- Safe Finder’s claims are at odds with its dubious activity
- The pest makes a mess of a victim’s search preferences
- A multi-vector distribution campaign
- Opportunistic Mac threats
- New tactics are transforming the hoax
- Safe Finder adware manual removal for Mac
- Get rid of Safe Finder virus in web browser on Mac
- Get rid of Safe Finder virus using Combo Cleaner automatic removal tool
- FAQ
This entry explains how the Safe Finder hijacker operates on Mac and provides comprehensive instructions on search.safefinder.com virus removal.
Update:
| Threat Profile | |
|---|---|
| Name | Safe Finder (search.safefinder.com) browser hijacker |
| Category | Mac adware, browser hijacker, redirect virus |
| Related Domains | search.macsafefinder.com, search.safefinder.biz, search.safefinder.info, search.safefinderformac.com, feed.safefinder.com, searchlee.com |
| Symptoms | Redirects web browser to Yahoo via third-party websites such as search.safefinder.com, adds sponsored content to search results, causes system slowdown, resists regular removal |
| Distribution Techniques | Malware-riddled app bundles, fake Adobe Flash Player update popups, spam |
| Severity Level | Medium |
| Damage | Unwanted changes of custom browsing settings, privacy issues due to Internet activity tracking, search redirects, redundant ads |
| Removal | Scan your Mac with Combo Cleaner to detect all files related to the browser hijacker. Use the tool to remove the infection if found. |
Infections like Safe Finder break the stereotype of malware-free Macs. In fact, browser hijackers and ads-serving threats pose, by far, the prevalent category of offending software affecting this operating system. The impact from such attacks normally won’t go beyond Internet surfing alone, but the restricted scope of adverse influence doesn’t make these occurrences any less abominable than other further-reaching breaches. The above-mentioned app reroutes its victim’s Safari, Chrome and Firefox preferences to search.safefinder.com or search.macsafefinder.com. The less commonly visited junk sites from the same pool include search.safefinder.biz, search.safefinder.info, and search.safefinderformac.com. What this means is that the unwelcome page will be popping up instead of the custom homepage, favorite search engine, and new tab. Furthermore, the same effect may occur when the user simply enters an arbitrary site’s URL in the address bar. This indicates that the hijacker also skews DNS settings on infected machines running macOS.
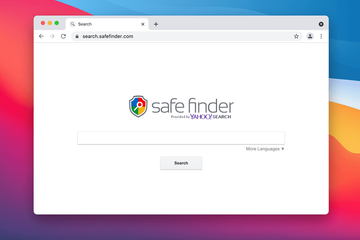
Safe Finder’s claims are at odds with its dubious activity
Officially, Safe Finder is advertised as “the perfect tool to simplify the web”. It is developed by Linkury Ltd., an Israeli company that has gained notoriety for creating and distributing Mac browser hijackers and rogue cleaners on a mind-boggling scale. This controversial vendor engages sketchy app bundles as the main source for the unwanted installations. The service is supposed to add a non-intrusive widget called “Safe Finder toolbar” to one’s preferred browser that contains icons for a number of useful features, including website translation to a language of choice, quick sharing on popular social networks, and safety ratings of web pages the user is about to visit. These benign and commendable declarations, though, become null and void as the app causes web browsers to get completely out of hand instead. The victim will ultimately find it hard to visit any website other than search.safefinder.com or search.macsafefinder.com. Authorization to make changes to browser settings on a contaminated Mac is the milestone that adware makers tend to skip, so the consequences of this trespass are usually a surprise to targeted users.
The pest makes a mess of a victim’s search preferences
In February 2020, the Safe Finder campaign started undergoing transformations that add one more notorious technique to the mix. The victims find themselves trapped in a browser misconfiguration quandary with Akamaihd.net at its core. The perpetrating code may replace one’s default web search provider with a URL whose structure fits the following sample pattern: search8952443-a.akamaihd.net. The fragment preceding the hyphen varies and can be something like “default[random digits]” or “lkysearchds[random digits]”. This clever tweak involving a cloud services and content delivery giant Akamai is, obviously, intended to keep the adware activity afloat and help the malicious infrastructure survive all forms of blacklisting.
