Find out how to remove MainReady, a strain of Mac adware that redirects victims to junk websites, displays annoying ads, and furtively downloads other threats.
There is no such thing as an invulnerable Mac whose built-in defenses stop malware attacks in their tracks. A polemic is underway whether viruses, self-replicating forms of malicious code, contaminate these computers without any user involvement, but the big picture is much clearer when it comes to adware. Often collectively called potentially unwanted applications (PUAs), these culprits are nearly ubiquitous and growingly common in the macOS environment. The tactics employed by the cybercriminals behind a new Mac threat called MainReady demonstrate how treacherous and evasive the present-day adware has become. First things first, it is part of a large malware family sharing several easy-to-identify hallmarks. Similarly to pests called IdeaShared, FocusProvide, PhaseSearch and numerous previously released clones, the dodgy app in question uses an icon with a magnifying glass symbol in it. The icon color can vary, though – from green to bluish. Although this external quirk seems like a trivial feature, it is a red flag to watch out for.
Another thing all the personas of this adware lineage have in common is that they operate in lockstep with notorious, long-running browser redirect viruses. In the case of MainReady, the attack always co-occurs with iterative instances of the victim’s Internet traffic being forwarded to a service called Safe Finder. Although it’s disguised as a fully-featured search provider, this impression is wrong because all the entered queries lead to a Yahoo Hosted Search destination. That’s a custom service that’s, obviously, being mishandled by some wicked makers of Mac viruses who seek easy gain from redistributing the infected users’ traffic. It’s worth emphasizing that before resolving the landing page the browser hits an in-between location related to the so-called a-akamaihd.net framework, another one that’s known to constitute malefactors’ plots.
MainReady may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.Ultimately, the MainReady infection forces the victim’s browser to jump from one unwanted site to another in a loop that doesn’t appear to have any apparent hole to escape. The reason is that the original web navigations preferences defined by the user get an overhaul without permission and it’s the adware under scrutiny to blame for these tweaks. Additionally, the harmful app displays sponsored content above the fold to add one more ply to its authors’ monetization hoax. The ads come in various forms and shapes, from in-text links and price comparison sections deposited where none of these materials belong, to full-page interstitial advertisements that are opened on their own and have to be closed off and on so that the browser continues to function properly.
MainReady is spreading alongside ostensibly harmless software via booby-trapped installation clients touted on questionably safe web portals. Predictably enough, the default install in these scenarios doesn’t mention any adjacent entities being pulled into the Mac simultaneously with the core freeware. The only way to see the entirety of bundled objects and uncheck the fishy ones is to select the custom setup mode. Unfortunately, this is what most people hardly ever do. Once the trespass has been completed, MainReady virus creates a rogue configuration profile listed under System Preferences on the Mac. Its task is to establish persistence and prevent the victim from reverting to the correct search engine and homepage settings in their browser of choice. With that said, this is a stubborn pest that doesn’t succumb to regular removal. The good news is, a little bit of thinking outside the box will help vanquish the PUA.
MainReady virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
- Open up the Utilities folder as shown below
- Locate the Activity Monitor icon on the screen and double-click on it
- Under Activity Monitor, find a process named MainReady, select it and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
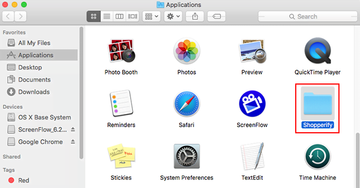
- Click the Go button again, but this time select Applications on the list. Find the entry for MainReady(Main Ready) on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it
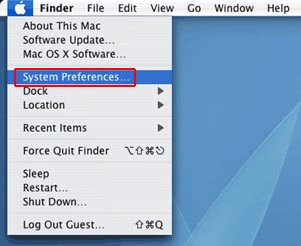
- Now go to Apple Menu and pick the System Preferences option
- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the box is started up. Locate MainReady or other potentially unwanted app there and click on the “-“ button
Get rid of MainReady ads and redirect activity in web browser on Mac
To begin with, the web browser settings taken over by the MainReady virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Stop MainReady virus symptoms in Safari
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
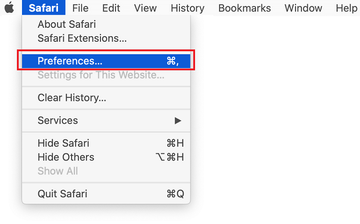
- Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
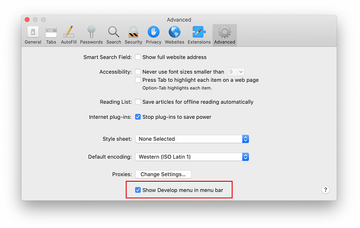
- Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
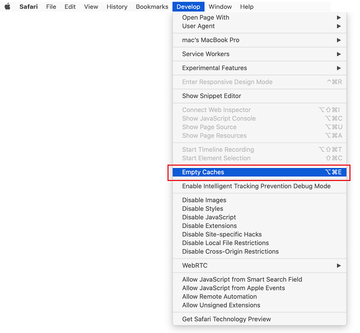
- Now select History in the Safari menu and click on Clear History in the drop-down list.
