If the app called Binarymove suddenly appears on a Mac, it’s in the user’s best interest to remove it and thereby stop the browser interference it causes.
Adware tailored to run on macOS is growingly tenacious, sneaky, and annoying. These types of potentially unwanted applications (PUAs) used to be marginal threats but they are making themselves felt acutely these days. Most programs falling into this category follow a well-trodden path of holding sway over a victim’s web browsing activities. To this end, they leverage a peculiar privileges escalation mechanism to manage the default Internet navigation settings in Safari, Chrome, and Firefox. On top of it, the impact may span recurrent instances of injecting ads into web pages (like DDR5 memory 100freesoft) where such sponsored content originally doesn’t belong. This series of adverse effects holds true for the entity known as Binarymove virus. Its onset on a Mac computer is never a matter of an informed decision as the victim discovers an abrupt browser misconfiguration without having authorized any changes prior to their occurrence. From that point on, a significant degree of control over the user’s preferred browser slips through their fingers.
What allows Binarymove Mac virus to play dirty is a new device profile it creates at the initial stage of the attack. It can be found in the Users & Groups pane under System Preferences. Ideally, a configuration profile is a useful administrative tool to specify certain parameters so that the machine operates in a way that fits a certain supervisory paradigm. A common example is about managing preferences in a computer network to enforce enterprise policies. However, Binarymove adware authors have a badly twisted perspective in this regard. They exploit the power of this feature to be in charge of the custom web surfing settings on the contaminated Mac. The profile installed by this malicious app configures the homepage, preferred search engine, and new tab page to return a fraudulent URL every time these defaults are supposed to apply. The resulting page can vary, but in most cases it’s a worthless copycat of a search service, a fake video page instructing the user to install a plugin update, or an outright harmful site hosting scripts that trigger drive-by malware downloads.
Binarymove virus may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes.
Download Now Learn how Combo Cleaner works. If the utility spots malicious code, you will need to buy a license to get rid of it.Binarymove virus also affects the Mac by embedding superfluous advertising materials into most websites the victim visits. This facet of the compromise is backed by a virtual layer that the pest integrates into page layout. When the attack is in full swing, the user will be stumbling upon myriads of in-text links, popups, comparison shopping content, banners, and interstitial windows that splash alongside the current browsing session. Not only do these items diminish the user experience, but they additionally cause the browser and the whole system to slow down because the heaps of adverts are resource-intensive and siphon off too many CPU resources to keep their performance footprint unnoticed.
As far as the distribution of Binarymove virus is concerned, its makers choose not to deviate from the tried-and-tested technique called bundling. The unwanted payload comes in a package of several applications, usually freeware, downloaded outside of the official App Store. The multi-pronged installer is craftily carved to look like it bolsters the setup and basic configuration of a benign program such as a media player, Adobe Flash updater, or some other utility that doesn’t raise any obvious red flags itself. This user-friendliness is a red herring, though, and it hides an extra component in plain sight. In other words, by agreeing to the all-in-one installation terms, the Mac owner implicitly provides their consent to install an accompanying app. This explains why the infiltration of Binarymove into a Mac is a rude awakening for the user. Strictly speaking, the person let the adware in, but this wasn’t really their conscious choice.
Ultimately, the numerous pitfalls associated with this shady application suffice to encourage a security-minded user to stay away from it. If it’s already inside a Mac and messing around with the browser, the necessity of a cleanup is out of the question. It shouldn’t take more than a few minutes but the relief from all the nasty symptoms is definitely worth the effort.