Safe Finder may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
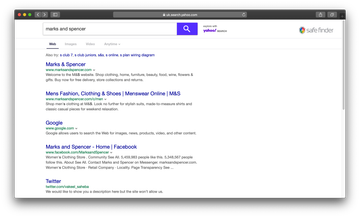
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.When the victim enters keywords in the dodgy service’s search box, they are forwarded to custom Yahoo search results. The involvement of legit providers is a common thing for traffic redistribution schemes in the Mac malware ecosystem. This way, the crooks make the attack seem to be a non-malicious tweak of one’s web surfing activities. Plus, the objective behind plugging Yahoo into this electronic stratagem is to create an illusion as if the Safe Finder landing page had some genuine web search features. It doesn’t actually accommodate any such functionality of its own, though, and simply embeds third-party sponsored content into relevant results returned by another engine. By the way, the dubious service under scrutiny is also a long-running generic entity that has spawned other browser hijackers like Any Search Manager.
A multi-vector distribution campaign
The way Safe Finder makes its way into a Mac is a whole separate story. Rather than study its ‘unique’ features and install it consciously, people allow it to literally slip by. The app’s payload accompanies other software like Advanced Mac Cleaner, but it’s usually a surreptitious process that makes it difficult for users to identify the threat and prevent it from getting in. What cloaks the trespass is an installation client that promotes several apps under the guise of one harmless utility. The catch is that such installers claim to smoothen the setup of popular freeware, which might push many users to proceed without paying attention to pitfalls that aren’t in plain sight. The only way to avoid the attack is to deselect the extra items accompanying the main application, but this is a matter of going the custom setup route rather than sticking with the default (express) option.
The fake Adobe Flash Player update campaign is one of the long-standing strongholds of Safe Finder distribution. This attack vector has seen a considerable spike since March 2020. Maybe the growth stems from Adobe’s officially confirmed plans to end support of Adobe Flash later this year. With that said, the adware authors are busy squeezing the maximum out of their readily available online hoaxes revolving around this controversial product. The scheme is trivial: the misleading updater touted on compromised or malicious web pages contains the Safe Finder payload in the same bundle.
Opportunistic Mac threats
Safe Finder raid can also be double trouble due to concurrent infestation of the Mac with an ad-injecting app such as SystemNotes 1.0 or AddUpgrade 1.0. The co-promoted adware represents an increasingly prolific lineage of potentially unwanted applications (PUAs) sharing an easy-to-identify hallmark sign - the green or bluish icon with a magnifying glass symbol inside. This ostensibly petty parasite can really give the victim a hard time by displaying a ton of sponsored information on web pages. The adware family in question is constantly expanding with new samples. Its productivity can reach a whopping several releases per week, so the contagion is an ever-moving target and it’s problematic to pinpoint the exact name of the troublemaking app at any given time.
One of the flustering things about these nasties is that they get an unproportionally vast range of privileges as compared to regular browser extensions. For instance, they can read sensitive data from web pages, including phone numbers, authentication details, and credit card info. On top of that, the victim’s entire browsing history is harvested as well. The symbiosis of a “classic” browser hijacker and adware means the cybercriminals behind this wave are no strangers to multi-pronged attack monetization.
New tactics are transforming the hoax
As this campaign evolves, its operators are adding new redirect schemes to their genre. In addition to the above-mentioned abuse of the Akamaihd.net service, the malefactors have started using variable URLs that replace the default web search setting in a malware-raided browser. Several examples of these domains are search.majorinputs.com, search.practicalsprint.com, search.windowtask.com, search.validplatform.com, search.handlersection.com, search.adjustablesample.com, and search.adjustablesample.com. Each one leads to a Yahoo hosted landing page featuring Safe Finder.
Given the stealthy infiltration technique, people mostly have to deal with the aftermath of the assault, which is a fairly tough challenge. The part below covers the must-take steps to eliminate this virus from Mac and rectify the modified browsing configuration.
