With the Safari Redirect Virus running rampant in the macOS environment these days, the tips in this article will point affected users in the right direction.
| Threat Profile | |
|---|---|
| Name | Mac Safari Redirect Virus |
| Category | Mac browser hijacker, Mac adware |
| Related Domains | search.safefinder.com, search.tapufind.com, search.anysearch.net, search.chill-tab.com, search.searchpulse.net, search.landslidesearch.com, searchmine.net, qsearch.pw, searchmarquis.com, searchbaron.com, searchsnow.com, searchitnow.info, mybrowser-search.com, onclickbright.com |
| Symptoms | Redirects Safari to Bing, Yahoo or fake search engines via intermediate sites (ad networks), injects ads into search results, slows down the system |
| Distribution Techniques | Freeware bundles, fake software updates, torrents, misleading popup ads |
| Severity Level | Medium |
| Damage | Privacy issues due to Internet activity tracking, search redirects, unauthorized modification of browsing preferences, unwanted ads |
| Removal | Scan your Mac with Combo Cleaner to detect all files related to the browser hijacker. Use the tool to remove the infection if found. |
What is Safari Redirect Virus?
Choosing the most suitable web browser to use on a Mac is a matter of personal taste. While Mozilla Firefox and especially Google Chrome are growingly popular among Apple fans, Safari continues to be the app conveying the true Apple-style experience. It’s also going to get a privacy boost via the Intelligent Tracking Prevention feature, a more streamlined tab design, customizable homepage, and quite a few more perks that will debut with the upcoming macOS 11 Big Sur release. These enhancements will likely contribute to a dynamic further increase in the Safari user base. What is cybercriminals’ response to this hype? Predictably, it comes down to a steady growth in attacks honing in on this browser. Out of all adware threats circulating in this area, the Safari Redirect Virus has been dominant for years, and this trend will probably persevere.
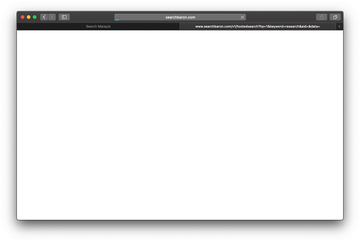
The generic name of this nasty speaks volumes about its behavior and adverse effects. It reroutes Safari to websites the user never intended to visit. To set this foul play in motion, the infection sneaks its way into a Mac as part of a freeware bundle and harnesses a dodgy extension that crops up in the browser without clear permission requests. This rogue helper object redefines custom settings, including the start page, preferred search engine, and new tab page. Additionally, the potentially unwanted application (PUA) at the heart of this interference often creates a configuration profile that specifies the way Safari works while causing an overarching system impact.
Safari Redirect Virus may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.Bing redirect virus in Safari
The Safari Redirect Virus can manifest on contaminated Macs in several different ways. One of the things that distinguishes some scenarios from others is the landing page, that is to say, the site the victim keeps hitting because of the tampering. A good deal of culprits from this pool forward the traffic to bing.com. The screen capture below demonstrates the former type in action. The intercepted web traffic goes through a rabbit hole of interstitial URLs. The most frequently encountered ones are as follows:
- searchbaron.com;
- searchmarquis.com;
- searchitnow.com;
- searchsnow.com;
- api.lisumanagerine.club;
- search.surfharvest.xyz.

The role of these domains is to manage the hijacked web traffic according to adware operators’ current monetization strategy that’s subject to regular transformations down the road. Although the auxiliary URLs can only be seen in the address bar for a split second, they are critical elements in the infection chain utilized by this spinoff of the Mac Safari Virus. The resulting service, bing.com, is used to smokescreen the dubious activity and has nothing to do with the evil plan of malicious actors who simply piggyback on its trustworthiness.
Safari Redirect leading to Yahoo
One more mainstream persona of this unruly code follows a similar logic, except that it forces hits to search.yahoo.com. The underlying PUA surreptitiously installs a Safari extension that runs with elevated privileges and replaces the user-specified web surfing settings with a sketchy address. This way, the victim incessantly visits a knockoff search engine which, in turn, resolves Yahoo. There are quite a few junk services from this cluster in active rotation. Below is a list of pseudo-providers that fit the mold of this stratagem:
- search.safefinder.com (see screenshot below);
- search.tapufind.com;
- search.anysearch.net;
- search.chill-tab.com;
- search.searchpulse.net;
- search.landslidesearch.com;
- searchmine.net.

