Find out what kind of an infection the Default Products Mac app is, how it contaminates systems, and what removal techniques stop this attack in its tracks.
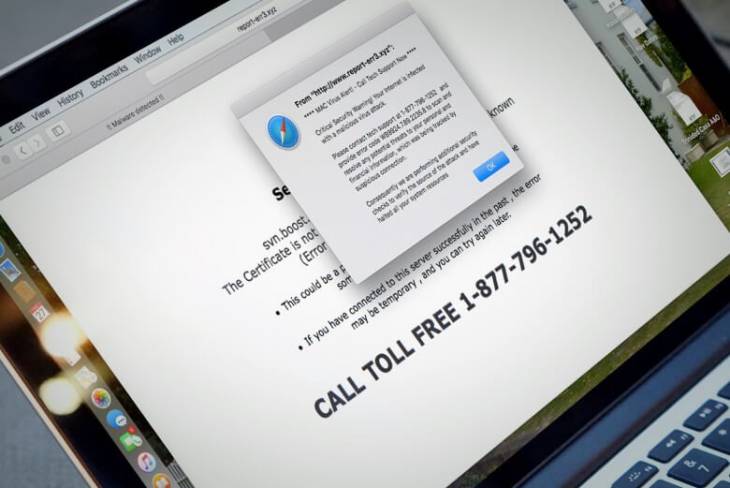
Whereas the adverse effects of adware are comparatively mild due to the attack being mostly isolated to one’s web browser, the stratagem is definitely a thorn in the victim’s side. It tends to be accompanied by intolerable popups and web traffic redirects that badly diminish the online experience of anyone infected. A recent upswing in this type of dodgy activity has spawned a slew of lookalike malicious apps that share quite a few common traits. The one called Default Products, also known as DefaultProducts 1.0, falls into this particular category. It infiltrates computers using a freeware bundling hoax that cloaks the junk payload beneath its ‘express’ option. Similarly to the other PUPs (potentially unwanted programs) from the same lineage, including WindowGroup and Premium Forward, this culprit uses a round green icon with a magnifying glass image in it. It’s hard to think of more verbose evidence of cross-adware affiliation in this case. This is just an external resemblance, though, with quite a few more unsettling quirks lurking under this ostensibly garden-variety wrapping.

The Default Products Mac app also takes after its dubious replicas in terms of the persistence and browsing distortion tactics. It configures the host system to launch its harmful process at boot time, plus it adds a rogue user profile to ascertain that the genuine admin account lacks privileges to close the misbehaving executable. When first launched, the adware installs a new extension called DefaultProducts 1.0 in the built-in Safari browser. It can also embed its add-on in Chrome and Firefox versions tailored for Mac. This impostor ‘helper object’ defiantly gets permissions to read sensitive data from all web pages without even triggering an appropriate request. It means the victim’s passwords for accessing personal Internet accounts and information like credit card numbers as well as full browsing history are potentially at risk.
Another realm where the Default Products Mac virus abuses these elevated privileges is all about advertising. By harvesting personally identifiable data about the infected user, it acquires details that suffice to serve targeted ads. Numerous instances of sponsored information labeled “Ads by DefaultProducts” are going to be injected into nearly every website the victim goes to, including regular news pages and search engines. Speaking of which, this adware claims to be a search enhancement tool of some sort. Instead, it recurrently forwards the user to a fake search provider that primitively leads to Yahoo or Bing results pages with adverts sprinkled all over them. When such a redirect is underway, it ‘touches’ a few ad networks as part of a filthy monetization strategy.
The victims may additionally visit tech support scam sites or trojanized software update pages due to the shenanigans of this pest. The goal of this foul play is to hoodwink the users into paying to fix an inexistent Mac problem, or to download a pseudo update veiling more malware. At the time of writing, the Default Products virus issue is making itself felt the most in the German community of Mac users. Its geographic focus demonstrates one more element of adware evolution. When the contaminated users realize that something isn’t right and get down to eradicating the source of the predicament, they run into a stumbling block: the adware doesn’t allow them to uninstall it easily. The following section of this article will help get around this perseverance quirk of the infection and remove completely.
Default Products app manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
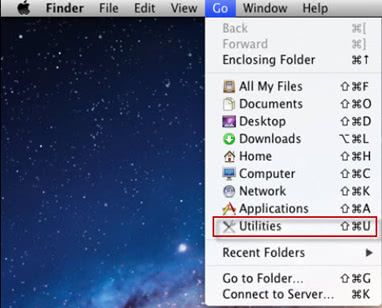
- Open up the Utilities folder as shown below

