As 2022 is now in full swing, let’s look back on the eventful 2021 under the angle of groundbreaking and unusual Mac threats that splashed onto the scene.
Hello, 2022. And a farewell to you, 2021. Traditionally, the dawn of a new year is a good time to reminisce about the moments that made the precursor stand out. Since we are a security crew focused on monitoring the threat landscape around Apple’s laptops and desktops, the best recap we can do is all about malicious code that zeroes in on Macs. While scores of previously known Trojans, malware, and adware strains maintained their footprint in this area over the past 12 months, a few offbeat campaigns were launched and truly made a difference.
Now, a quick spoiler. Most of the newbies are geared toward extracting sensitive user data from computers with the Apple logo, which showcases one of the prevailing cybercrime trends we’re in for: personal information is a valuable asset growingly targeted by malefactors. Without further ado, here is a summary of last year’s macOS-haunting nasties that paved the way for the increasing sophistication and stealth of cybercriminals’ Tactics, Techniques, and Procedures (TTP). For the sake of tidiness, the list is arranged in chronological order.
• ElectroRAT
As the name suggests, this is a Remote Access Tool, and as such, it is aimed at establishing an unauthorized connection with an infected system. Generally, this type of activity may pursue various objectives, but in the case of ElectroRAT, the primary goal is to steal data from victims’ cryptocurrency wallets. It spreads under the guise of ostensibly useful applications touted on popular blockchain-related discussion forums. One of these undercover programs is called eTrader.
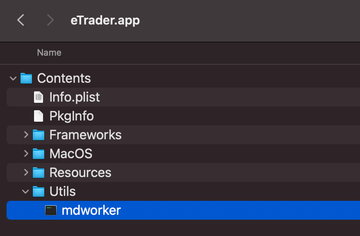
When running inside a Mac, the culprit executes a binary named “mdworker” to do its thing. As part of a persistence methodology, it adds a .plist file to the LaunchAgents directory, which makes the system trigger the main executable during each log-in instance. The predatory app also queries a Pastebin page to fetch the IP address of its Command and Control (C2) server and then submits some basic details about the plagued Mac, including the operating system version and username.
Once the covert connection is active, ElectroRAT is all set to receive instructions from its masters. For instance, it can be “told” to upload and download arbitrary files, run commands, record keystrokes, take images with the machine’s built-in camera, and perform different kinds of backdoor activity. Because it propagates via rogue posts on cryptocurrency forums, coin wallet credentials are a common form of valuable information at stake.
• Silver Sparrow
First spotted in mid-February last year, Silver Sparrow is unique in several ways. The most striking peculiarity is that this malware was compiled to run natively on machines with Apple Silicon inside. For the record, this system on a chip (SoC) architecture – also known as M1 ARM64 – had only been around for a few months before this outbreak, which demonstrates threat actors’ unmatched adaptability in light of new circumstances.
The fact that Silver Sparrow is M1-compatible isn’t the only thing that sets it aside from garden-variety macOS malware. At the time of discovery, the baddie was detected on a whopping 30,000 computers. That’s a huge number of hosts for a brand-new strain to infect in one go. In addition, its installer “updater.pkg” uses a JavaScript API to execute commands, which is very uncommon for Mac perils out there. The associated launch agent sets off a script named “verx.sh” with predefined intervals (one hour in most cases) to check in with the C2 server.
Analysts haven’t been able to determine the exact infection vector used by the operators of this program. Perhaps the weirdest thing, though, is that the original variant of Silver Sparrow didn’t drop any payloads onto contaminated Macs, making the whole campaign kind of pointless. However, it could have played a trickier role of probing M1 devices for security gaps. Time will tell whether crooks will weaponize their findings going forward.
• XcodeSpy
It is common knowledge that most crooks try to maximize their attack surfaces by keeping the number of infection criteria low. The rationale is as follows: the more users are hit, the more gain. The malware dubbed XcodeSpy is different because the range of its intended victims is limited to software developers. Its authors concentrate on riddling open-source Xcode projects with obfuscated scripts. As a result, the instance of building one of such projects becomes a trigger for the malware to crop up on the Mac behind the scenes.
The above-mentioned scripts spawn Bash shell objects and assemble them into an offensive command. The latter is used to get a reverse shell on the malware-stricken machine, which means the malefactor can easily get around authentication and firewall barriers when infiltrating the target device remotely.
This access is mishandled to run a modified version of EggShell, a Python-based hacking tool that extends the intruder’s capabilities considerably. It allows, among other things, uploading and downloading files at will, obtaining passwords, taking photos with the Mac’s camera, and tracking the user’s location.
• ElectrumStealer
This species of Mac malware homes in on users of a popular Bitcoin wallet service called Electrum, hence its name. It somehow passed Apple’s notarization checks so that it could run on systems without any alerts. A massive outbreak occurred in early March 2021 and relied on a wave of malvertising that parasitized a supply-side platform (SSP) compromised earlier. This allowed crooks to forward users to a page pushing a knock-off Electrum wallet update.
