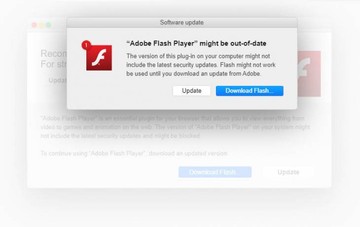
Keep abreast of the growingly treacherous Shlayer Trojan Mac campaign to find out how to avoid this threat and remove it if the attack has taken place.
Shlayer Trojan isn’t a new peril in the cybercrime landscape. Having been originally spotted in February 2018, this infection homes in on Macs while ostensibly not boasting any particularly sophisticated characteristics. As a matter of fact, this is a researchers-coined name and the culprit doesn’t manifest itself that way. Instead, its primary goals are to display ads, redistribute web traffic, and install other malware onto hosts as a second-stage payload. The Mac menaces backed by this surreptitious promotion – adware, for the most part – had been mainly eclipsing the core threat until early 2020, when a well-known security software provider spread the word about some startling statistics. According to the telemetry systems of the company in question (Kaspersky Lab), a knockoff catalogued as Trojan-Downloader.OSX.Shlayer.a accounted for almost 30% of all their detections globally on machines running macOS last year. This whopping number makes the predatory program the dominating strain in its niche that outstrips the second most detected Mac malware codenamed Bnodlero.q by nearly 17%. How did the pest under scrutiny become so alarmingly pervasive?
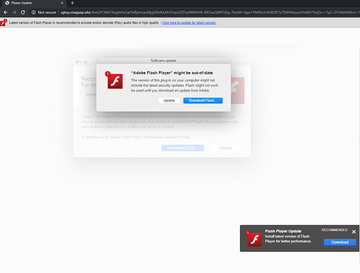
Before taking a deep dive into the distribution of Shlayer Trojan, though, let’s dissect its modus operandi and objectives. The infection arrives at Macs with a booby-trapped version of Adobe Flash Player. Unsuspecting users are fooled into clicking a malicious link that supposedly installs the latest iteration of the software suite. In fact, the victims thereby authorize the infiltration of the pest. Shlayer additionally adds a rogue extension to Safari that modifies the plagued user’s browsing preferences and executes covert reconnaissance seeking to collect the search terms and web surfing history. None of this activity is accompanied by dialogs or other forms of permission requests. One more element of the raid is that the Trojan promotes a custom build of open-source proxy software while installing a valid digital certificate. This trick paves the threat’s way towards displaying ads and injecting arbitrary scripts on the visited websites. Plus, the browser may be redirected to fake search engines, dangerous download portals, or tech support scams.
Shlayer Trojan may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.As previously mentioned, an extra trait of the Shlayer Trojan comes down to pushing opportunistic viruses. To be able to do it silently, the malady cashes in on its capability of communicating with a Command and Control server. For the record, security analysts have unearthed roughly 140 different C2 domains associated with this campaign over the course of its two-year existence. This real-time server interaction quirk yields a game-changing benefit to the operators of this malicious entity. Simply put, the crooks can remotely instruct Shlayer to install any other malware onto compromised Mac computers. This trespass typically assumes the form of a commonplace setup routine. The victim suddenly sees a popup screen asking them to install some multimedia app or web search enhancement tool, which is actually a harmful app in disguise. The worst part is that the baddie will get on board no matter if the user agrees or rejects the “offer”.
The criminals behind Shlayer have masterminded a distribution wave that stands out from the crowd. There are hundreds of websites out there that promote it at this point, and some of these have large audiences among Mac fans. The malefactors have reportedly set up “partner programs” that offer webmasters, YouTubers, and Wikipedia contributors to spread fake Adobe Flash Player updates for an attractive commission that may reach $4 per install. Obviously, even with such a high rate, the hoax still pays off as the perpetrators can monetize the attack in multiple ways. They rake in a mind-boggling profit by displaying sponsored information to countless victims, funneling the intercepted traffic to malicious web pages, and selling the stealthily harvested browsing data to interested parties such as advertisers or other cybercriminals. If you notice any of the above clues that may indicate the presence of the Shlayer Trojan on your Mac, be sure to get rid of it along with a potential bundle without delay.
