Learn how to fix the Rackcdn virus Mac problem, where the web browser is repeatedly forwarded to a fake threat alert page pushing a rogue system utility.
A web browser is the most heavily exploited area in Mac malware distribution campaigns. That’s probably because this environment is the lowest-hanging fruit compared to the rest of the operating system’s components, which is on the plus side of Apple’s platform security in general but still a cold comfort for those who fall victim to such attacks. The users experience a harsh tampering with their web surfing activity, typically manifested as browser redirects accompanied by irritating popups. One of the long-running waves of such malicious code propagation involves the rackcdn.com domain, which is part of a content delivery network provided by American cloud services company Rackspace. By “weaponizing” the reputable online infrastructure, the malefactors make sure that their fraud campaign isn’t interrupted as part of commonplace browser security practices.
The raid stems from an infiltration of a harmful browser plugin into the Mac. This is usually a matter of bundling, a software promotion method originally designed to be benign but also notorious for being a source of malware trespassing on computers. The crooks cook up complex setup clients that install potentially unwanted applications (PUAs) alongside inoffensive ones. Therefore, when getting themselves some new free and useful program Mac users should pay close attention to the items that hide underneath the default install. Thankfully, it’s easy to do – just peek into the custom options and take a look at the items listed there. If there is one that seems suspicious, but sure to uncheck it right away. Zooming back in, the attack commences with a wrongdoing element being added to one’s browser, which instantly modifies a number settings and starts redirecting Safari, Chrome, or Firefox to rackcdn.com domain without the victim’s consent.
Rackcdn hijacker may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
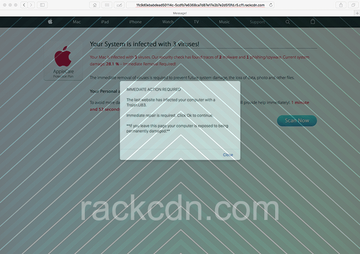
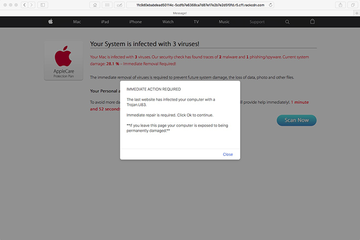
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.In the resulting URL string, the rackcdn.com part will be prepended with numerous hexadecimal characters and a fragment like “r5.cf1” while being concatenated with many more gibberish characters. So, the address bar will be in the following format: [random].r5.cf1.rackcdn.com/[random]. Note that the number in the prefix may vary. The redirect activity will be going off in a haphazard way and accompany some standard actions of the user, such as opening the browser, running a web search or triggering a new tab. When on the landing page, the victim will see a warning allegedly from AppleCare Protection Plan that says, “Your system is infected with 3 viruses!” The spoof site also provides details about the pseudo predicament, emphasizing that the current system damage is 28.1% due to the misdemeanor of 2 malware and 1 phishing/spyware samples.
Furthermore, there will likely be a popup alert going, “Immediate action required. The last website you visited has infected your computer with a Trojan.U83. Immediate repair is required. Click Ok to continue”. The footnote about the Mac’s exposure to being “permanently damaged” if the victim leaves the page is supposed to add more pressure to the brainwashing. Ultimately, by opting into what the rackcdn.com scam wants, the user runs the risk of downloading and installing a Mac scareware application, such as Mac Cleanup Pro. This secondary payload will only make matters worse as it will display noxious scans reporting imaginary system performance issues and inexistent threats in order to fool the victim into buying the full version in exchange for the fix. It goes without saying that users shouldn’t fall for this scam. Instead, it’s strongly recommended to remove rackcdn virus from Mac.
