A recent Chrome update takes care of a high-risk flaw that could have been weaponized by North Korean threat actors in attacks against security researchers.
The vulnerability, documented as CVE-2021-21148 and rated high-risk, can cause a heap buffer overflow condition in Google Chrome for Mac, Windows, and Linux. Specifically, it affects the V8 JavaScript engine engineered by The Chromium Project for all web browsers under its umbrella. If abused, the loophole leads to memory corruption and allows a malicious actor to open a backdoor into the target’s system. While patches like that are normal occurrences in the Chrome ecosystem, the alarming thing about this one is that it has likely been parasitized in real-world attacks. Moreover, security researchers could have been the intended victims.
Breadcrumbs leading to North Korean hackers
The vulnerability was first reported by security analyst Mattias Buelens in late January 2021. At that point, Google admitted it was aware of a viable exploit for this bug that was being harnessed in the wild. Furthermore, the tech giant’s Threat Analysis Group (TAG) shortly published an article describing an attack chain used by a high-profile hacker gang based in North Korea. According to these findings, the government-funded cybercrime crew zeroed in on researchers involved in vulnerability analysis initiatives.
The crooks have been reportedly using social media channels to lure their targets into visiting a malware-riddled blog under the guise of cooperation proposals. When visited from an unpatched version of Chrome (older than v88.0.4324.150), the site would trigger an exploit that quietly executed malicious code in the system and kept a loophole opened for further exploitation. Since some security-minded folks have fallen for this trick, regular users could be much easier prey.
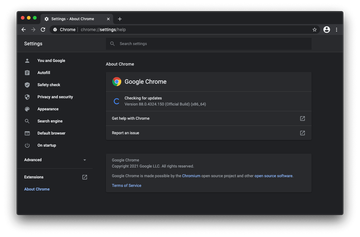
With that said, it’s strongly recommended to head to the browser’s settings, open ‘Help’, select ‘About Google Chrome’, and ascertain that the latest build is already installed. If it’s not, the right time to update is now.