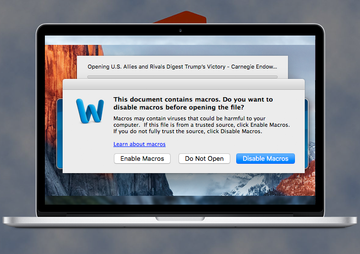
Learn how to get rid of Inquiry.doc Mac malware that attempts to poison a target Mac computer with Trojans, spyware or other harmful code of high severity.
Creating Mac-compatible malware is one of the things cybercriminals focus on these days. It’s somewhat of a challenge for the black hats, too, because macOS is more secure than Windows by design. However, the development job might not be as tough as the distribution at the end of the day. Apple keeps the defenses high enough to prevent perpetrating programs from entering their machines, so the crooks’ tactics have been quite resilient in this regard. An ongoing campaign that involves the Inquiry.doc file demonstrates the evolution of the felons’ modus operandi when it comes to compromising the nearly flawless protection. The file is not really a virus itself, in the broad sense. It is a contagion leveraged to spread other opportunistic cyber threats.
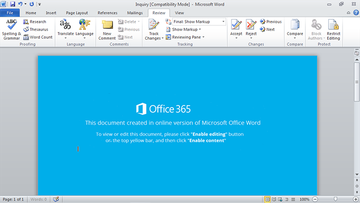
So, let’s see how the attack takes place. First, the malefactors need to somehow make sure users get to the point of opening the toxic Inquiry.doc object. To this end, they typically employ two mechanisms: one is email, the other is bundling. The former is more common. An unsuspecting Mac user discovers a new trustworthy-looking message in the email inbox. It tends to be disguised as a notification from a partner, bank or utility services provider that instructs the recipient to confirm some personal details provided in the attachment. The item embedded in this message is the culprit in question. Inquiry.doc is a Microsoft Word file in compatibility mode that, when opened, doesn’t render anything meaningful. Instead, it is a blank document, or one containing gibberish characters, that encourages the Mac user to click “Enable editing” or “Enable content” button.
Once the would-be victim gets curious enough to click the button and learn what’s actually in that document, a chain of adverse events is triggered in the background. A Word macro script that was inconspicuously fired ends up launching a random-named PKZIP file. This one, it its turn, contains an executable flagged as W32.eHeur, Trojan.Zbot or another threat. The type of delivered malware can range from password stealing Trojans or fake security applications – all the way to Mac ransomware and cryptojacking entities. One way or another, the code promoted in this fashion does not belong on a healthy Mac, so it should be removed immediately. And the tip of the day is to refrain from ever opening suspicious files like Inquiry.doc received over email or bundled with uncertified app downloads.
Inquiry.doc virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
• Open up the Utilities folder as shown below
• Locate the Activity Monitor icon on the screen and double-click on it
• Under Activity Monitor, find a suspicious executable, select it and click Quit Process
• A dialog should pop up, asking if you are sure you would like to quit the process. Select the Force Quit option
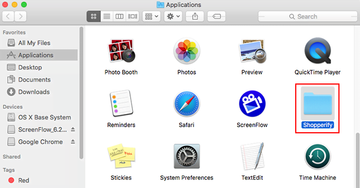
• Click the Go button again, but this time select Applications on the list. Find the potentially unwanted entry on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it
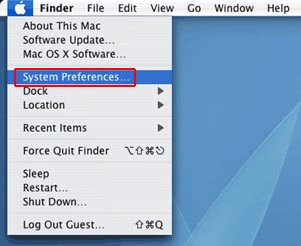
• Now go to Apple Menu and pick the System Preferences option
• Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the box is started up. Locate a suspicious entry that shouldn’t be there and click on the “-“ button
Use automatic tool to uninstall Inquiry.doc related malware from your Mac
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Inquiry.doc virus virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Inquiry.doc virus issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
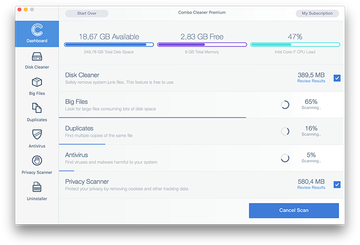
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
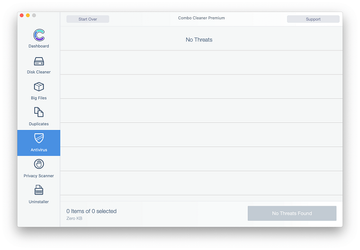
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Inquiry.doc virus threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.