Well-known researcher unveils a new powerful exploit that allows executing malicious Office macros on a Mac computer with zero user interaction.
Macros in Office documents are intended to facilitate the execution of iterative tasks. These are shortcuts to performing routine actions and therefore they are, ideally, both helpful and benign. However, in pursuit of workarounds to plague systems with malicious code, cybercriminals have been mishandling macros for years. This is one of the most widespread malware distribution vectors in the Windows ecosystem. Paired with social engineering tricks, it works by luring a user to enable macros in a file attached to a phishing email. What happens next is, a script gets triggered behind the scenes and downloads a predefined threat onto the host.
Although this stratagem isn’t nearly as common in the Mac world, it has been front and center in several campaigns since 2017. With a recent exploit unearthed by a white hat researcher, though, this marginality might transform into mainstream implementation by malicious actors.
Downsides of commonplace Office macros abuse on Macs
According to Patrick Wardle, former NSA hacker and currently security analyst at Jamf, there is a way to weaponize Office macros on macOS beyond the traditional model to boost the success rate of such an attack. He spread the word about his findings at the Black Hat USA event held remotely this year due to the pandemic.
As part of his presentation called “Office Drama on macOS”, the researcher highlighted the hurdles encountered by cybercrooks when trying to abuse macros on Mac computers in the well-trodden way. Here they are:
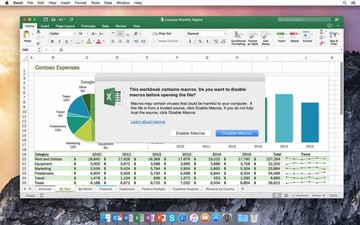
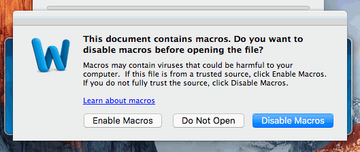
- Whenever a booby-trapped MS Office document is opened, the user sees an alert stating that the file contains macros. To get these potentially harmful entities to run, the would-be victim needs to click on the dialog’s button that says “Enable Macros”. Otherwise, the attack won’t continue.
- As long as the user is running an up-to-date version of macOS, Office applications and their components are executed in a sandbox environment. Therefore, even if the person slips up and enables macros, the rest of the system will stay unaffected.
- The payloads hinging on macros may fail to pass Apple’s notarization and quarantine checks.
These are, obviously, serious roadblocks that stop most attempts to compromise a macOS machine in their tracks.
New attack method bypasses all defenses
Wardle’s exploit chain eliminates the above drawbacks from the equation. Specifically, it allows an adversary to run harmful macros on a Mac without user approval, prevent them from being sandboxed, and circumvent notarization restrictions.
A vulnerability codenamed CVE-2019-1457 is what sets the attack in motion. In a proof-of-concept video, the researcher showed Calculator.app being triggered on a computer running Catalina once an Excel document with a sketchy macro in it was loaded. This took place without any sign of manually granting a permission to allow macros.
The attack scenario can get evil depending on the payload, though. It can theoretically allow a perpetrator to create a backdoor providing a hacker with full access to the Mac. This way, installing more malware or controlling the system’s behavior is trivial.
At the time of writing, the Office flaw has been addressed by Microsoft. Apple, in turn, has rolled out a fix on their side. Hopefully, sophisticated macOS macro-borne malware like that won’t go further than the PoC domain anytime soon.