A high-profile cybercrime clique raided the networks of Apple business partner Quanta Computer and now wants a huge ransom for nondisclosure of stolen data.
On April 20, cybercrooks in charge of the REvil ransomware operation updated their dark web site with information about a successful assault against Quanta Computer, a Taiwan-based Apple partner that manufactures MacBook Air, MacBook Pro, and Apple Watch devices. Also referred to as Sodinokibi, this extortion crew gained notoriety for sucker-punching major businesses. In the aftermath of the Quanta breach, the criminals have allegedly stolen a lot of sensitive materials, including drawings of MacBook parts as well as personally identifiable data of the supplier’s staff and clients.
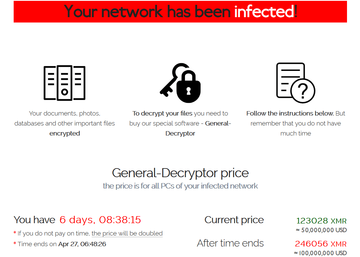
A jaw-dropping ultimatum
To keep the illegally obtained information from being leaked via REvil’s “public shaming” site on the dark web, Quanta Computer was instructed to pay $50 million worth of XMR (Monero cryptocurrency) within a six-day deadline. Afterward, the ransom would double. When the victimized company refused to cooperate, the felons uploaded a part of the blueprints to their dark web resource and threatened to put it up for sale unless their demands were met.
The noncompliance of the original target apparently made the REvil group switch to a plan B and extort Apple that should be interested in keeping its proprietary schematics secret in the first place. The payment is now due May 1 – in the meantime, the attackers are reportedly leaking files in small portions as an element of extra pressure. At the time of this writing, there are no updates regarding the Cupertino company’s response to the outrageous blackmail attempt. Quanta has admitted to being compromised but stated that its threat mitigation mechanisms have prevented critical IT infrastructure elements from being impacted.
More questions than answers
It is unknown at this point how exactly the riff-raff infiltrated the networks of the major Apple supplier. In past incidents orchestrated by these threat actors, though, the common entry points included RDP hacking, phishing scams, and intrusion upon the systems of managed service providers (MSPs) working with the primary targets.
Also, there are no reports so far that would shine the light on Apple’s reaction – whether or not the tech giant is in a dialogue with the perpetrators, and how sensitive the pilfered records are. The new deadline is around the corner, so things might get clearer in the coming week.
