Get a full profile on the Xagent Mac virus, including the infection vectors and its impact, and use cleanup techniques to remove this malware from Mac OS X.
The Xagent Mac malware demonstrates how rapidly cyber espionage is evolving. The original version of this stealth infection targeted devices running Windows, Linux, Android and iOS platforms. It’s not until February 2017 that researchers discovered its Mac edition. The hacker group behind it is believed to be high-profile. According to preliminary verdicts of IT experts who have looked into this issue, Xagent Mac is managed by state-sponsored criminals from Russia. Referred to as APT28 (alias Fancy Bear or Sofacy), the threat actors allegedly have close ties to GRU, Russia’s Main Intelligence Agency. This particular group gained notoriety for compromising the German parliament (Bundestag) and attacking U.S. Democratic National Committee last year.

As it has been mentioned, the top-notch offensive operations of APT28 have recently moved into the Mac OS X realm. Xagent exhibits backdoor properties. It arrives at Mac machines through the use of a sophisticated downloader known as Komplex. When inside, it establishes connection with its Command and Control server to download additional modules behind the scenes. The URLs being reached during this process are camouflaged as domains affiliated with Apple – this is probably an anti-detection trick to circumvent site blacklisting mechanisms. The Xagent components downloaded from the malicious C2furtively identify the target machine’s software and hardware configuration. In particular, the infection harvests information on running processes in order to determine what apps the victim uses and which parts of the system can be exploited as the breach proceeds. That’s only part of the contamination aftermath, though. The backdoor also makes snapshots of the desktop and steals passwords for online-accessible accounts. To add insult to injury, it also finds iPhone backups that are kept on the plagued computer. The entirety of collected data is then exfiltrated to the C&C server.
The blatant information mining operation deployed by Xagent Mac malware is a serious threat to a victim’s identity. Given that the infection is presumably associated with the Kremlin’s intelligence forces, the most likely targets are defense contractors and governments. Data theft, obviously, is a particularly sensitive issue for these organizations. Fortunately, there are Mac security suites capable of detecting and eradicating Xagent. Keep reading this article to learn all the applicable troubleshooting methods.
Xagent manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
• Open up the Utilities folder as shown below
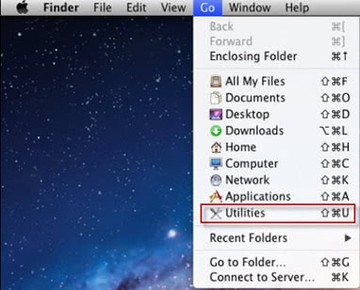
• Locate the Activity Monitor icon on the screen and double-click on it
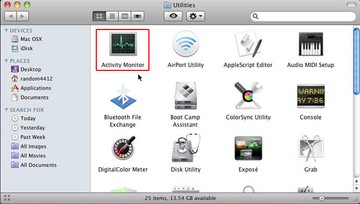
• Under Activity Monitor, find the entry for Xagent (or other dubious-looking object), select it and click Quit Process
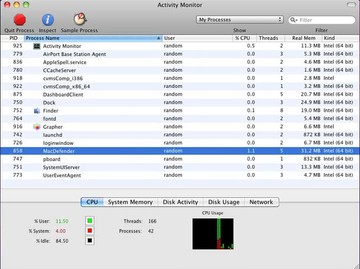
• A dialog should pop up, asking if you are sure you would like to quit the Xagent executable. Select the Force Quit option
• Click the Go button again, but this time select Applications on the list. Find the entry for Xagent on the interface, right-click on it and select Move to Trash. If user password is required, enter it
• Now go to Apple Menu and pick the System Preferences option
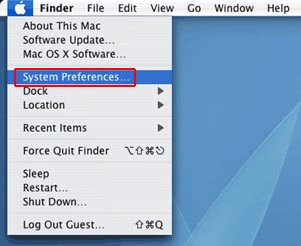
• Select Accounts and click the Login Items button. Mac OS will come up with the list of the items that launch when the box is started up. Locate Xagent or other suspicious entry there and click on the “-“ button
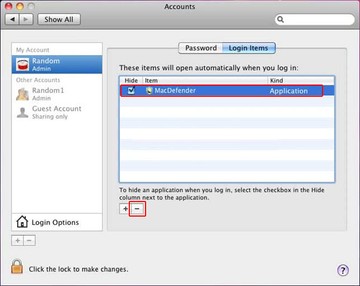
Get rid of Xagent Mac virus using Combo Cleaner automatic removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Xagent Mac malware virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Xagent Mac malware issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
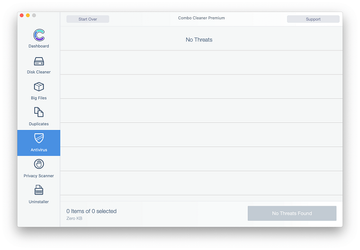
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
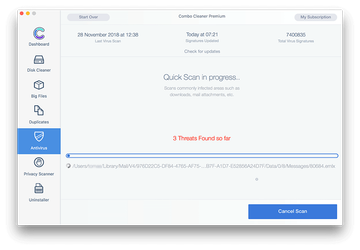
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Xagent Mac malware threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
