Find out everything you need to know about the activity of the Conduit Search toolbar adware on Mac and its up-to-date removal.
Conduit Search is one of the few adware threats at large that have been up and running for a time span as large as a year plus, whereas these types of infections typically aren’t long-lasting. The authors of Conduit have apparently gone yet further, targeting Mac OS machines on a large scale, while Windows based computers were subject to its disruptive effect for a longer period. The early payloads of this PUP (Potentially Unwanted Program) are known to have been distributed as a bundle to DivX products, and for the time being this is no longer the case. The threat now propagates with other third-party applications designed mainly for enhancing multimedia experience and entertainment purposes.
This adware is manifested on a compromised computer as a community toolbar which makes unauthorized changes to the web browsers running on the respective Mac OS system, namely Safari, Chrome or Firefox. Originally, this toolbar was intended for the facilitation of advertising by businesses that could customize it in order to gain a bigger online audience of potential clients. However, this fairly harmless idea turned out a calamity to individual Internet users who got this browser helper object as a drive-by attached to other downloads.
The worst part about the Conduit Community toolbar is that it changes such settings as the homepage, new tab page, and the default search provider in the above-mentioned web browsers. What is more, this is done with no option of entering alternate values for these settings, leaving the user stuck with http://search.conduit.com instead, which, by the way, further reroutes the traffic to Bing.
The fix for the Conduit Community toolbar issue in Mac OS isn’t trivial and requires a number of subsequent actions on the user’s end. It was found that locating and deleting the affiliated files under Library (such as /Library/InputManagers/CTLoader/, /Library/LaunchAgents/com.conduit.loader.agent.plist, /Library/Application Support/SIMBL/Plugins/CT2285220.bundle, /Library/Application Support/Conduit/, ~/Library/Internet Plug-Ins/ConduitNPAPIPlugin.plugin) might be worth a try but doesn’t completely resolve the problem in many cases. This is why, in addition to sending the unwanted files listed above to trash, the affected web browsers running on the targeted Mac should be attended to as well.
Conduit Search manual removal for Mac
To begin with, settings for the web browser that got hit by search.conduit.com adware should be restored to their default values. The overview of steps for this procedure is as follows:
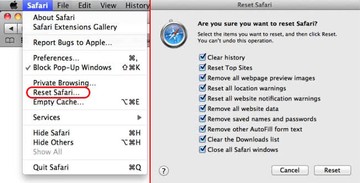
1. Reset Safari
• Open the browser and go to Safari menu. Select Reset Safari in the drop-down list
• Make sure all the boxes are ticked on the interface and hit Reset
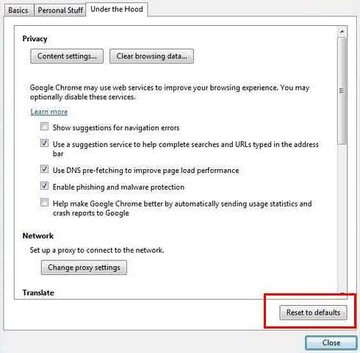
2. Reset Google Chrome (if affected by the Conduit Search virus)
• Open Chrome and click the Customize and Control Google Chrome menu icon
• Select Options for a new window to appear
• Select Under the Hood tab, then click Reset to defaults button
3. Reset Mozilla Firefox (if hit)
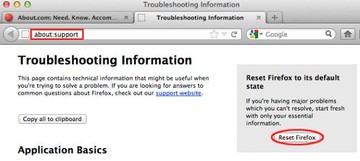
• Open Firefox and select Help – Troubleshooting Information
• On the page that opened, click the Reset Firefox button
Get rid of Conduit Search virus using Combo Cleaner automatic removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Conduit Search virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Conduit Search issue using Combo Cleaner:
Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
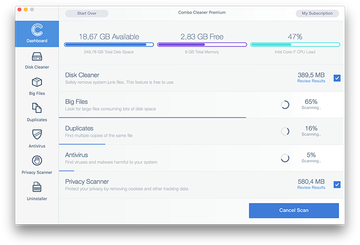
Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.
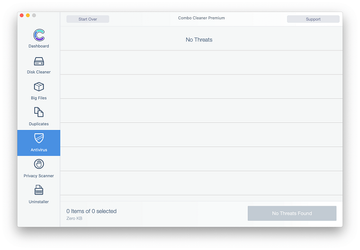
Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).
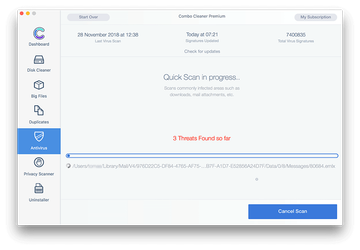
In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Conduit Search threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.
Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.