Researchers discovered an offbeat malware sample arriving at Mac and Linux machines through a booby-trapped package on npm software hosting service.
Malicious code disguised as a piece of legitimate software is nothing new, but in a recently unveiled attack chain, threat actors took it up a notch. Last weekend, analysts at US-based DevOps automation firm Sonatype came across an unorthodox malware strain uploaded to npm, a free JavaScript code sharing platform that’s part of GitHub.
The harmful entity mimicked a popular open-source JavaScript programming package called “browserify”, which allows developers to create NodeJS browser modules and boasts over a million weekly downloads. The knock-off tool, “web-browserify”, contained a series of legitimate npm instruments concealing a unique binary tailor-made to run on Mac and Linux systems. At the time of this writing, the copycat package is no longer available on npm.
Multistep infection process cloaking a dangerous executable
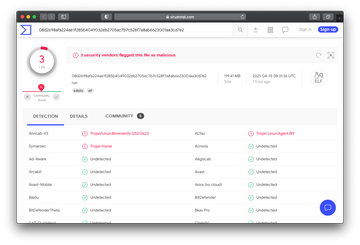
The brandjacking foul play featuring the rogue “web-browserify” bundle involved a 27-megabyte TGZ archive uploaded to npm. When an unsuspecting would-be victim developer downloaded and opened this file, it would trigger a dodgy binary in Executable and Linkable Format (ELF) supported by Mac and Linux devices alike. Unlike typical malicious binaries out there, this object (named “run”) is huge, taking up more than 100 MB. Furthermore, it contains numerous trusted npm tools, which explains why it bypasses macOS defenses and still has a minuscule detection rate across the third-party AV spectrum, as illustrated on the screenshot above. The threat is also VM-aware and therefore evades virtual machine environments to stay undetected.
The malware acts as an info-stealer, for the most part
When deployed on a developer’s computer, the malware runs several commands to terminate critical OS processes and tries to completely erase the “/etc/” folder, which is one of the core elements of a Unix-based system. The multiple modules under the toxic ELF binary’s wrapping then harvest various kinds of device information, including the installed software, hardware specifications, usernames, and more. Then, the culprit sends out these details to its operators by establishing a connection with a remote server.
With the motivation behind data theft being as clear as crystal, it remains a mystery why the infection attempts to disrupt the normal functioning of the host system through the above-mentioned “/etc/” directory wiping maneuver. That said, the big picture regarding this sample’s evil potential may become evident as further research is performed.