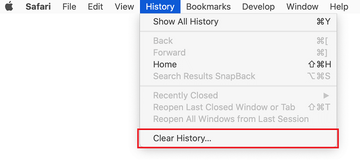
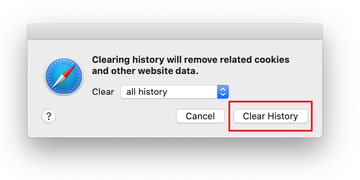
- Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
- Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
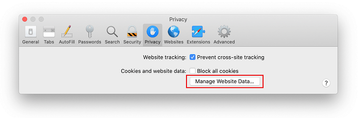
- The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
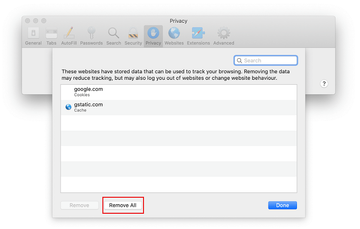
- Restart Safari
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Remove MainReady redirects in Google Chrome
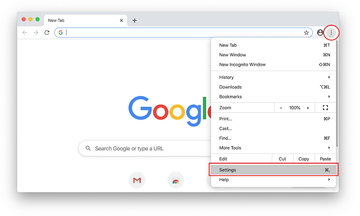
- Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
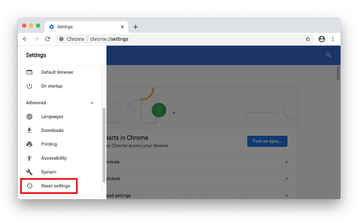
- Scroll down to the Reset settings section.
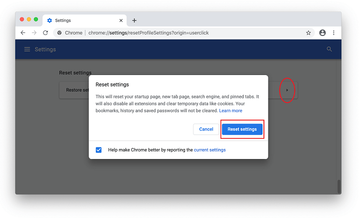
- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- Remove MainReady redirect virus from Mozilla Firefox
- Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
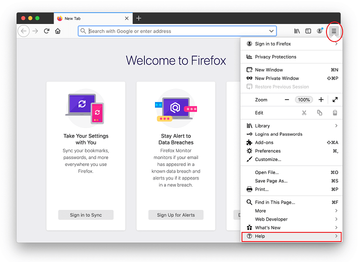
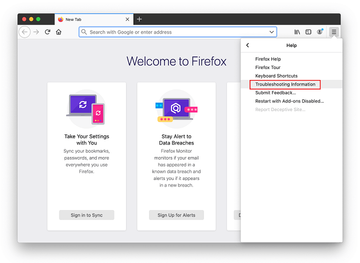
- When on the Troubleshooting Information screen, click on the Refresh Firefox button.
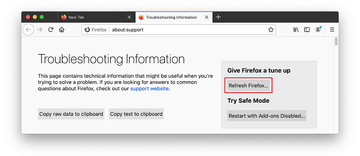
- Confirm the intended changes and restart Firefox.
- Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
Get rid of MainReady virus using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove MainReady virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the MainReady issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
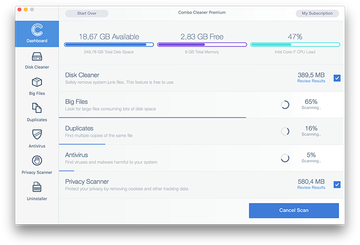
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove MainReady threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.