Find out what types of coronavirus themed scam emails are currently doing the rounds so that you can easily identify these hoaxes and avoid being defrauded.
Never before has modern civilization been confronted with a challenge as serious and impactful as the global outbreak of the coronavirus. Amidst the pandemic, the “stay at home – stay safe” motto and the social distancing principle have become synonymous with physical well-being. It comes as no surprise that millions of people are immersing themselves deeper into the online world, only to be increasingly exposed to online scams and realize that the isolation might be an illusion of safety to a certain extent.
As if the catastrophic consequences of the crisis weren’t enough, malicious actors don’t mind seizing the moment to spread digital mayhem under the guise of up-to-date COVID-19 statistics or new illness cases nearby. They are shelling users with fake emails that impersonate trusted healthcare authorities and try to dupe recipients into clicking a malicious link or open a malware-riddled attachment.
The worst part is that everyone is potentially vulnerable to these frauds no matter if they use a Windows PC or a MacBook boasting decent built-in defenses. Whereas Macs are less likely to be infected with email-borne malicious programs, phishing works indiscriminately and therefore Apple fans run the risk of inadvertently disclosing their sensitive information such as the Apple ID and credit card details. Keep reading to familiarize yourself with the common ways cybercrooks are pilfering personally identifiable data under the smokescreen of the COVID-19 scare.
“Safety measures” phishing campaign
To execute this scam, malefactors are sending fake emails impersonating the World Health Organization (WHO). The bait is a button embedded in the message body that says “Safety measures” and supposedly leads to a downloadable document containing the entirety of coronavirus precautions. Once clicked, though, the link opens a faux email verification form where the user is instructed to enter their credentials.
To make the swindle appear persuasive, the attackers include the logo of the United Nations public health agency in the message. However, there are primitive spelling mistakes in the text that outweigh the scammers’ attempt to mimic a real advisory from the WHO. It’s worth mentioning that the “Safety measures” fraud can assume somewhat different forms. Another common variant is an email impersonating a medical expert from Wuhan, China – the place where the COVID-19 infection originally took root.
“New cases around your city” CDC alert scam
The subject of this scam email pulls the strings effectively enough to hoodwink users into making a mistaken click. The message pretends to come from the Centers for Disease Control and Prevention (CDC), a U.S. federal agency specializing in health protection. The lure is a link that allegedly points to a page listing new coronavirus cases in the recipient’s area. Instead, it forwards the victim to a phishing page asking for personal info.

Coronavirus themed BEC scam
BEC stands for “business email compromise” and denotes a fraudulent technique where an adversary passes himself off as a company executive and instructs employees to wire funds to a wrong account. The scam in question, though, is a little more complex than that and includes an extra layer of manipulation. The social engineering attack starts with an email sent to an organization’s finance department employees asking them to send back an “aging report”. This is a list of overdue invoices generated for unpaying customers.
Once this database is at the crooks’ disposal, they contact people who owe money to the firm. The scam email says that the company is switching to another bank due to the COVID-19 pandemic and tells recipients to wire their debts to a different account, which is actually a Hong Kong based mule account.
The phony COVID-19 infection map trick
The operators of the notorious password-stealing Trojans dubbed AZORult are parasitizing the fact that numerous users want to stay tuned for coronavirus stats. Specifically, they are spreading the pest under the veil of a dashboard app that reflects live data regarding the geographic distribution of the disease. The mechanisms used to serve the contagious map application include malicious websites and quite likely spam emails.
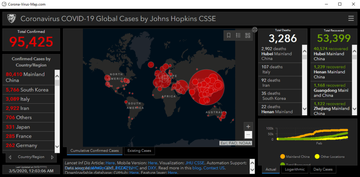
The fake map is a replica of the well-known resource set up by John Hopkins University. It even fetches data from its authentic counterpart to appear true-to-life. However, when launched, the dubious process called Corona-Virus-Map.com.exe executes a series of commands to run AZORult in the host environment. The Trojan captures the victim’s screen at random and pilfers passwords along with cryptocurrency wallet information. The harvested data goes to the criminals’ C2 server.
“Emergency Regulation Ordinance” hoax
Lokibot is one more info-stealer whose operators are boiling their distribution practices down to the pandemic theme at this point. The fraudulent emails spreading this nasty impersonate the Ministry of Health of the People’s Republic of China. The subject of these messages is “Emergency Regulation Ordiance [sic] Against Coronavirus” (note the typo). The unnerving thing is that this stratagem focuses on compromising organizations as the message includes the phrase “for the safety of your industry”.
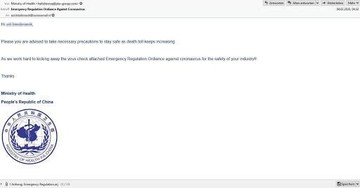
The emails contain an attachment in ARJ compressed file archive format. Once opened and unpacked, this item turns out to have a batch file inside named “Emergency Regulation” which, in turn, executes Lokibot on the computer. The Trojan instantly starts collecting the victim’s credentials and sends them to its Command and Control server.
The bottom line
As secure as macOS inherently is, it’s not entirely foolproof. Human error is the main vulnerability exploited by cybercriminals at the helm of COVID-19 themed scams. Under the circumstances, online hygiene is an important prerequisite for staying safe in these tough times. To avoid the common frauds currently in rotation, Mac users should ignore online requests for credentials, keep an eye on spelling and grammar errors in emails, stay away from messages that impose pressure or urgency, and only resort to official sources of information about the pandemic.
