A crew of ethical hackers have probed Apple’s proprietary web infrastructure and spotted a host of flaws, some of them categorized as critical.
The white hats – Sam Curry, Ben Sadeghipour, Brett Buerhaus, Samuel Erb, and Tanner Barnes – teamed up in early July 2020 to check Apple’s electronic infrastructure for weak links. The collaboration turned out fruitful as the five enthusiasts pinpointed 55 vulnerabilities in different areas of Apple’s digital “household” over a three-month period. After submitting their findings to the Cupertino company under its bug bounty program, the researchers have earned $288,500 for 32 flaws and expect to receive more payments for the remaining reports in the upcoming months. Out of the total vulnerability count on this project, 11 flaws are flagged critical, 29 ranked high-severity, 13 moderately impactful, and only two categorized as low-severity.
Types of the unearthed vulnerabilitie
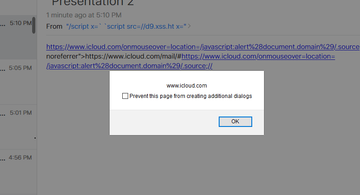
The adverse effects of exploiting these bugs run the gamut from compromising Apple’s industrial inventory solutions and accessing employee applications to obtaining the source code for internal projects and taking over iCloud accounts. Two defects on the long list are potentially the most destructive if exploited by a competent adversary. One of them is a remote code execution (RCE) vulnerability that could pave an evildoer’s way toward gaining unauthorized access to the Apple Distinguished Educator (ADE) program. The other is a stored cross-site scripting (XSS) flaw allowing a malefactor to run a computer worm that steals a user’s iCloud credentials via email without raising red flags.
To Apple’s credit, all of these slip-ups were fixed in mere days. According to the researchers, the span between the disclosure and remediation of the most critical bugs was within four hours. It took Apple up to two business days to rectify the other imperfections.
Peaks and valleys of Apple’s bug bounty program
Apple extended the reach of its bug bounty program in December 2019 by allowing anyone to join up. For years, this had been a prerogative of the chosen, and only researchers who got the tech giant’s official blessing could explore its products for imperfections. Contrary to the anticipations, though, this newsmaking move was followed by a good deal of controversial feedback about the company’s whims of silencing researchers who found bugs in its products. Meanwhile, vulnerabilities could stay unpatched for months.
In the case of the reports by Sam Curry and fellow-analysts, things were quite the opposite. Not only did Apple’s product security personnel take care of the loopholes amazingly fast, but they also gave the white hats the green light to spread the word about the vulnerabilities at their own discretion. Furthermore, the researchers received rewards for the greater part of the bugs without further ado and expect more batches as the flaws are re-tested.
With these developments underway, Apple could be departing from the tactic of turning a blind eye to ethical hackers’ initiatives in regards to exploring its products and services for weaknesses. And yet, some will argue that such reasoning is premature and the big picture has yet to take shape. One way or another, this is definitely a step in the right direction.