Again, this treacherous scheme parasitizes a legitimate search engine to feign trust. To take the hoax further, the crooks have created a network of online resources hinging on the Yahoo Hosted Search (YHS) service. It’s hard to say how exactly the felons have established this controversial “partnership”, but it has reached unsettling heights over the years. A mix of stubborn adware, dirty redistribution of Internet traffic, and questionable ties between malicious and regular entities makes this wave a major spot on the heat map of contemporary Mac menaces.
Other hijackers plaguing Safari
Whereas the vast majority of the Safari Mac Virus embodiments forward one’s web traffic to Yahoo or Bing, some stand out from the crowd. There are strains that promote various worthless applications or outright dangerous ones. A common trick is to drag a victim into a vicious circle of rerouting to sites that push fake updates of popular software such as Adobe Flash Player. In many scenarios, the landing page recommends the user to install an app which is supposedly required to watch streaming content. Obviously, these entities are malware in disguise that can range from browser hijackers and info-stealers to Mac ransomware and scareware.
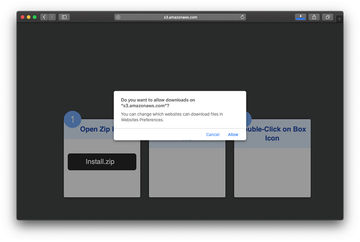
Another notorious ruse involves non-stop redirects to a YouTube copycat. The malicious page tells the visitor to click on the embedded “Allow” button to watch some allegedly viral video. This way, the malefactors cloak the process of enabling web push notifications in Safari. Once turned on, this feature will result in obnoxious pop-up ads deluging the right-hand part of the desktop.
No matter which abominable incarnation of the Safari Virus Redirect you may encounter on your Mac, it will make your computing experience go down the drain. If this is already happening due to a slip-up such as the installation of a dubious app bundle, the following instructions will help purge the infection. Be advised that most of these pests are cross-browser and so you may need to additionally tidy up Chrome and Firefox if these are installed on your Mac.
Safari Redirect Virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
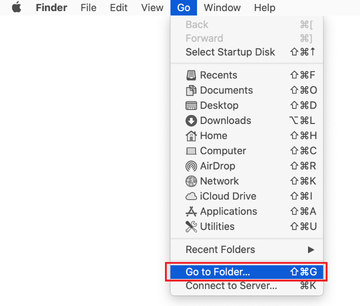
Expand the Go menu in your Mac’s Finder bar and select Utilities as shown below.
Locate the Activity Monitor icon on the Utilities screen and double-click on it.
In the Activity Monitor app, look for a process that appears suspicious. To narrow down your search, focus on unfamiliar resource-intensive entries on the list. Keep in mind that its name isn’t necessarily related to the way the threat is manifesting itself, so you’ll need to trust your own judgement. If you pinpoint the culprit, select it and click on the Stop icon in the upper left-hand corner of the screen.
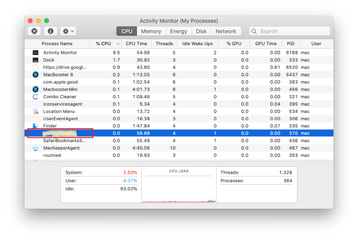
When a follow-up dialog pops up asking if you are sure you want to quit the troublemaking process, select the Force Quit option.
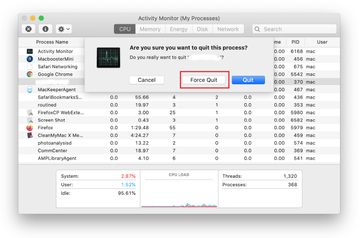
Click on the Go menu icon in the Finder again and select Go to Folder. You can as well use the Command-Shift-G keyboard shortcut.
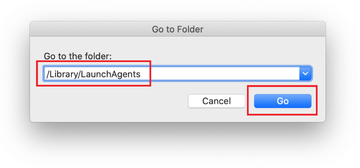
Type /Library/LaunchAgents in the folder search dialog and click on the Go button.