Rackcdn virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
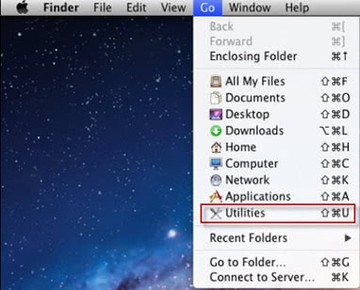
- Open up the Utilities folder as shown below
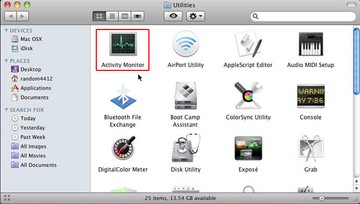
- Locate the Activity Monitor icon on the screen and double-click on it
- Under Activity Monitor, find a suspicious entry, select it and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
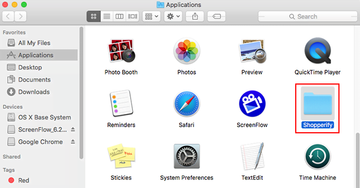
- Click the Go button again, but this time select Applications on the list. Find the potential pest on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it
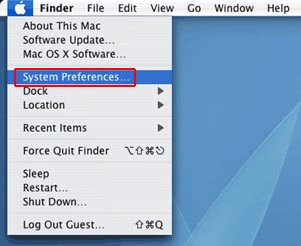
- Now go to Apple Menu and pick the System Preferences option
- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the computer is started up. Locate the infection there and click on the “-“ button
Get rid of browser redirects to rackcdn.com
To begin with, settings for the web browser that got hit by the rackcdn.com hijacker should be restored to their default values. The overview of steps for this procedure is as follows:
- Reset Safari
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
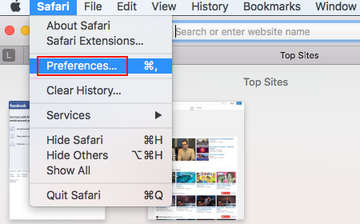
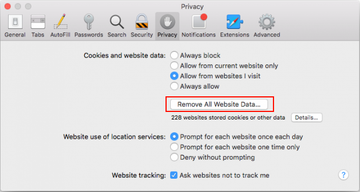
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Remove All Website Data and click on it
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove Now button
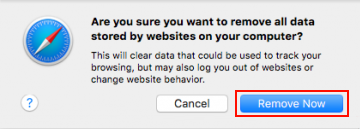
- In order to selectively clear data generated by certain websites only, not all of them, hit the Details button under the Privacy section of Safari Preferences

- This feature will list all websites that have stored potentially sensitive data, including cache and cookies. Select the one, or ones, that might be causing trouble and click the appropriate button at the bottom (Remove or Remove All). Click the Done button to exit.
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Reset Google Chrome
- Open Chrome, click the More (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
- Scroll down to the Reset settings section. Under the Restore settings to their original defaults option, click the Reset settings button
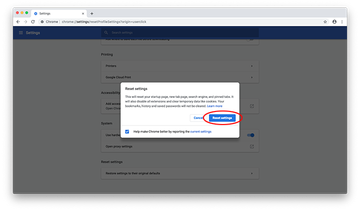
- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Reset Mozilla Firefox
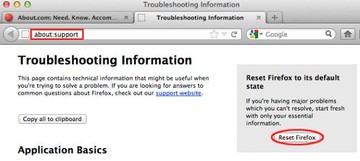
- Open Firefox and select Help – Troubleshooting Information
- On the page that opened, click the Reset Firefox button
Get rid of rackcdn virus Mac using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Rackcdn hijacker virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Rackcdn hijacker issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
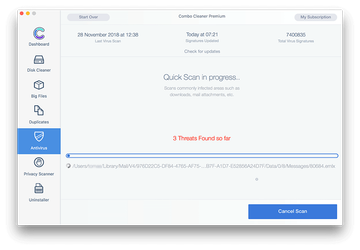
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
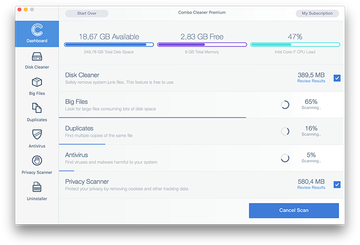
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
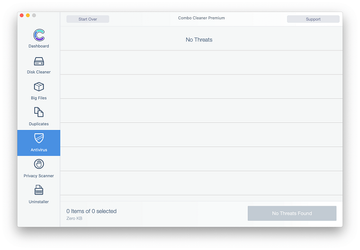
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Rackcdn hijacker threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.