browser?
Let’s get something straight: Bing doesn’t hijack browsers. Malware does. This is an important disambiguation that should be made before elaborating further on this issue. The reason why some Mac users treat Bing and a browser takeover synonymously is that Safari, Google Chrome, or Mozilla Firefox suddenly start returning this provider instead of the correct one specified in the settings. In plain words, the victims should blame it on a browser hijacking infection rather than Bing.
The authors of the unwanted app that overrides the Internet preferences are mishandling Bing to smokescreen their real intentions. Their plan is to abuse the fraudulently obtained control over a browser to promote shady web services, including phony search engines and advertising networks with a questionable track record. This explains why each redirect instance goes through a rabbit hole of dubious URLs such as searchmarquis.com, searchbaron.com, nearbyme.io, search1.me, api.lisumanagerine.club, hut.brdtxhea.xyz, search-location.com, and search.surfharvest.xyz.
Because the legitimate Bing search results are the landing pages, some victims may misinterpret the hijack as a trivial non-malicious glitch. Meanwhile, the sneaky adware app behind this digital quagmire will continue to boost its makers’ rogue e-marketing until removed from the Mac.