- Locate the Activity Monitor icon on the screen and double-click on it

- Under Activity Monitor, find Default Products (DefaultProducts) or some other item that appears suspicious, select it and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
- Click the Go button again, but this time select Applications on the list. Find the DefaultProducts entry on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it

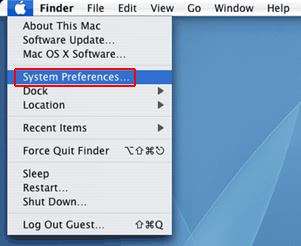
- Now go to Apple Menu and pick the System Preferences option

- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the box is started up. Locate Default Products (DefaultProducts) or other potentially unwanted app there and click on the “-“ button
Get rid of Default Products ads and redirects in web browser on Mac
To begin with, settings for the web browser that got hit by this virus should be restored to their default values. The overview of steps for this procedure is as follows:
- Reset Safari
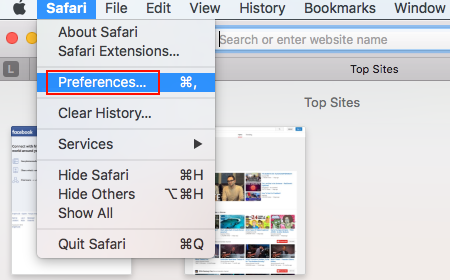
- Open the browser and go to Safari menu. Select Preferences in the drop-down list

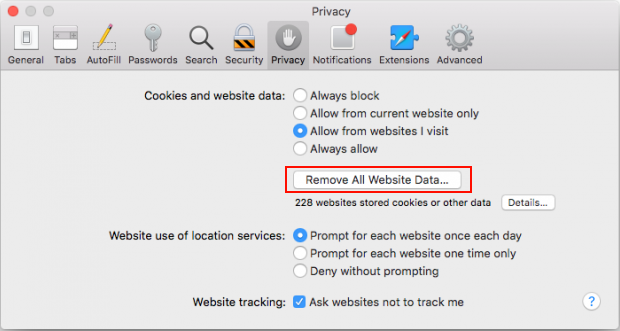
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Remove All Website Data and click on it

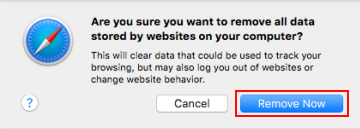
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove Now button

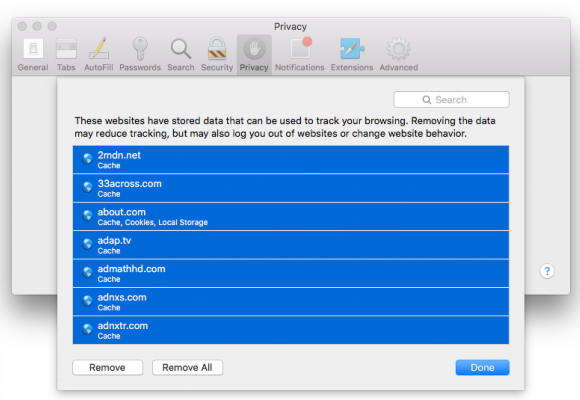
- In order to selectively clear data generated by certain websites only, not all of them, hit the Details button under the Privacy section of Safari Preferences

- This feature will list all websites that have stored potentially sensitive data, including cache and cookies. Select the one, or ones, that might be causing trouble and click the appropriate button at the bottom (Remove or Remove All). Click the Done button to exit.
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Reset Google Chrome
- Open Chrome, click the More (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
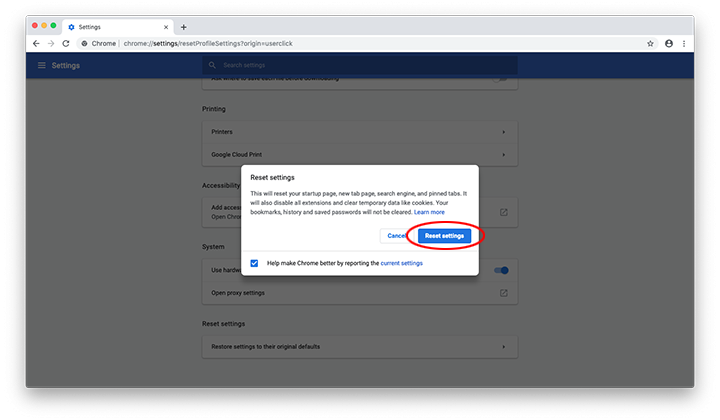
- Scroll down to the Reset settings section. Under the Restore settings to their original defaults option, click the Reset settings button

- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
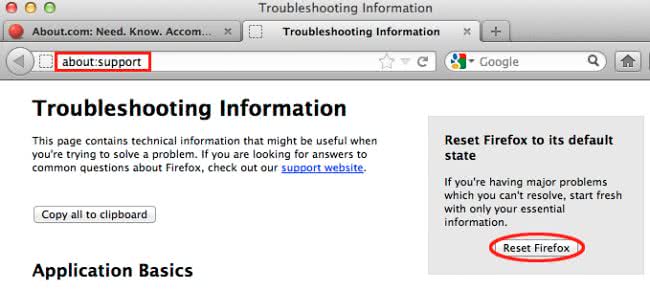
- Reset Mozilla Firefox
- Open Firefox and select Help – Troubleshooting Information
- On the page that opened, click the Reset Firefox button

Get rid of Default Products virus using Combo Cleaner automatic removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Default Products virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Default Products issue using Combo Cleaner:
- Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
- Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
- Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.

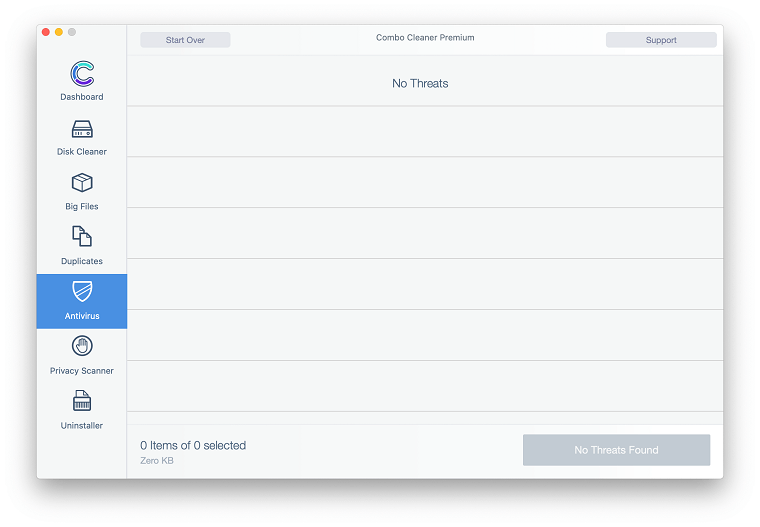
- Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).

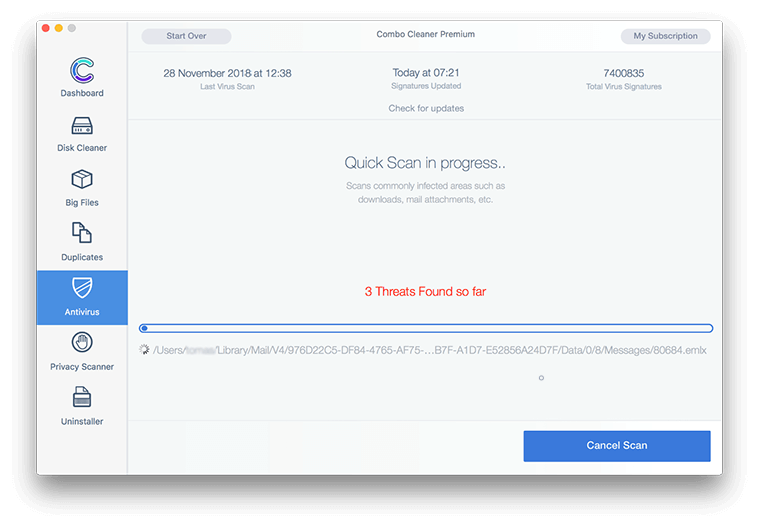
- In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Default Products threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.

- Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.