Get an overview of Mac ransomware 2025 in general and the prevalent extortion vector via fraudulent use of Apple’s Find My iPhone feature in particular.
Update:
Even with cutting-edge tools and considerable resources on their hands, cybercriminals don’t have much room for maneuver when it comes to infecting macOS or iOS devices. This is largely thanks to professionals such as network administrators and systems engineers who design, maintain, and constantly improve Apple’s security ecosystem (what does a systems engineer do). Another obvious reason is that Apple has contrived a security architecture sturdy enough to thwart most attack mechanisms that work on Windows. Under the circumstances, threat actors are bound to discover alternate weak links in this strong defense chain and, unfortunately, have had some success.
Screen lockers raiding Apple devices
While depositing run-of-the-mill crypto ransomware on Mac is easier said than done, felons have found a workaround whose gist consists in abusing a legitimate feature called Find My iPhone. On a side note, this service has been superseded by Find My app in iOS 13. Originally, this functionality is aimed at helping Apple users lock their lost or misplaced device remotely and set up a specific message on the screen so that the person who finds it can contact the owner. Crooks have learned to turn this great feature against users by locking their devices with a passcode and extorting Bitcoins to unlock.
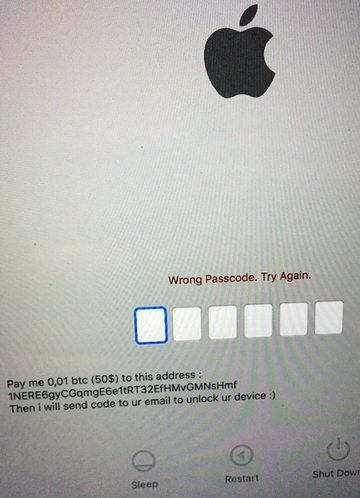
The workflow of this type of attack presupposes that someone performs unauthorized sign-in to a Mac user’s personal account at iCloud.com. This process can only be successful if the intruder has the would-be victim’s Apple ID and password. There are different theories on ways that the perpetrators obtain these sensitive credentials. The most likely method is through breaches of certain online services. Here’s a plausible scenario: an Apple customer uses the same email address and password to log into their iCloud account and multiple other accounts. If hackers breach servers of some third-party provider and steal numerous users’ PID (personally identifiable data), they may try their luck and use these credentials to access the compromised users’ iCloud profiles.
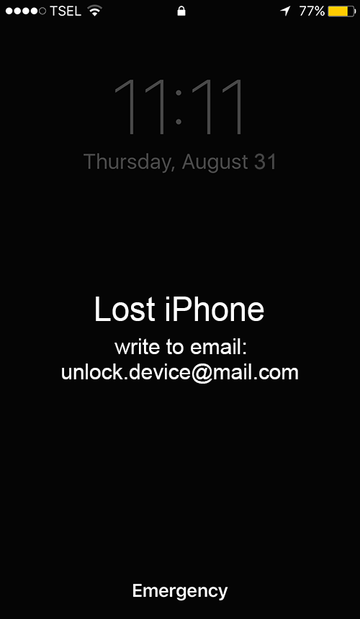
Once an attacker has furtively logged in, they proceed to the above-mentioned Find My iPhone app and enable the remote device lock. A serious caveat in this context is that locking down a Mac, iPhone or iPad this way can be completed even if two-factor authentication is toggled on. That’s due to the specificity of this emergency feature. The trespasser will also type some custom text to be displayed on the victim’s screen. Some examples are, “Pay me 0.01 BTC ($50) to this address: [hacker’s Bitcoin address], then I will send code to ur email to unlock ur device,” or “Your computer is disabled, write to email: apple.help@post.com.”
Actually, the ransom note can be anything, depending on the attacker’s creativity. The email address indicated in it can vary, too. Aside from apple.help@post.com mentioned in the example, some of the reported contact details include apple.help@europe.com, pass.apple@mail.com, unlock.device@mail.com, help.apple@gmx.com and helpappledevice@gmail.com, to list a few.
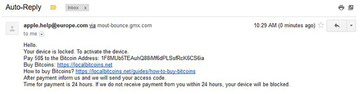
If a hacked user chooses to go the route imposed by the perpetrators and sends an email to the indicated address, they will receive an auto-reply with unlock instructions. Again, the wording varies, but it mostly goes, “Hello. Your device is locked. To activate the device, pay $50 to the Bitcoin address: [hacker’s BTC address]. After payment inform us and we will send your access code. Time for payment is 24 hours. If we do not receive payment from you within 24 hours, your device will be blocked.”
File-encrypting Mac ransomware is an escalating peril
The above extortion methodology is, by far, the most widespread ransom scam encountered by Apple users nowadays. However, a more sophisticated technique is gearing up for a rise as well. It is reminiscent of commonplace Windows ransomware attacks and often revolves around a RaaS (Ransomware-as-a-Service) model.
• MacRansom
This malicious framework is being promoted via Dark Web forums. To try their hand at Mac extortion, wannabe criminals need to contact the proprietors of this RaaS via ProtonMail, a well-known encrypted email provider. The creators will quite likely respond with a sample of the crypto ransomware.