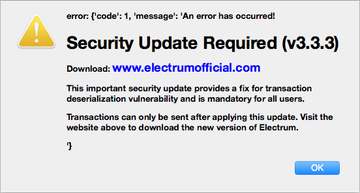
In the aftermath of this hoax, victims start using a booby-trapped copy of the wallet app. Interestingly, it’s not equipped with any particular persistence features. That’s not too surprising, though, given that people think they are using the legitimate version and routinely open the rogue software to complete cryptocurrency transactions. When up and running on a Mac, ElectrumStealer amasses passwords and other coin-related data, subsequently exfiltrating it to a server under hackers’ control.
• WildPressure
Unlike the previously described threats, WildPressure is cross-platform: it supports both macOS and Windows. Its main mission is to open up a backdoor into a target host, which is a catalyst for deep compromise. The infection entails a complete system takeover combined with a capability to upload and run second-stage payloads without giveaways.
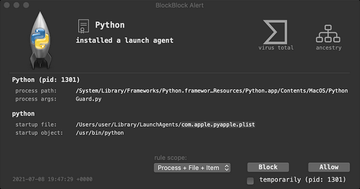
To persevere inside a new environment, WildPressure tampers with it at the level of LaunchAgents. Specifically, the baddie creates a file named com.apple.pyapple.plist inside that folder and is thereby started during every login. A feature that builds an extra layer of persistence and a sort of reconnaissance works by retrieving details about antivirus applications installed on the device so that these processes can be terminated.
Very little is known about the spreading mechanisms leveraged by WildPressure operators. The only fact in this context is that it chiefly aims at hitting organizations in the Middle East that represent the oil and gas sector. That being said, the backdoor is likely an instrument for targeted incursions.
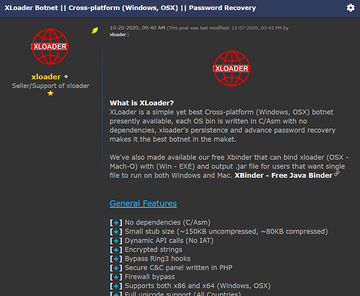
• XLoader
XLoader is believed to be a cross-platform successor of the infamous password-stealing program called FormBook, which only targeted PCs. The more versatile spin-off is advertised on hacker forums as malware-as-a-service, and therefore, the malefactors who purchase the turnkey program choose the suitable mechanisms for depositing it on computers. The kit allows criminals to create a single Java Archive (JAR) file that blends EXE and Mach-O binaries for frictionless execution in two different operating systems.
XLoader is mostly doing the rounds via phishing attacks. When inside a Mac, it adds a launch agent that activates the RunAtLoad routine so that the computer launches it at boot time. While the theft of a victim’s passwords is the main adverse effect, the malware supports plenty of other commands. It can make API calls, download files, execute applications, clear browser cookies, uninstall software, visit websites, and even reboot or shut down the infected device. The culprit surreptitiously sends out the harvested data over HTTP protocol using POST or GET requests.
• ZuRu
This unwanted application is designed to fulfill two tasks. One is to gather comprehensive information about an infected Mac, and the other is to install a popular penetration testing tool that will provide crooks with nearly unlimited access to the computer. The first outbreak took place in September 2021 and was focused on Chinese users. In this campaign, ZuRu was propagating via sponsored results in Baidu, the country’s most-used search engine.
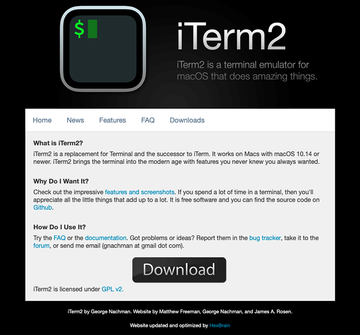
The ad led to a page camouflaged as the official website for a macOS Terminal replacement app called iTerm. When installed, this trojanized program drops a duet of payloads mentioned above. The Python-based system survey module retrieves basic information about the computer, including the Z shell (zsh) history, keychains, and hosts. Then, it exfiltrates the data in the shape of a ZIP archive.
A more dangerous payload is an executable that connects to an external IP to request a copy of Cobalt Strike, a well-known attack simulation tool widely used in red teaming and pentest exercises. It goes without saying that this action opens up a Pandora’s box of exploitation opportunities.
• MacMa
MacMa, also known as OSX.CDDS, is a technically complex, multifunctional backdoor threat that might have nation-state roots. There are several clues that suggest a high level of its sophistication. First off, it spreads via a fusion of a known exploit (documented as CVE-2021-30869) and a zero-day local privilege escalation bug. To ensure persistent execution, the sneaky parasite piggybacks on a launch daemon and a launch agent created at the early infection stage.
The harmful program comes with sophisticated sandbox evasion features to fly under the radar. The snooping capabilities of MacMa are manifold, as the backdoor downloads a handful of extra components. These helper instruments allow its authors to obtain screen captures, record the victim’s keystrokes, start Terminal sessions, run commands, uninstall apps, download or upload files, and more.
Summary
Whereas this review doesn’t fully reflect the state of the Mac malware territory, it does reveal the big picture. Cybercrooks are agile enough to adjust their attacks to whatever defenses Apple implements. Neither older machines nor high-end devices with M1 chips are safe when well-resourced adversaries step in. However, this doesn’t lessen the importance of proper security hygiene. Keep your macOS installation up to date, stick to the official App Store for software downloads, and bear in mind that protection is a systematic process requiring continuous efforts.