Examine the contents of the LaunchAgents folder for dubious-looking items. Be advised that the names of files spawned by malware may give no clear clues that they are malicious, so you should look for recently added entities that appear to deviate from the norm.
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist. If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
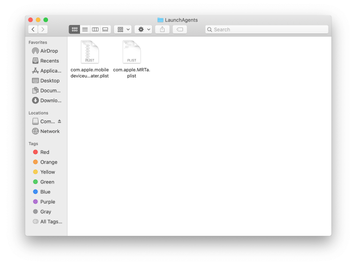
Use the Go to Folder lookup feature again to navigate to the folder named ~/Library/Application Support (note the tilde symbol prepended to the path).
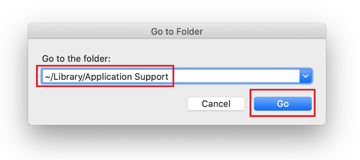
When the Application Support directory is opened, identify recently generated suspicious folders in it and send them to the Trash. A quick tip is to look for items whose names have nothing to do with Apple products or apps you knowingly installed. A few examples of known-malicious folder names are Quick Mac Booster, IdeaShared, and ProgressMatch.
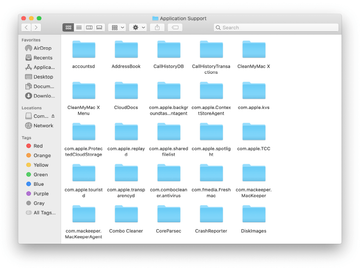
Enter ~/Library/LaunchAgents string (don’t forget to include the tilde character) in the Go to Folder search area.
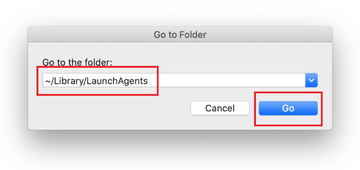
The system will display LaunchAgents residing in the current user’s Home directory. Look for dodgy items related to Safari Redirect Virus (see logic highlighted in subsections above) and drag the suspects to the Trash.
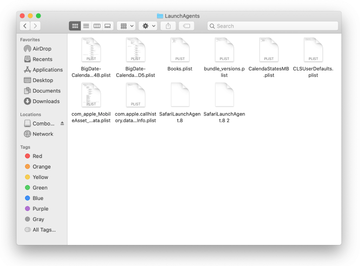
Type /Library/LaunchDaemons in the Go to Folder search field.
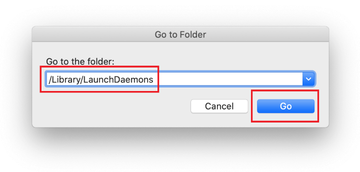
In the LaunchDaemons path, try to pinpoint the files the malware is using for persistence. Several examples of such items cropped by Mac infections are com.pplauncher.plist, com.startup.plist, and com.ExpertModuleSearchDaemon.plist. Delete the sketchy files immediately.
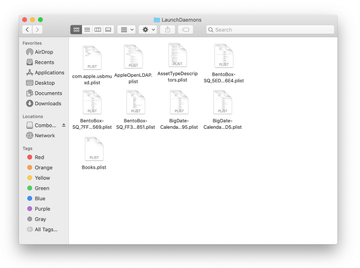
Click on the Go menu icon in your Mac’s Finder and select Applications on the list.
Find the entry for an app that clearly doesn’t belong there and move it to the Trash. If this action requires your admin password for confirmation, go ahead and enter it.

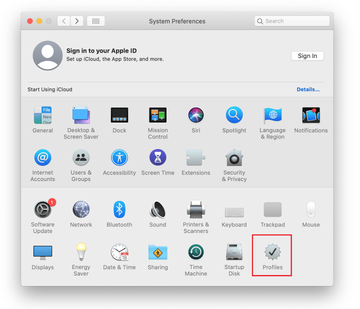
Expand the Apple menu and select System Preferences.
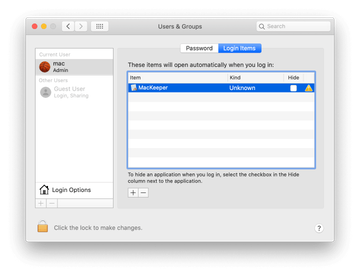
Proceed to Users & Groups and click on the Login Items tab.