One of the worst hallmarks of MacRansom is its ability to circumvent administrator permission when being installed, so the victim isn’t likely to notice anything wrong going on. Then, the culprit scours the /Volumes directory for the user’s personal data. This particular path includes all hard disks, removable media currently plugged in, as well as Time Machine backups. Having completed its scan for valuable files, the infection encrypts all matching entries and sprinkles a bevy of README documents containing ransom instructions. The crooks typically demand 0.25 Bitcoin (about $1,000) for data decryption.
• KeRanger
Another variant of file-encrypting Mac ransomware is a strain called KeRanger. It originally did the rounds via a booby-trapped build of Transmission, a mainstream BitTorrent client for Apple computers. Ever since the app got an emergency patch due to the newsmaking incident, the culprit has been mainly distributed by means of freeware bundles and malicious spam. Having scanned the host’s hard disk for potentially valuable files, KeRanger employs RSA-2048 (asymmetric cipher) to lock them all down. Unlike the above-mentioned MacRansom plague, it additionally subjoins the .encrypted extension to every hostage item.
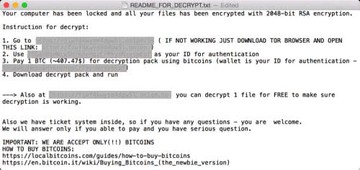
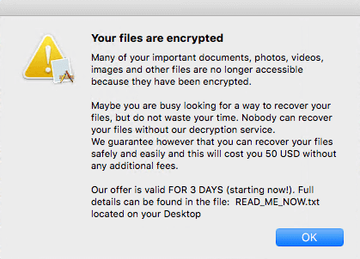
The ransom note is a document named README_FOR_DECRYPT.txt shown below. The size of the ransom has fluctuated over time, currently being set to about $500 worth of Bitcoin. Although KeRanger is an oldie, no cure has been found for its malicious encryption, so the victims are bound to cough up the money unless they have a recent data backup.
• Patcher
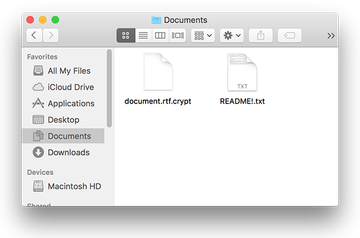
The category of crypto ransomware zeroing in on Mac machines is also represented by a sample dubbed Patcher. It is referred to this way because its installer impersonates a crack tool for unlicensed copies of Microsoft Office and Adobe Premiere Pro CC suites promoted on BitTorrent resources. Coded in Swift programming language, the Patcher ransomware first encrypts a victim’s personal files with a random 25-character key and then moves these inaccessible entities to encrypted ZIP archives. The original files are obliterated.
Similarly to KeRanger, this pest concatenates a peculiar extension to every encrypted file, namely the .crypt suffix. The ransom note, README!.txt, instructs the user to send 0.25 BTC to the attacker’s wallet in order to get the decryption key. According to a number of analytical reports on this infection, its creator cannot actually restore the data because Patcher doesn’t interact with any Command and Control server, so the adversary doesn’t have the secret key for real. This case demonstrates that although Mac ransomware has been around for years, even samples proliferating in 2020 can be crudely written. In the upshot, they can destroy one’s data irreversibly.
• EvilQuest
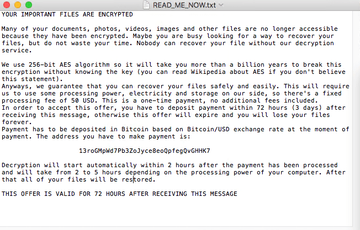
EvilQuest is an unorthodox sample of Mac ransomware that takes the data encryption route. Discovered in June 2020, it leverages a cipher strong enough to prevent private key cracking, drops a ransom note with a self-explanatory name READ_ME_NOW.txt, and instructs the victim to pay $50 in Bitcoin. Seems like a pretty standard tactic so far, doesn’t it? However, there is one thing that sets EvilQuest apart from other strains.
Shortly after this nasty made its debut, researchers found that its extortion strategy was basically a curtain for sneaky data-stealing activity. It is a modular threat that additionally deposits components for keystroke logging and information harvesting. When the latter comes into play, the victim’s personal documents, databases, cryptocurrency wallets, and backups are retrieved and sent to threat actors’ servers.
To top it off, the original version of EvilQuest would mention the exact same Bitcoin address for different users in its recovery how-to. This means that its operators couldn’t work out who paid and who didn’t, hence the decryption appeared to be impossible. There have been no reports about later releases of this infection that act differently, so it still maintains a status of an undercover data-stealer.
• ThiefQuest
An EvilQuest spin-off dubbed ThiefQuest follows in the footsteps of its precursor when it comes to the hybrid tactic. It also looks like a competently tailored ransomware species with flawless cryptographic implementation under its hood, but with the caveat that extortion doesn’t appear to be its ultimate objective.
