Sung-ting Tsai and Ming-chieh Pan, researchers from Taiwan-based Team T5, take the floor at Black Hat Asia to demonstrate how tricky a Mac OS X rootkit can be.
Sung-ting Tsai: Hello everyone! I’m TT.
Ming-chieh Pan: I’m Nanika.
Sung-ting Tsai: We are from Taiwan. We are from Team T5 Research. The topic of this talk is “You Can’t See Me: A Mac OS X Rootkit Uses the Tricks You Haven’t Known Yet”. Since more and more people start using Mac, attacking Mac OS has become a trend and we see more and more malware with advanced techniques. In order to gain persistent control and avoid detection, malware has started to adopt rootkit tricks. In this talk we are going to introduce several new rootkit tricks that cannot be detected by existing security software

This is a short introduction of me (see image below). My name is Sung-ting, and you can just call me TT. I’m the leader of Team T5 Research. We like threat and vulnerability research.
Nanika is our Chief Researcher (see image below). He is a well-known vulnerability researcher and has been disclosing new vulnerabilities for many years. His major areas of expertise include vulnerability research, exploit techniques, malware detection, mobile security; and he has discovered numerous samples in Windows system as well as document and application vulnerabilities. He has found many 0days and reported those to Microsoft before. In the recent years, we have started exploring and discovering problems on Mac OS. Nanika and me frequently do presentations in many security conferences.
These (see image below) are the topics we are going to discuss today. We will show you some advanced process hiding techniques; how to become a privileged normal user; how to directly access kernel memory from user space. On Mac OS X 10.9, there are security warnings if you want to load third-party kernel module. We will show you how to load a malicious kernel module without warnings. And finally, I will show you a trick to gain root permission.
Advanced Process Hiding
So, the first topic is Advanced Process Hiding. Let me introduce the Rubilyn rootkit. It was released for disclosure in 2012.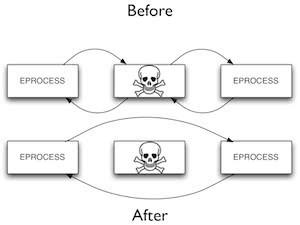
There are many features, but we are going to focus on process hiding. This is how Rubilyn hides a process (see right-hand image). It directly modifies kernel objects to unlink a process from the linked list. So it is a typical DKOM approach to hide a process.
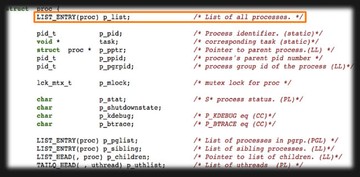
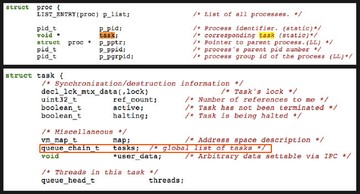
This (see image above) is the process structure in Mac OS kernel. The ‘p_list’ is the linked list. It is the list of all processes. So the first element is a list of all processes. You probably noticed the ‘task’ pointer, which is the third element. It will point to another ‘task’ object. So, one process object will have the task object. Actually, all tasks are in another linked list. As you can see, there is a chain, the ‘queue_chain_t’ – that is the linked list of all tasks (see image below). So there is another linked list.
Read next part: A Mac OS X Rootkit Uses the Tricks You Haven’t Known Yet 2 - Detecting a Process Hidden by Rubilyn
