Read previous part: A Mac OS X Rootkit Uses the Tricks You Haven’t Known Yet 3 - Benefits of the Host Privilege
At the end of their talk, TT and Nanika outline a method to gain root permission on Mac OS X and present their tool called System Virginity Verifier (SVV-X).
A Trick to Gain Root Permission
Alright, all the tricks that we showed basically require some privilege, at least the host privilege. For our rootkit, you still need at least one time to be root. I am going to show you a trick that can easily get root permission.
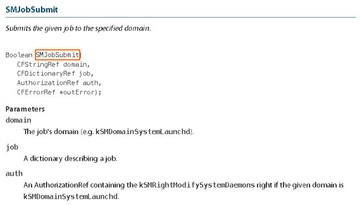
So, basically, when an application requires a permission, such as installation for instance, it will use this API to obtain authorization from securityd. By using this API, you can get authorization and you will have permission to do things.
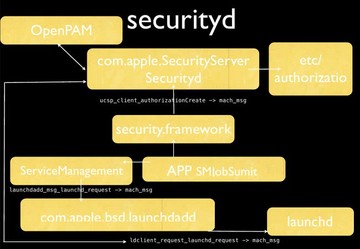
So, an app will call this function (SMJobSubmit) to request the permission from securityd. And securityd will load the configuration from here (etc/authorization) to know which permission is required. And securityd will pop up a message to ask the user to type the password. After the password is typed, securityd will return a token to the application. With this token, the application can start doing something with permission. And launchd will use another permission to launch the application.
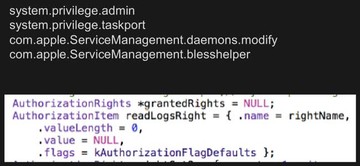
There are many authorization combinations, and you can choose what kind of authorization you need. You just specify which one you need – and you can get the authorization if the user types the password.
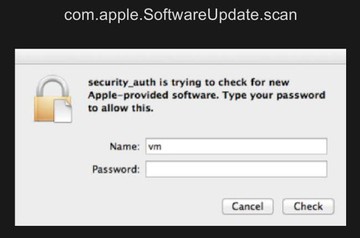
There is one combination that’s very interesting. It’s com.apple.SoftwareUpdate.scan. This application is trying to check for new Apple-provided software. You need to type your password to allow this. After the user types the password you can get the permission. I think most users will type this particular password. So, this is a trick that malware developers can use to get permission.
Conclusion
Okay, the conclusion.
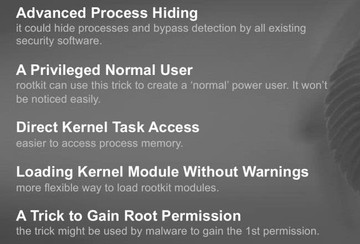
Today we introduced advanced process hiding tricks. In particular, we introduced application control from user mode. If you want to hide a process you have to deal with not only kernel, you have to deal with user mode as well. We also introduced a privileged normal user. Actually, in Mac OS kernel the permission control is very complicated, so I think there are still many things you can try to do. With host privilege we can do many things, you don’t have to be root. Maybe the administrator will not feel anything weird if you are just a normal user when you rootkit is installed on the system. Also, we introduced a new way to directly access kernel task, and it is a very easy way to access kernel memory. Furthermore, we introduced a method of loading kernel module without warnings; and also tricks to gain root permission.
System Virginity Verifier for Mac OS X (SVV-X)
There is one more thing, not only the rootkit tricks. We are developing System Virginity Verifier for Mac OS X. You know on Windows there is SVV released in 2006 or 2007, I don’t remember exactly. It is, basically, a rootkit checker to check whether your kernel has been modified by a rootkit. So we are developing this tool and we are going to give you a preview of this tool.
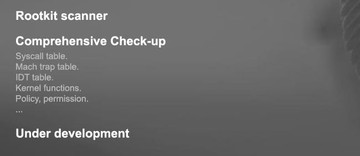
This tool is, basically, a rootkit scanner and it performs a comprehensive checkup. It checks system call table, trap table, IDT table, kernel functions, policy permission, and network. So, we check everything that might be used by a rootkit. But this is under development. We are giving you a demo now.
This is the way we monitor process creation. Now we use our tool to scan the kernel. It checks syscall, mach trap, IDT table, and kernel function. The execsnoop is monitoring the process creation, so it will insert some hook in the kernel. We used our tool to check this hook and it discovered the hook. We got two alerts, which means two hooks were discovered.
Okay, that’s it. Thanks for attending and thanks for listening!
