Explore the issue where Mac malware mishandles the com.apple.tcc directory to play a privileges escalation trick and thereby take root in the host system.
As a foreword, it’s worth pointing something out: ideally, a Mac user should never really be concerned about the entity called com.apple.tcc; moreover, most people have no idea what it is and what its purpose is. This is understandable, given that this is the name of a folder located within /Library/Application Support path that retains, among other things, an object named TCC.db, which is an SQLite database underlying a number of important system-wide preferences. Specifically, it defines Security & Privacy as well as Accessibility settings on a Mac computer.
An additional wiki facet of the matter is as follows: first introduced with the OS X 10.9 Mavericks release in 2013, TCC stands for Transparency, Consent, and Control. Having evolved all the way to the current macOS 10.15 Catalina, it is Apple’s longstanding implementation of a mechanism for users to grant and restrict permissions to their private data. Originally tasked with managing the scope of third-party applications’ access to sensitive information, this service can also be an instrument for cybercriminals to piggyback on while achieving their malicious objectives.
There are a few strong reasons why com.apple.tcc is a Pandora’s Box malefactors may want to break open. Potentially unwanted applications such as adware and fake system cleaners can cause the most damage if they gain a foothold in a system far beyond regular software activity. For instance, ads fraudulently injected into web pages pull the right strings as long as they are targeted. To be able to display ecommerce information aligned with the victim’s interests and previous Internet searches, the infection has to collect these details behind the scenes – and it will fail to do it without the appropriate privileges. By furtively misconfiguring the contents of TCC.db file inside com.apple.tcc folder, the harmful program can get these elevated permissions in a snap. This attack vector is also a way to bypass System Integrity Protection (SIP), a macOS security feature designed to safeguard system-critical files and paths against unauthorized tweaks.
Adware modifying com.apple.tcc data may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.A virus called macOS Bundlore is one of the notorious threats relying on this exact technique. Propagating by means of shady downloads and spoof Flash Player updates, it silently infiltrates a Mac computer and establishes persistence by circumventing SIP defenses and altering TCC.db database. These shady changes allow the culprit to interfere with browser behavior and download additional malware onto the plagued host. Speaking of the latter impact, the Bundlore nasty connects to a Command and Control (C2) server and downloads an ad-sprinkling app such as MyCouponsmart or MyShopcoupon. When the secondary payload is executed, it goes a well-trodden route of spammy ad delivery. To this end, it harnesses the permissions obtained by Bundlore to embed offensive JavaScript code in Safari, Chrome, or Firefox.
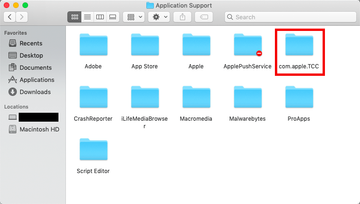
Normally, the com.apple.tcc folder pictogram has a “do not enter” sign in its right-hand bottom corner. It means it’s not accessible by the user, which is a measure to thwart unintended modifications that may cause unpredictable malfunctions and distort the current set of application privileges. However, modern backdoors and Mac viruses such as the above-mentioned Bundlore can get around this access restriction logic. Therefore, if you go to /Library/Application Support and see that the com.apple.tcc folder has no red sign icon, this may be a breadcrumb leading to malware foul play. If this is the case, be sure to apply a security procedure that will help identify the infection and get rid of it.
Uninstall Mac malware escalating its privileges via com.apple.tcc tweaks
The steps listed below will walk you through the removal of the malicious application. Be sure to follow the instructions in the order specified.
- Open up the Utilities folder as shown below
- Locate the Activity Monitor icon on the screen and double-click on it
- Under Activity Monitor, find a process named MyCouponsmart, MyShopcoupon or other suspicious-looking process, select it and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
- Click the Go button again, but this time select Applications on the list. Find the adware on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it
- Now go to Apple Menu and pick the System Preferences option
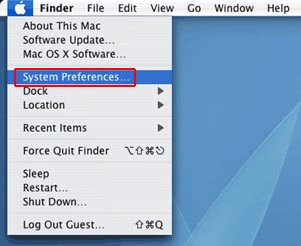
- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the computer is started up. Locate MyCouponsmart, MyShopcoupon or other potentially unwanted object there and click on the “-“ button
Get rid of unwanted ads and redirects in web browser on Mac
To begin with, settings for the web browser that got hit by this virus should be restored to their default values. The overview of steps for this procedure is as follows:
- Reset Safari
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
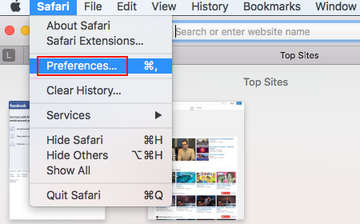
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Remove All Website Data and click on it
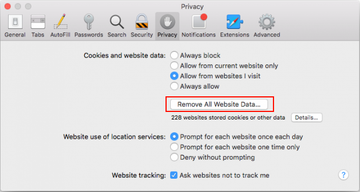
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove Now button
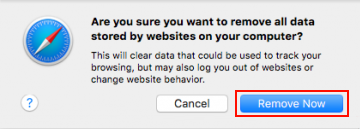
- In order to selectively clear data generated by certain websites only, not all of them, hit the Details button under the Privacy section of Safari Preferences

- This feature will list all websites that have stored potentially sensitive data, including cache and cookies. Select the one, or ones, that might be causing trouble and click the appropriate button at the bottom (Remove or Remove All). Click the Done button to exit.
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Reset Google Chrome
- Open Chrome, click the More (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, selectAdvanced
- Scroll down to the Reset settings section. Under the Restore settings to their original defaults option, click the Reset settings button
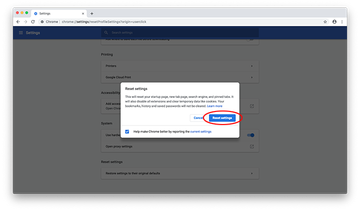
- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Reset Mozilla Firefox
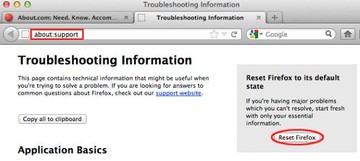
- Open Firefox and select Help – Troubleshooting Information
- On the page that opened, click the Reset Firefox button
Get rid of com.apple.tcc abusing virus using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Adware modifying com.apple.tcc data virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Adware modifying com.apple.tcc data issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
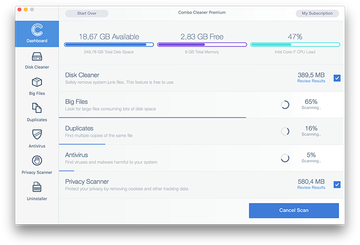
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
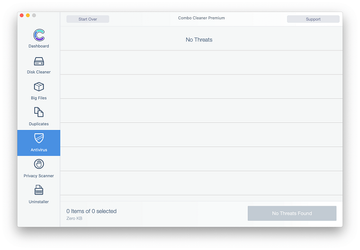
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Adware modifying com.apple.tcc data threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
