- What is “"HP Scanner / HP Utility / Fax.Backend ..." will damage your computer”?
- “PDE.plugin will damage your computer” alert
- “Fax.Backend will damage your computer” Mac warning
- “hpPostProcessing.bundle will damage your computer” message
- “Matterhorn.framework will damage your computer” popup
- “Inkjet1.driver will damage your computer” alert on Mac
- “hpPostScriptPDE.plugin will damage your computer” popup warning
- “HPSmartPrint.framework will damage your computer” Mac alert
- How to fix “HPDM.framework … will damage your computer” warning (non-malware scenario)
- Ways to address “HP Scanner 3 / HP Utility… will damage your computer” malware-borne issue
- Get rid of “HPDeviceMonitoring... will damage your computer” virus alert using automatic removal tool
If you are struggling to fix the “HPDM.framework will damage your computer” alert issue on your Mac, here is a round-up of applicable options.
Update:
In late October last year, numerous Mac owners who were using Hewlett Packard printers ran into bizarre difficulties with these peripheral devices. All of a sudden, macOS started flagging HP drivers as malicious, with the following alert appearing whenever the users tried to print: “HPDeviceMonitoring.framework will damage your computer”. The warning also included a phrase saying, “This file was downloaded on an unknown date”. At the time of this publication (more than three months after the original reports), the issue isn’t making itself felt as badly, and yet it is still making lots of users frown.
First things first, HPDeviceMonitoring.framework isn’t a malicious app. It is a component of HP software geared toward ensuring hardware compatibility through valid drivers as well as proper interoperability between Macs and the manufacturer’s servers in terms of updates and other technical matters. In theory, macOS should never give users a heads-up about a legitimate entity like that. In practice, things got out of hand.
What is “"HP Scanner / HP Utility / Fax.Backend ..." will damage your computer”?
There are several theories. Let’s start with the more credible one. Alerts in that format constitute the logic of Gatekeeper, a macOS feature that keeps users from executing potentially dangerous code. If an app flunks this automated inspection because of dubious behavior or unknown signatures, the defenses kick in and display this pop-up when the Mac owner tries to run the software. This makes a whole lot of sense and should work wonders as far as security goes. But, red flags raised by the genuine HPDeviceMonitoring.framework object look like false positives, don’t they? Yes and no.
“HPDM.framework / HP Scanner / HP Utility... will damage your computer” message virus may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.When the issue broke out, HP representatives stated that they had inadvertently “revoked credentials on some older versions of Mac drivers”, which led to an influx of dissatisfied customers’ feedback. In other words, the vendor rendered code-signing certificates for a series of printer drivers null and void. Once the Gatekeeper module spotted a missing certificate along with invalid HP driver signatures, it started blocking the software and displaying the “HPDeviceMonitoring.framework will damage your computer” alert. By the way, this snafu is often accompanied by more than a dozen similar pop-ups:
- “commandtohp.filter” will damage your computer
- “FaxArchive.task” will damage your computer
- “Fax.Backend” will damage your computer
- “HP Scanner 3” will damage your computer
- “HP Utility” will damage your computer
- “HPDeviceMonitoring.framework” will damage your computer
- “HPDM.framework” will damage your computer
- “hpPostProcessing.bundle” will damage your computer
- “hpPostScriptpde.plugin” will damage your computer
- “inkjet1.driver” will damage your computer
- “inkjet3.driver” will damage your computer
- “Matterhorn.framework” will damage your computer
- “PDE.plugin will damage your computer
- “Productimprovementstudy.hptask” will damage your computer
- “ScanEventHandler.app” will damage your computer.
Here is a summary of several most-encountered alerts from this pool:
“PDE.plugin will damage your computer” alert
Normally, this pop-up doesn’t mean that the Mac is being affected by a piece of malware. PDE.plugin is a legitimate component of software made by Hewlett Packard HP. It runs on the computer if an HP printer is hooked up and the user creates a new print job. At some point, something went seriously wrong with the way macOS Catalina and macOS Big Sur treat HP drivers and auxiliary elements like this. The XProtect anti-malware feature built into these operating system versions flags PDE.plugin as harmful, hence the alert.
“Fax.Backend will damage your computer” Mac warning
As is the case with PDE.plugin, Fax.Backend is part of HP software environment that manages printing tasks on Mac machines. Despite its benign gist, macOS defenses give users a heads-up whenever it’s being executed. According to some reports mentioned above, this is happening because code-signing certificates on older versions of HP drivers for Mac were accidentally revoked. That said, installing the latest version of the printer software should help – the “Software Update” pane under System Preferences might show an update ready to be applied. Alternatively, users can download and install the new build from Apple Support site manually (the walkthrough will be provided further down).