Shlayer malware manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
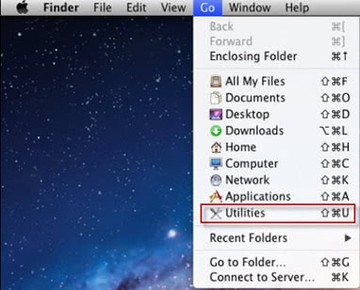
- Open up the Utilities folder as shown below
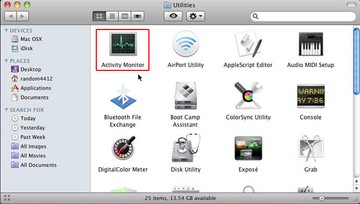
- Locate the Activity Monitor icon on the screen and double-click on it
- Under Activity Monitor, find an entry that appears suspicious, select it and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
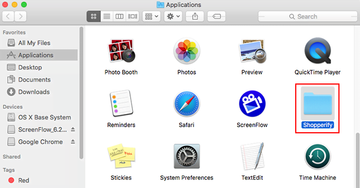
- Click the Go button again, but this time select Applications on the list. Find the dubious entry on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it
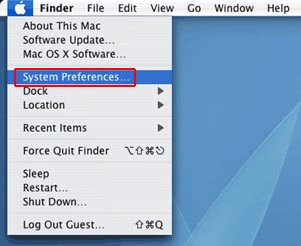
- Now go to Apple Menu and pick the System Preferences option
- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the computer is started up. Locate the potentially unwanted object there and click on the “-” button
Get rid of Shlayer malware ads and redirects in web browser on Mac
To begin with, settings for the web browser that got hit by this virus should be restored to their default values. The overview of the steps for this procedure is as follows:
How do I get rid of Shlayer malware symptoms in Safari?
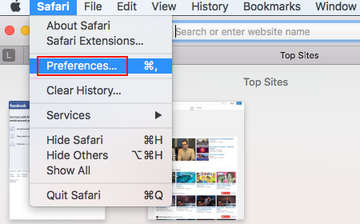
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
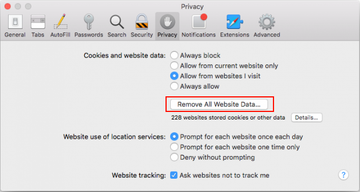
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Remove All Website Data and click on it
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove Now button
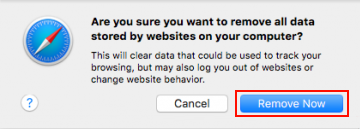
- In order to selectively clear data generated by certain websites only, not all of them, hit the Details button under the Privacy section of Safari Preferences

- This feature will list all websites that have stored potentially sensitive data, including cache and cookies. Select the one, or ones, that might be causing trouble and click the appropriate button at the bottom (Remove or Remove All). Click the Done button to exit.
How do I block Trojan:OSX/Shlayer in Chrome?
- Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
- Scroll down to the Reset settings section. Under the Restore settings to their original defaults option, click the Reset settings button
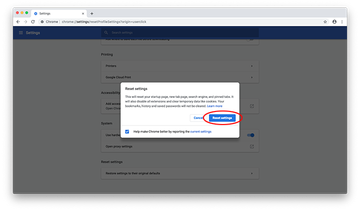
- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
How to stop Shlayer Trojan activity in Mozilla Firefox?
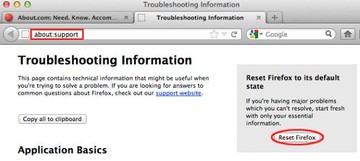
- Open Firefox and select Help – Troubleshooting Information
- On the page that opened, click the Reset Firefox button
Get rid of Shlayer.Trojan using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Shlayer Trojan virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Shlayer Trojan issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
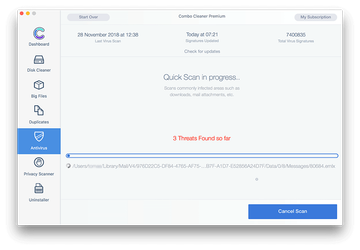
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
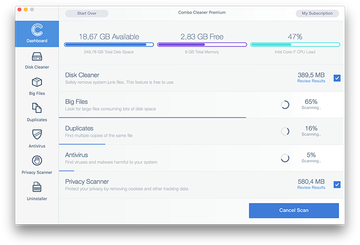
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
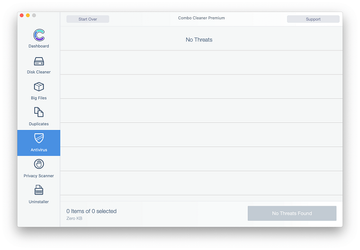
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Shlayer Trojan threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.