Operators of the OSX/MacOffers Mac adware family have duped Apple’s automated security checks into notarizing six rogue apps posing as Flash installers.
App notarization is Apple’s software auditing technique focused on extensively vetting code before it ends up in the Gatekeeper whitelist. Adopted earlier this year, it requires developers to submit their apps for in-depth automated inspection aiming to look for signs of malicious behavior. If a piece of software passes these checks, it can be executed seamlessly with a single click of a mouse on macOS 10.15 Catalina and macOS 11 Big Sur, with the latter expected to roll out in the coming weeks.
Whereas the idea is commendable, the implementation is far from immaculate. 2020 has seen at least two slip-ups of this vaunted technology, where cybercriminals managed to dupe Apple into notarizing apps that don’t belong inside a healthy Mac.
Adware camouflaged as a Flash installer
The latest bypass plot was spotted on October 21, 2020. Researchers for the Mac protection software publisher Intego came across six notarized apps which, when run on systems, would install a sample of adware known as OSX/MacOffers. All of these booby-trapped entities were disguised as an Adobe Flash Player installer.
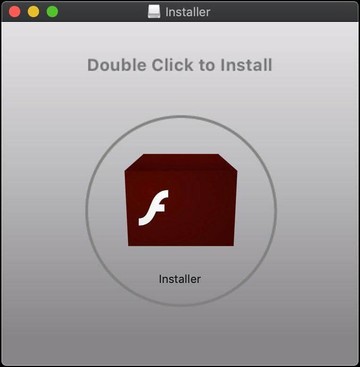
Using faux Flash updaters is an old trick that has backed numerous adware campaigns over the past years. Crooks set up rogue web pages or inject dodgy scripts into legitimate sites to display misleading pop-ups to visitors stating that their version of the Flash Player is out of date and an update is required to surf the web properly.
However, the resulting bundle installs unwanted extras that show annoying ads or take over the browser preferences. The above-mentioned OSX/MacOffers, for instance, changes the victim’s search engine without asking and makes it highly problematic to revert to the correct set-ups.
It remains unclear how exactly malicious actors managed to prevent the notarization checks from raising red flags on their shady code. The good news is, Apple de-notarized all the six pseudo-installers for Flash before the white hats reported their findings to the Cupertino company’s security teams.
This has happened before
The recent incident isn’t one of a kind. In late August, analysts unveiled a plot in which adware distributors circumvented Apple notarization controls to push through multiple samples of the Shlayer Trojan. This is another infamous Mac adware lineage that quietly installs a proxy tool to monitor and modify a victim’s Internet traffic. Such privileges are mainly weaponized to reroute web browsers to bogus search services via sketchy advertising networks.
As was the case with the OSX/MacOffers trickery, the Shlayer outbreak hinged on adware-riddled Adobe Flash Player installers. When alerted to the wrongful notarization, Apple promptly revoked its seal of approval for those harmful apps.
The fact that the story has reoccurred means that there is a loophole in the notarization scheme that can be exploited by malicious third parties. Hopefully, Apple will figure out where the weak link is and will harden its defenses against such hoaxes sometime soon.
Another thing to consider is that Adobe will discontinue support of the Flash Player at the end of this year. Modern web browsers are already using alternative proprietary solutions that work flawlessly. Therefore, Mac users are strongly advised against installing Flash updates when a pop-up instructs them to – this is a telltale sign of an adware attack.