Safe Finder adware manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
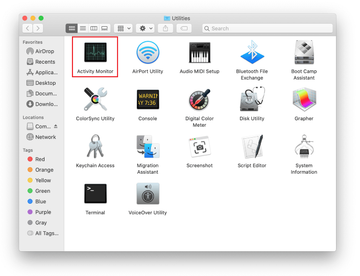
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
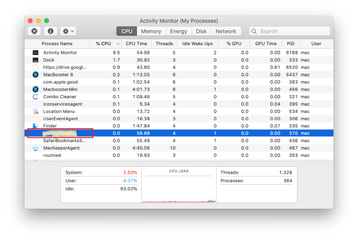
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
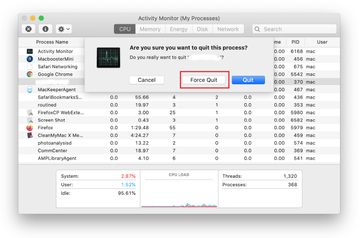
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
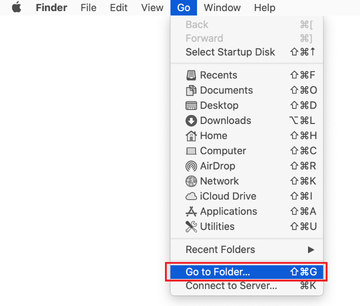
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
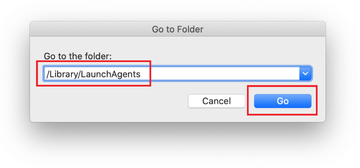
Examine the contents of the LaunchAgents folder for dubious-looking items. The object known to be related to Safe Finder virus is called com.ExpertModuleSearch.plist. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
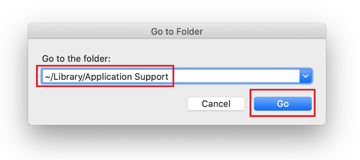
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
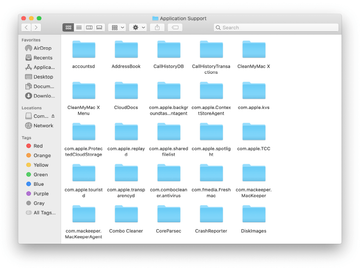
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are com.ExpertModuleSearchP.plist, IdeaShared, and ExtraBrowser.
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
The system will display LaunchAgents residing in the current user’s Home directory. Look for com.ExpertModuleSearch.plist or other dodgy items related to Safe Finder virus (see logic highlighted in subsections above) and drag the suspects to the Trash.
Type /Library/LaunchDaemons in the Go to Folder search field.
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
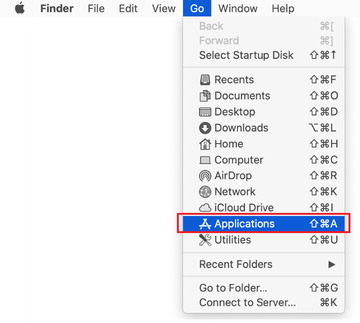
Find the entry for for Safe Finder (SafeFinder), SystemNotes 1.0 or another app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

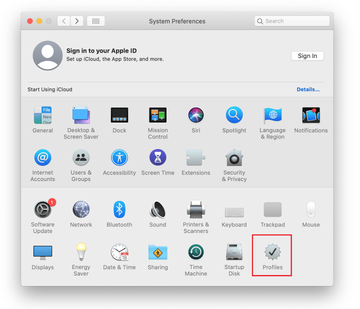
Expand the Apple menu and select System Preferences.
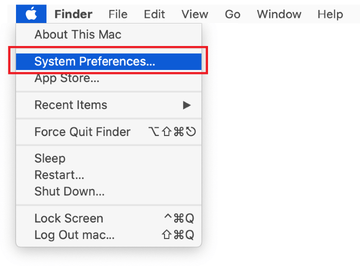
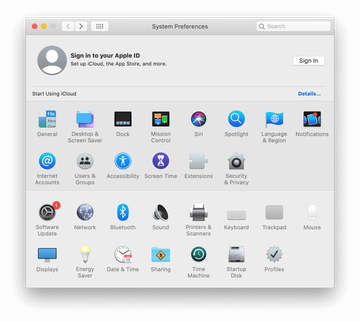
Proceed to Users & Groups and click on the Login Items tab.
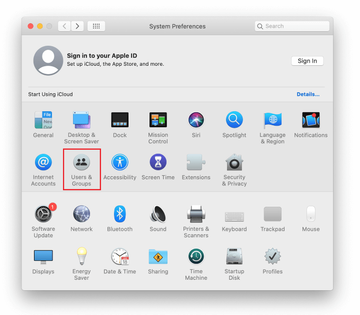
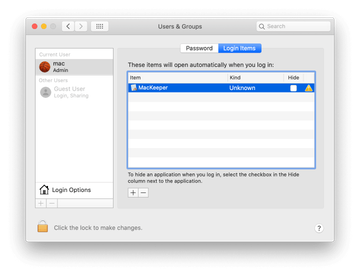
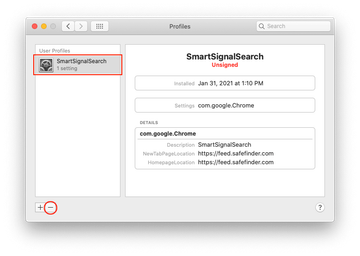
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include SmartSignalSearch, TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of Safe Finder virus in web browser on Mac
To begin with, the web browser settings taken over by the Safe Finder virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Remove Safe Finder virus from Safari
Open the browser and go to Safari menu. Select Preferences in the drop-down list.