“hpPostProcessing.bundle will damage your computer” message
Technically, this scenario barely differs from the above two predicaments. The entity named hpPostProcessing.bundle is yet another Hewlett Packard software component that facilitates printing. macOS most likely rings the alarm bells wrongfully by displaying a notification that says the file was downloaded on an unknown date. And yet, there is always a chance that malware could mimic the known-legitimate process to cloak its pranks inside a Mac. The likelihood of this situation is by all means worth verifying.
“Matterhorn.framework will damage your computer” popup
When printing with HP gear, Mac users may also get an alert that says a file named Matterhorn.framework is a potential threat. This is one more instance of a false positive where macOS Big Sur and Catalina report suspicious characteristics of otherwise trusted software. The popup offers no obvious way to get around the blocking and run the file anyway, so those affected end up unable to print. In most cases, users can fix the issue by deleting the external device in System Preferences > Printers & Scanners and then re-adding it along with fresh drivers.
“Inkjet1.driver will damage your computer” alert on Mac
Driver updates don’t always go smoothly. Starting October last year, numerous Mac owners have been bumping into popup messages blaming a possible system damage on inkjet1.driver file. All these people ended up in the same boat because they use HP printers that got a buggy firmware update. Inability to print is a real-world upshot of this slip-up on Hewlett Packard’s end. Thankfully, removing the printer in System Preferences and adding it anew usually helps. This process also involves downloading generic drivers that won’t raise red flags when inspected by macOS Gatekeeper and XProtect.
“hpPostScriptPDE.plugin will damage your computer” popup warning
In most cases, this one is another upshot of the HP certificate expiration drama. Although the device supplier fixed it a long time ago, Mac owners who are still using obsolete versions of the software are getting this irksome malware notification when they start a new print task. The comment on this popup that says, “This file was downloaded on an unknown date” is a hazy explanation of the cause for such a belligerent system response.
The most effective workaround is to delete and then reinstall the HP software suite that’s raising red flags. Doing so will pull in the latest hardware drivers that don’t tick off XProtect and notarization-related security features that ship with macOS. Speaking of which, these warnings often begin appearing right after a system update. This suggests that Apple’s protection mechanisms get some fine-tuning that results in the detection of processes that used to slip below the radar.
“HPSmartPrint.framework will damage your computer” Mac alert
These popups are also a pain in the neck for those running outdated Hewlett Packard printer software with a no-longer-valid digital certificate. There are reports galore about this activity on the web. If it weren’t for the code-signing blunder, most HP printer users would probably never know the HPSmartPrint.framework file resides on their Macs. As is the case with the other warnings on the list, this bug broke out last October and has been encountered throughout 2021.
The hardening of Apple’s malware detection practices is certainly welcome, but things get out of hand for thousands of users when this response is blown out of proportion. Obviously, HP products have nothing to do with malicious software, and the Cupertino company should fine-tune its security algorithms to differentiate between outright threats and legitimate programs that have certificate inconsistencies.
There is one more theory. It comes down to a conspiracy with a cybercriminal flavor that supposedly resulted in injecting malware into the authentic HP printer drivers. On a side note, this type of compromise isn’t as marginal as it may appear. Threat actors often exploit vulnerabilities in reputable companies’ websites (mostly in outdated plugins or themes) to embed scripts that furtively contaminate visitors’ devices with malicious code. They may as well get unauthorized access to an app release hosted on an official site and trojanize it.
The purportedly toxic version of HP printer software is rumored to come from a survey organized by the device maker. There is no evidence backing this narrative, though, aside from a few posts on tech forums. Even if this is far-fetched, the likelihood of malware setting this predicament in motion isn’t minuscule at all. Moreover, something like this has happened before. The outbreak of the first fully-fledged Mac ransomware called KeRanger relied on a malware-riddled version of a popular BitTorrent client.
Whether or not the HP story fits this mold remains unclear. Again, this is most likely an unintentional blunder of the manufacturer. One way or another, the following steps will help you take care of the incredibly annoying printer problem and check if malware is to blame.
How to fix “HPDM.framework … will damage your computer” warning (non-malware scenario)
If you are experiencing issues over HPDeviceMonitoring.framework, the most likely root cause is within the benign realm. That is to say, Gatekeeper could be ringing the alarm bells due to a misconfiguration on HP’s end, such as a temporary code-signing certificate problem. Therefore, you should be able to sort things out by following the steps below.