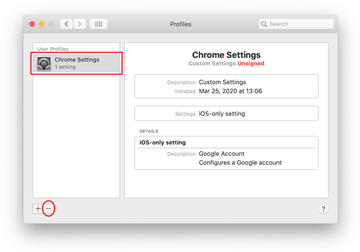
Now select Profiles under System Preferences. Look for a malicious item in the left-hand sidebar. Several examples of configuration profiles created by Mac adware include TechSignalSearch, MainSearchPlatform, AdminPrefs, and Chrome Settings. Select the offending entity and click on the minus sign at the bottom to eliminate it.
Get rid of redirect virus in Safari and other browsers on Mac
To begin with, the web browser settings taken over by Safari Redirect Virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Remove redirect virus in Safari
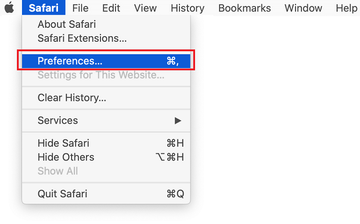
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
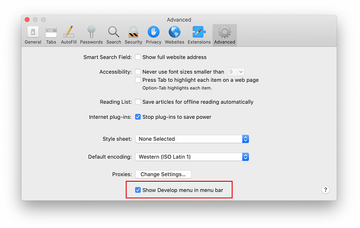
- Once the Preferences screen appears, click on the Advanced tab and enable the option saying “Show Develop menu in menu bar”.
- Now that the Develop entry has been added to the Safari menu, expand it and click on Empty Caches.
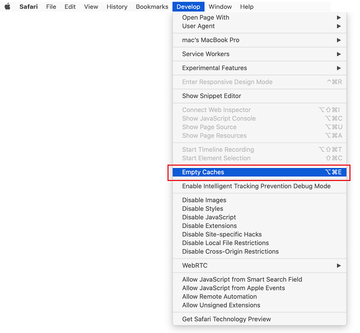
- Now select History in the Safari menu and click on Clear History in the drop-down list.
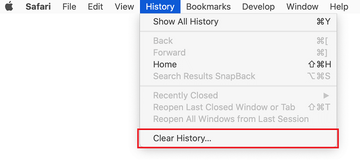
- Safari will display a dialog asking you to specify the period of time this action will apply to. Select all history to ensure a maximum effect. Click on the Clear History button to confirm and exit.
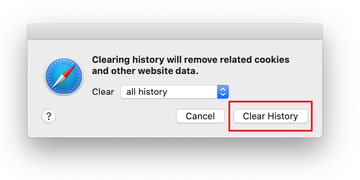
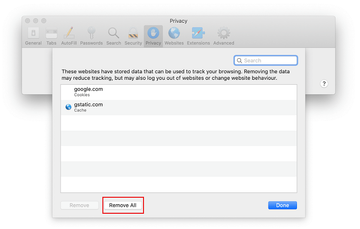
- Go back to the Safari Preferences and hit the Privacy tab at the top. Find the option that says Manage Website Data and click on it.
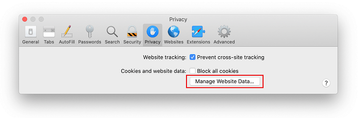
- The browser will display a follow-up screen listing the websites that have stored data about your Internet activities. This dialog additionally includes a brief description of what the removal does: you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click on the Remove All button.
- Restart Safari
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Get rid of redirect virus in Google Chrome
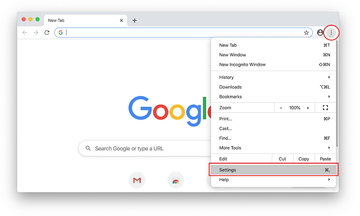
- Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
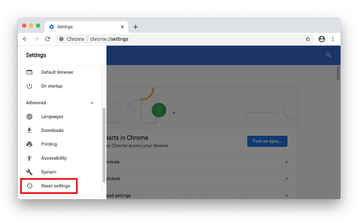
- Scroll down to the Reset settings section.