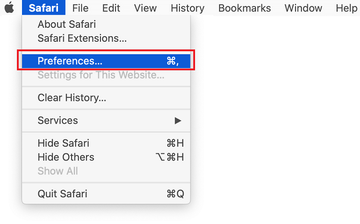
Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
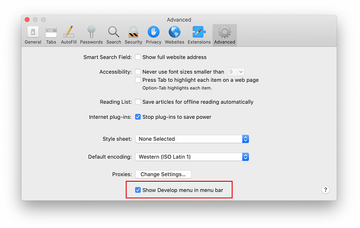
Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
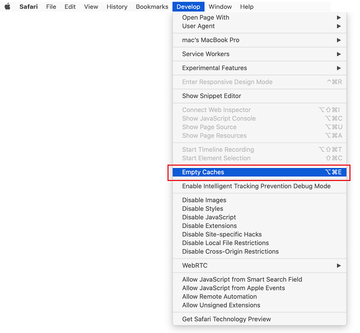
Now select History in the Safari menu and click on Clear History in the drop-down list.
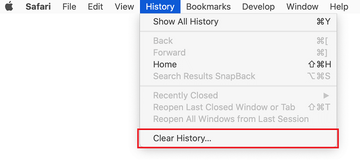
Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
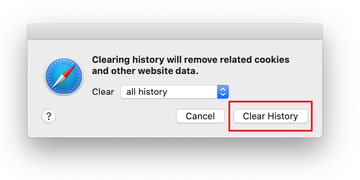
Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
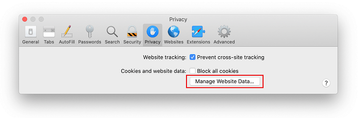
The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
Restart Safari
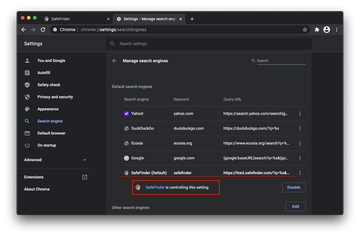
- Remove Safe Finder in Google Chrome
Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
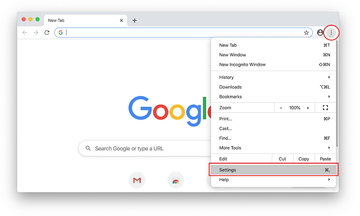
When on the Settings pane, select Advanced
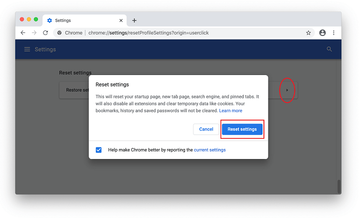
Scroll down to the Reset settings section.
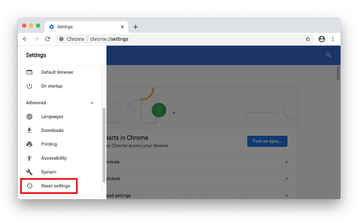
Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Remove Safe Finder from Mozilla Firefox
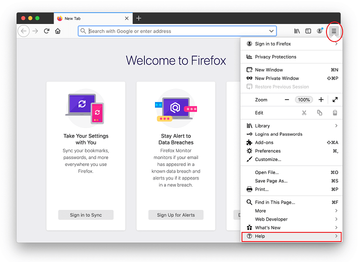
Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
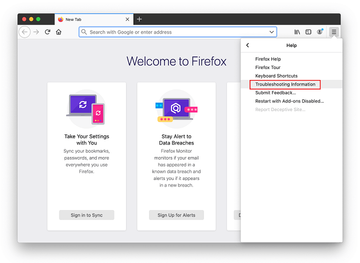
When on the Troubleshooting Information screen, click on the Refresh Firefox button.
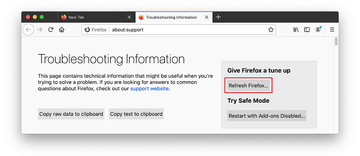
Confirm the intended changes and restart Firefox.