- Use AirPrint. If your printer supports this awesome feature, you don’t need any drivers to print. In other words, your troubleshooting will stop successfully at this point. If AirPrint isn’t available, though, you’ll have to keep going through trial and error (see tips below).
- Purge the faulty drivers. Go to /Library/Printers/ and move the folder called “hp” to the Trash. Then, open System Preferences > Printers & Scanners and delete the HP printer by clicking the minus button.
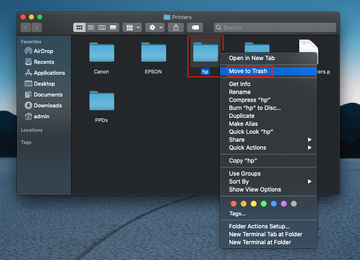
- Let macOS find the right driver. Once you delete the “hp” folder from your Library and remove the device from the Printers & Scanners list, reconnect the printer via a USB port. macOS should trigger a pop-up offering you to download and install the appropriate software – just follow the prompts to complete the procedure. If the system doesn’t find the driver, proceed to the next step.
- Download and install the driver manually. If you own an HP printer manufactured in October 2017 and later, visit support.hp.com, search for your printer model, and install drivers from there. If your device was released earlier, install the HP Printer Drivers v5.1 for macOS package available at support.apple.com.
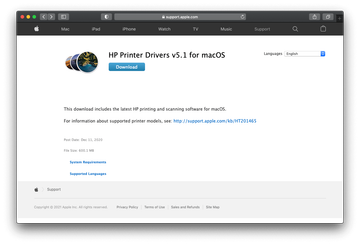
If the above steps did the trick, your printing experience will get back on track and you can heave a sigh of relief. However, there could be situations in which the problem persists because it wasn’t precipitated by HP’s driver deployment slip-ups, in the first place. The messy condition may be a byproduct of malware activity on your Mac.
Ways to address “HP Scanner 3 / HP Utility… will damage your computer” malware-borne issue
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
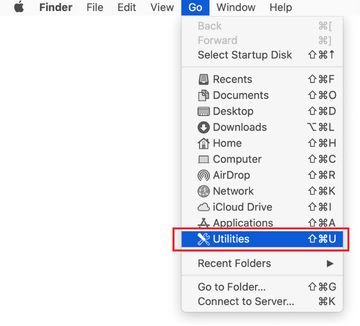
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
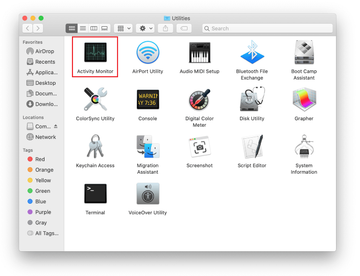
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
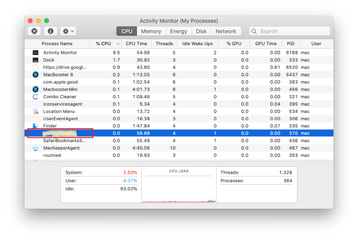
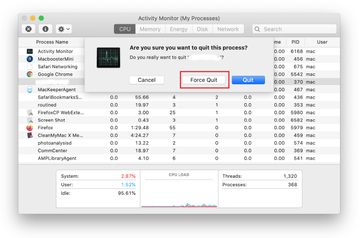
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
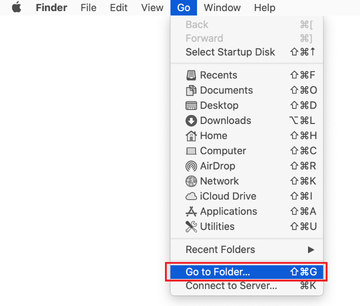
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
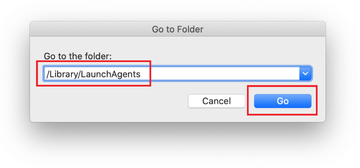
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
Examine the contents of the LaunchAgents folder for dubious-looking items. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
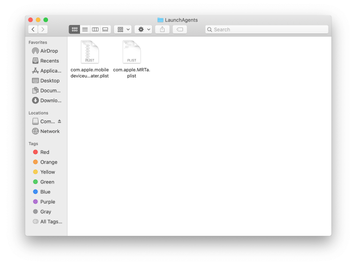
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
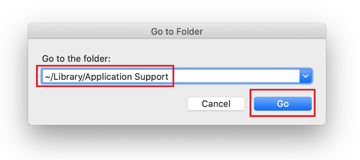
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are Searchlee, ProgressSite, and IdeaShared.