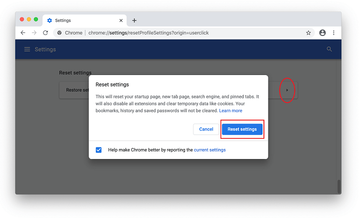
- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- Remove redirect virus from Mozilla Firefox
- Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
- When on the Troubleshooting Information screen, click on the Refresh Firefox button.
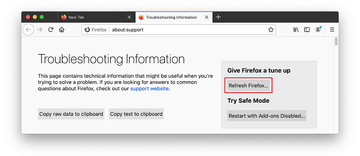
- Confirm the intended changes and restart Firefox.
- Open Firefox and go to Help – Troubleshooting Information (or type about:support in the URL bar and press Enter).
Get rid of Mac Safari Virus using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Safari Redirect virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Safari Redirect issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
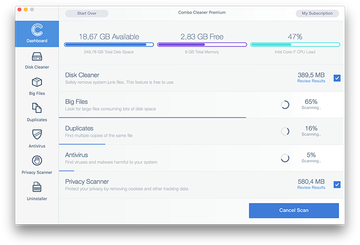
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Safari Redirect threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
FAQ
How do I stop Safari from redirecting on Mac?
If Safari is being incessantly rerouted to unwanted sites, figuring out the root cause of this predicament is trivial: a species of harmful code has stung the Mac. Even though a lot of Apple aficionados still firmly believe these computers don’t get viruses, the Safari redirect threat is real and so are tons of rogue optimizers, malicious crypto miners, and even ransomware perils out there.
To make Safari redirect activity discontinue, the fixes span both system-wide cleaning and quite a bit of tidying at the browser level. First things first, to overcome the persistence of this infection you need to pinpoint and iron out the macOS configuration profile it uses. Head to System Preferences and check if an entry named “Profiles” is listed there. In case there are no profiles at all, this item will be missing. Otherwise, open it and delete the unwelcome object.
The rest of the remediation includes:
- Quitting any suspicious processes you come across in the Activity Monitor.
- Spotting and removing dubious LaunchAgents, LaunchDaemons, and items in the Application Support folder that look out of place.
- Trashing recently installed apps that appeared on your Mac without your awareness.
- Vanquishing unwanted login items.
- Emptying the Trash.
When done, you should take care of the redirect proper: remove dodgy extensions from Safari, empty caches, and delete all browsing history. This combo of techniques will address the issue in most cases. The only roadblock on your way toward successful removal of the parasite is that its filenames and processes vary and usually have nothing in common with its manifestation. If you cannot accurately identify its components, consider using an automatic cleaning tool to boost your effort.
How do I remove browser hijacker from Safari?
As emphasized in the previous answer, this isn’t a Safari-only problem. Therefore, before getting down to the browser part of the repair, focus on the removal of adware that impacts the system far beyond wrecking the web surfing experience.
So, it’s recommended to scour the Activity Monitor, Profiles, Login Items, Applications, LaunchAgents, LaunchDaemons, and Application Support directory for items you don’t recognize. Because Mac browser hijackers tend to use random filenames, this is a shot in the dark to a big extent. It’s worth a try, though.
As soon as you have spotted and removed the core adware, open Safari and scrutinize the list of installed extensions. Anything that doesn’t look benign or familiar should be eradicated without a second thought. Do some testing browsing when done: if the issue is still there, you will need to clear Safari’s caches and delete all history. This will wipe all customizations and therefore cause some inconveniences, but you may have to give it a go if nothing else works.
Can Macs get viruses from Safari?
Yes, they can. In fact, this is exactly what’s happening on a large scale these days. Safari is fairly handy and secure, but it has flaws that allow threat actors to bypass the defenses and deposit PUAs onto systems. With that said, it’s worth placing emphasis on the user’s role in this process. There are hardly any Mac viruses currently at large that exploit Safari in a zero-click way. Instead, these pests infiltrate systems after the users unwittingly allow them to.
The classic plot involves a bundle of several applications downloaded via Safari. The front app in this package is harmless or even useful but the extras can be malicious, let alone the fact that the user may not even know that something else is tailgating into the Mac. If this infection chain is going on via Safari, the browser won’t alert the user unless the source download page is blacklisted. This isn’t really a Safari loophole, after all. These attacks stem from a lack of vigilance on the user’s end.