Binarymove virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
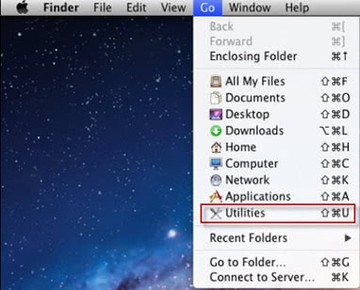
- Open up the Utilities folder as shown below
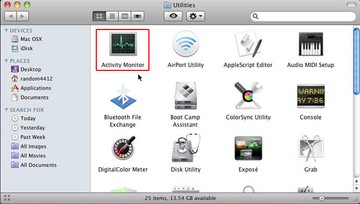
- Locate the Activity Monitor icon on the screen and double-click on it
- Under Activity Monitor, find a process named Binarymove, select it, and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
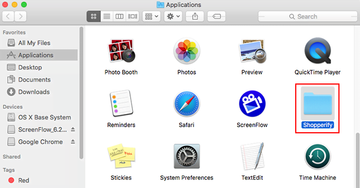
- Click the Go button again, but this time select Applications on the list. Find the Binarymove entry on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it
- Now go to Apple Menu and pick the System Preferences option
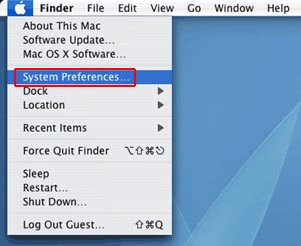
- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the computer is started up. Locate Binarymove or other potentially unwanted object there, select it, there and click on the “-“ button
Get rid of Binarymove redirect activity and ads in web browser on Mac
To begin with, settings for the web browser that got hit by the virus should be restored to their default values. The overview of steps for this procedure is as follows:
- Reset Safari
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
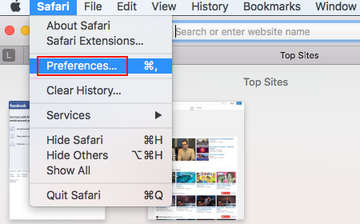
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Remove All Website Data and click on it
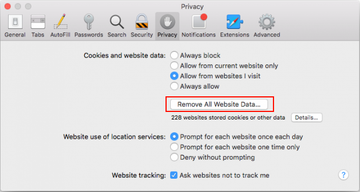
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove Now button
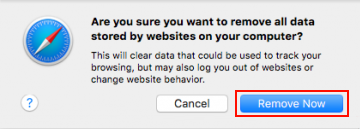
- In order to selectively clear data generated by certain websites only, not all of them, hit the Details button under the Privacy section of Safari Preferences

- This feature will list all websites that have stored potentially sensitive data, including cache and cookies. Select the one, or ones, that might be causing trouble and click the appropriate button at the bottom (Remove or Remove All). Click the Done button to exit.
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Reset Google Chrome
- Open Chrome, click the More (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
- Scroll down to the Reset settings section. Under the Restore settings to their original defaults option, click the Reset settings button
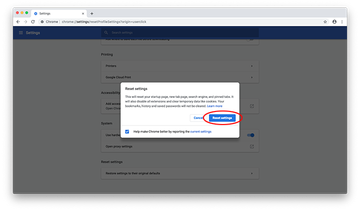
- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Reset Mozilla Firefox
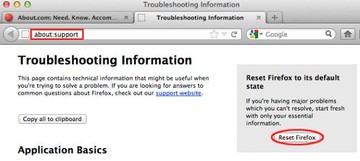
- Open Firefox and select Help – Troubleshooting Information
- On the page that opened, click the Reset Firefox button
Get rid of Binarymove virus using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Binarymove virus virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Binarymove virus issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
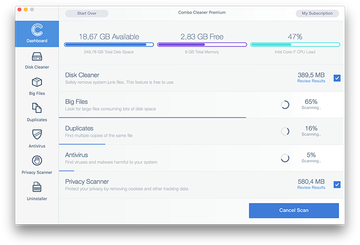
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
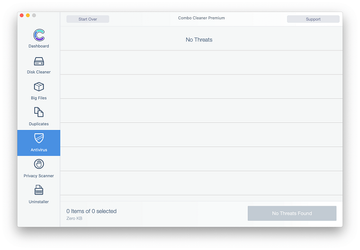
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Binarymove virus threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