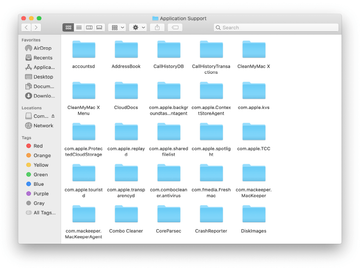
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
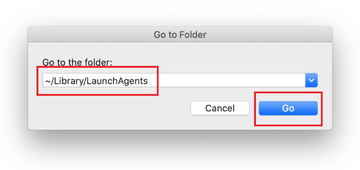
The system will display LaunchAgents residing in the current user’s Home directory. Look for dodgy items related to HPDeviceMonitoring.framework (see logic highlighted in subsections above) and drag the suspects to the Trash.
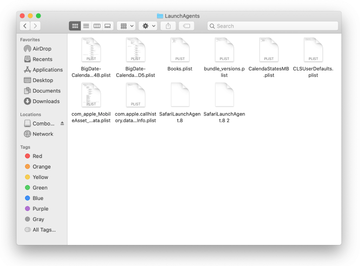
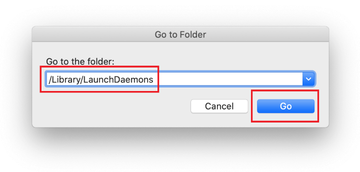
Type /Library/LaunchDaemons in the Go to Folder search field.
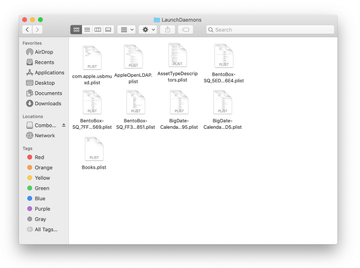
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
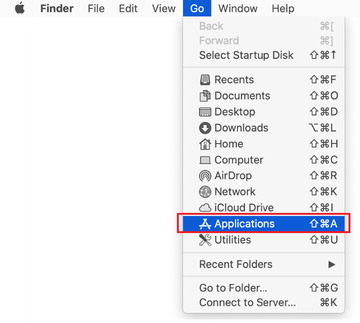
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
Find the app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

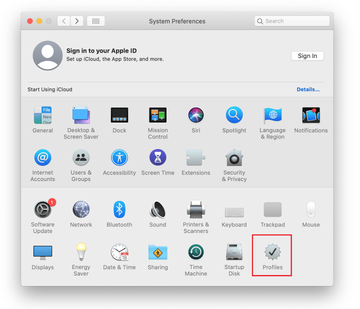
Expand the Apple menu and select System Preferences.
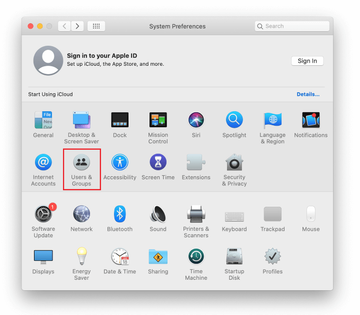
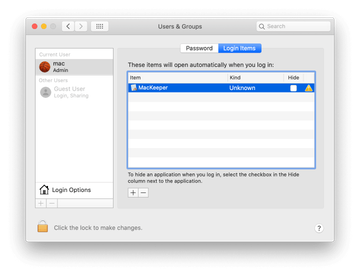
Proceed to Users & Groups and click on the Login Items tab.
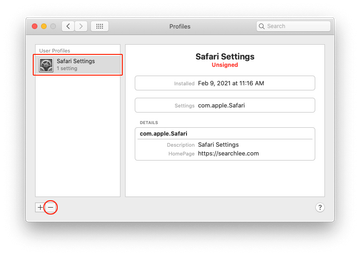
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include SmartSignalSearch, TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of “HPDeviceMonitoring... will damage your computer” virus alert using automatic removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove HPDM.framework pop-up virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the HPDM.framework pop-up issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
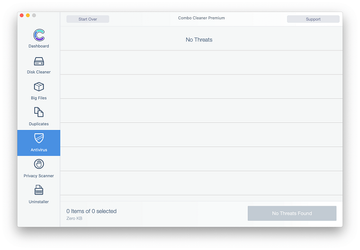
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove HPDM.framework pop-up threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