Judging from the presence of modules geared toward collecting user data, holding files for ransom isn’t ThiefQuest authors’ first priority. As is the case with its predecessor, the Bitcoin address used for ransom payments is static. This is a clue suggesting that those infected won’t get their decryption key even after coughing up the money.
The blackmail narrative of the READ_ME_NOW.txt ransom note comes down to demanding $50 worth of Bitcoin that must be paid within 72 hours. The amount is unusually low, too – that’s one more hallmark of an info-stealing Trojan camouflaged as ransomware. Perhaps this outbreak was a test run to check the viability of a modular strain with multi-pronged functionality. Time will tell. As of April 2021, this campaign is in a state of hiatus, and it will hopefully stay that way.
• REvil
• Search Baron
• Search Marquis
Browser-only Mac extortion scams
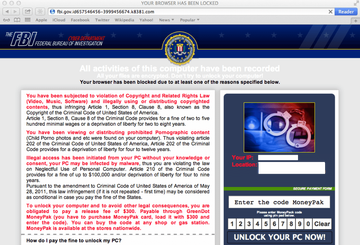
Browser lockers represent yet another common type of ransomware zeroing in on Mac computers. These threats are less severe than data-encrypting infections because they only impact Safari web browser. Technically, these are stubborn hijackers that prevent the victim from visiting any site other than a spoofed FBI or police alert page. The extortion plot revolves around false allegations about electronic felonies supposedly committed by the user. The goal is to hoodwink the user into paying a “fine” for purportedly distributing prohibited or copyright-protected materials. Fortunately, the fix is simple in this scenario. All it takes is clearing Safari cache and website data. If the victim isn’t very tech-savvy, though, they run the risk of falling for this scam.
Whether you are confronted with Mac hijack assault via Find My iPhone (Find My) feature abuse or a file-encrypting Mac ransomware attack, it’s a serious predicament that causes a great deal of trouble. To avoid the former, most widespread, type of blackmail, it’s recommended to follow a few simple rules: use a hard-to-guess Apple ID password, never reuse it for other accounts, and enable two-factor authentication for your iCloud account. If the attack has taken place, you should apply a combo of troubleshooting techniques, including iTunes password reset and the use of effective security software.
Unlock Apple device hacked and held for ransom
As per the anatomy of this con, an efficient workaround is to reset the iCloud login credentials. To do this, go to iforgot.apple.com on a computer or other non-infected device and follow the steps below:
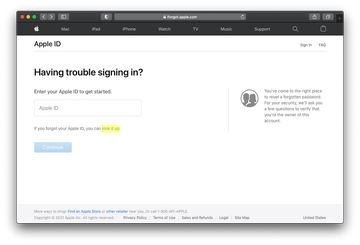
- Select the option that suggests looking up your Apple ID if you forgot it.
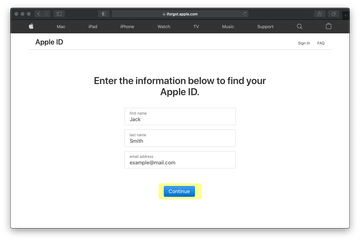
- Enter the requested details, including your first name, last name and email address and click Continue.
- Follow any further directions until you reset your iCloud password. In some cases, you may have to give Apple Support a phone call to explain your issue and get the reset job completed.
- Use the new password to regain access to your iOS or macOS device.
Unlock Safari infected by a Mac screen locker
To stop this scam in its tracks, some Safari settings should be restored to their default values. The overview of the steps for this procedure is as follows:
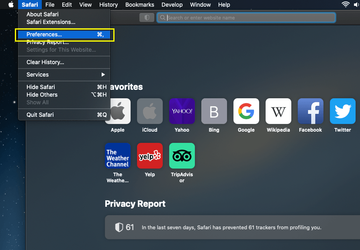
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
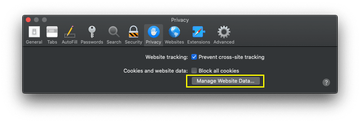
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove All button
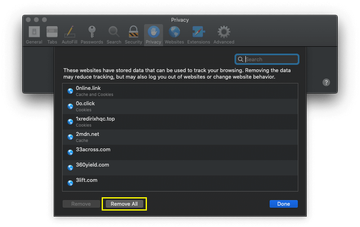
- Click the Done button to exit.
Get rid of Mac ransomware 2021 using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Mac ransomware virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Mac ransomware issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
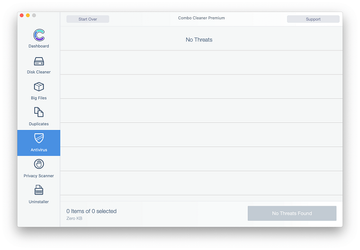
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
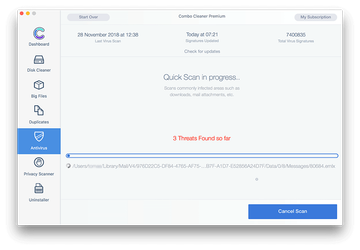
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Mac ransomware threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
