Reviews
Best proxy providers for teams with shared access, whitelisting, and controls
When multiple people need to access the same web resources proxies quickly become a team dependency.
Top SaaS application development companies you can trust
Looking for a reliable SaaS development partner? Explore our list of top SaaS application development companies known for delivering scalable, high-quality solutions.
10 best video editing software for Mac (iMovie alternatives)
Find the best Mac video editing software for your needs. Edit videos on Mac with powerful tools like iMovie for Mac.
MacKeeper review 2023
Read the MacKeeper review encompassing a detailed evaluation of its features, support, usability and effectiveness in optimizing and protecting Mac devices.
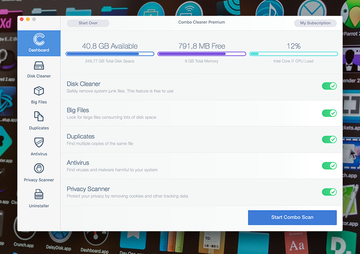
Combo Cleaner for Mac review
This Combo Cleaner review gives informative insights into the app’s Mac optimization and antivirus features while singling out its main pros and cons.
Private Internet Access VPN review
Using Private Internet Access VPN is a sure-shot way to curb eavesdroppers, avoid geo-discrimination, and generally surf the web with peace of mind.