Read previous part: Injecting Malware into iOS Devices via Malicious Chargers 3 - Installing an Arbitrary Hidden App
Yeongjin Jang and Billy Lau now provide a demo of how the actual Mactans charger can be used to pull off an attack on an iOS device.

We have prepared a video clip for showing all steps of the Mactans attack, so let’s watch it.
This is the Mactans charger; it is built with the BeagleBoard. We made some fancy case with a 3D printer. It has a power cable and SD card for the operating system and some data, and there’s a lightning cable which will be connected to iPhone device. And then, there’s the iPhone device, and we reset this device to the factory state and just set the passcode. So, there are no installed applications. Let’s look at the device information: the version of the operating system is 6.1.4, so it is not a jailbroken device; and there are no pre-installed provisioning profiles, so it is pristine state.
To simulate the scenario, we will install the Facebook application from the App Store, and it is the original Facebook application. The app gets installed and executed. The user can log in and use Facebook. There’s no Trojan at this time. The user will see that the battery is low and he will decide to charge with Mactans, which is a bad choice. Now, we connect with the USB cable, and we can see it is charging. At this time, the pairing cannot happen because the iPhone is passcode-locked. But if the user gets some SMS message or if the user wants to do web surfing while it’s charging, they will unlock the phone. The Mactans attack can start at this point.
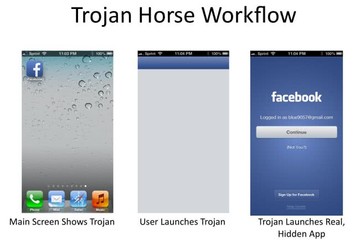
Since the paired connection can be permanently available whether or not the device is locked, the Mactans attack can continue even though the device is locked. While Mactans is installing the provisioning profile and the application, there’s no visual indication of the installing; so it looks just like regular charging. This generally takes less than 1 minute, but in this case the Facebook app is quite large - installation takes 40-50 seconds, and the installation of the payload takes 5-10 seconds – the whole step takes around 80 seconds. So we will unlock the target iPhone after 80 seconds have passed.
Okay, it’s done. Let’s now unplug it and unlock the phone. There’s no visual difference although the attack has happened, because the payload is actually the same as the Facebook application. So, first it launches the Trojan and it launches the Facebook app. And since the original Facebook application is hidden, on the Task Manager only one Facebook application is shown, and it is actually a Trojan. The original Facebook application is not on the SpringBoard and it’s not on the Task Manager either. We set the payload to do something after the user locks the screen, and let’s see what will happen. It types the passcode on its own and even makes a call to the phone right next to it, typing the phone number. Actually, the phone rings! Well, this is the Mactans attack.
I will now pass the mic to Billy and he will talk about the attack scenarios.
Billy Lau: So, ladies and gentlemen, now that you’ve seen how the Mactans attack can take place in real life, let’s discuss some attack scenarios.

In the second scenario, it’s more of a targeted attack, where I want to put it into perspective scenarios like espionage, where the adversary is very highly funded, possibly at a state level. So, there’s no question of the ability to be able to fabricate the charger that looks exactly the same and feels exactly the same as a regular one, but it’s actually a Mactans charger capable of injecting arbitrary malicious apps, as you’ve seen just now. From the adversary’s standpoint, they just need to exchange the original charger with the Mactans charger - and then the game is over.
For further discussion, I will now pass it over to Chengyu.
Read next part: Injecting Malware into iOS Devices via Malicious Chargers 5 - Problems and Fixes