Get rid of Safe Finder virus using Combo Cleaner automatic removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Safe Finder virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Safe Finder issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
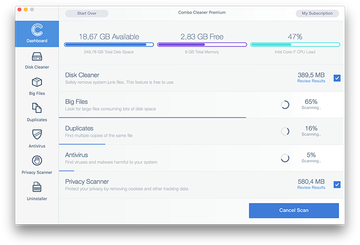
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
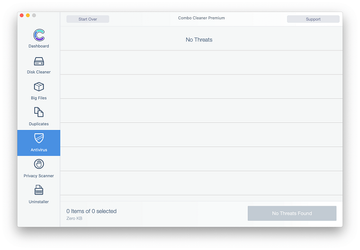
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
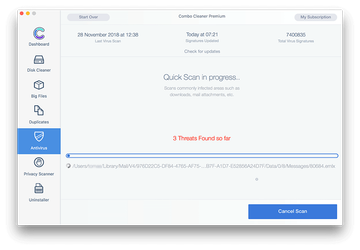
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Safe Finder threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
FAQ
Is SafeFinder a virus?
The shades of categorization vary, but SafeFinder is definitely not a benign application. At first sight, it appears to deliver a combo of ostensibly useful features, such as one-click sharing, content translation and harmful site alerts. However, this turns out to be just the tip of the iceberg upon closer inspection.
The flip side of installing SafeFinder is that your web browsing will undergo an overhaul without your consent. The app will replace your web preferences with a page controlled by the malware operators, such as search.safefinder.com or search.macsafefinder.com. The resulting site is basically worthless search-wise, simply redirecting all the queries to Yahoo.
When running on a Mac, the infection also collects the victim’s browsing details, including Internet history and search terms. This information may be further handed over to unscrupulous advertisers and other third parties behind the user’s back. To top it all off, SafeFinder is distributed in an unethical way that has nothing to do with one’s informed decision.
Here’s the verdict: SafeFinder is undoubtedly malicious. Some researchers label it as a virus, while others prefer a slightly different classification, such as PUP (potentially unwanted program) or adware. One way or another, this sketchy app should be avoided by all means.
Why is SafeFinder my search engine on Mac?
It’s because a strain of malware has infected your Mac. The unwelcome app is designed to change the browsing preferences in a system it’s running on, including the default search engine. These tweaks aren’t based on user approval, which explains why the victims are clueless about why all their searches are forwarded to search.safefinder.com or other affiliated replicas. In some cases, the virus meddles with one’s favorites (bookmarks) by appending the rogue URL string at the end of the user-defined values. This adds an extra layer of persistence to the browser hijack.
How do I get rid of Safe Finder on MacBook Pro?
Start the removal process by looking for the misbehaving item in your Applications folder and Login Items under System Preferences. All entries with ‘Safe Finder’ in their name (the spelling may vary) should be deleted. If you are unable to send the harmful app to the trash due to an error, open the Activity Monitor and force quit the dodgy process first. Be sure to empty the Trash once you successfully remove the culprit.
You’re more than halfway done. The next step is to fix the affected web browser and stop the obnoxious redirects in their tracks. To do it, go to your browser’s preferences and delete the Safe Finder extension. If this doesn’t do the trick, reset your browser to its original defaults and then define your correct custom settings.
How do I remove Yahoo from my Mac?
To begin with, it makes sense to rephrase it as follows: how do I remove Safe Finder virus that redirects all my searches to Yahoo? As previously mentioned, the malicious app forces hits to its landing page powered by Yahoo search. This fact simply indicates that the shady service in question doesn’t provide any search capacity of its own. Instead, it displays ads and redistributes the web traffic obtained in an underhand way.
At the end of the day, you need to address the Safe Finder issue so that your searches don’t end up on Yahoo anymore. See the guide above to get an idea of how to find and remove all components of the infection from your Mac.
What is Adware Linkury?
Also referred to as Adware.Linkury, this is a generic detection for one of the dominant families of browser hijackers targeting Macs. For the record, this strain is quite active in the Windows environment, too. The codename is derived from the name of the company that builds adware applications and spreads them under the guise of useful extensions, as is the case with the Safe Finder toolbar described in this article. The vendor is Linkury Ltd. (official website linkury.com). Based in Israel, it dominates the present-day ecosystem of dubious web traffic monetization with Macs at its core. A distinguishing characteristic of the Adware Linkury family is that unethical bundling is its primary distribution vector.