Researchers have unearthed a new Mac backdoor sample in the wild that’s believed to have ties with a Vietnamese state-funded cybercrime group OceanLotus.
The unorthodox Mac malware strain with backdoor capabilities has code overlaps and shares some behavior patterns with earlier threats distributed by the OceanLotus Advanced Persistent Threat group. Also referred to as APT32, this gang is considered to have a connection with the Vietnamese authorities. It has been previously spotted in plots aiming to perpetrate industrial espionage attacks against foreign companies with offices in Vietnam, including entities from the construction, research, and media sectors.
The most likely objective of these cybercrime operations is to steal corporate secrets and allow local organizations to take a leap in adopting new technologies. The long-running macOS backdoor opens a loophole into an infected Mac computer so that its operators can quietly amass proprietary information.
Clever evasion techniques
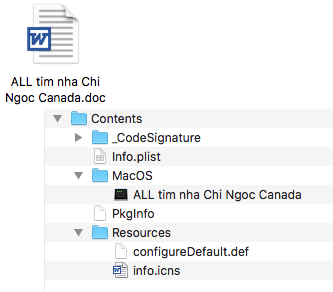
According to a write-up by the Trend Micro research team, the updated iteration of the OceanLotus group’s notorious backdoor is making the rounds via phishing emails that contain a ZIP archive cloaking a dodgy app. The fact that the filename is in Vietnamese indicates the potential range of intended victims. The malicious binary itself lurks behind a spoofed Microsoft Word icon.
Aside from trying to slip past a recipient’s attention, the payload evades detection by the operating system’s native defenses and antimalware tools. To this end, it includes a series of special characters plus three UTF-8 encoded bytes that don’t alter the visual manifestation of the app. However, the trick results in macOS interpreting the bundle as an unsupported directory object, and therefore the harmful app is triggered through the “open” command, which adds an extra layer of AV evasion to the scheme.
A multistep infection chain
When running in the background, the initial shell script tries to eliminate file quarantine limitations for the rogue DOC item. Then, it executes the app, extracts the encoded binary, modifies its access privileges, and launches the second-stage payload. To clean up the traces of the infiltration, the script removes the original app bundle.
The role of the second-stage payload is to drop another one and establish persistence in the host system by adding a malicious entry to the ~/Library/LaunchAgents folder. This paves the way for loading the backdoor component, which instantly harvests the macOS version details along with hardware specifications and submits the info to the OceanLotus Command & Control server.
The most unnerving facet of this backdoor activity comes down to downloading and uploading files, running commands in the Terminal, and executing arbitrary files. This allows the criminals to exfiltrate data from a compromised system without raising red flags and deposit other malware samples.
Security analysts claim the development of this backdoor is a work in progress and new adverse features might surface to avoid detection and enhance the persistence side of things. In the meanwhile, Mac users should exert extra caution with files and links received over email.
