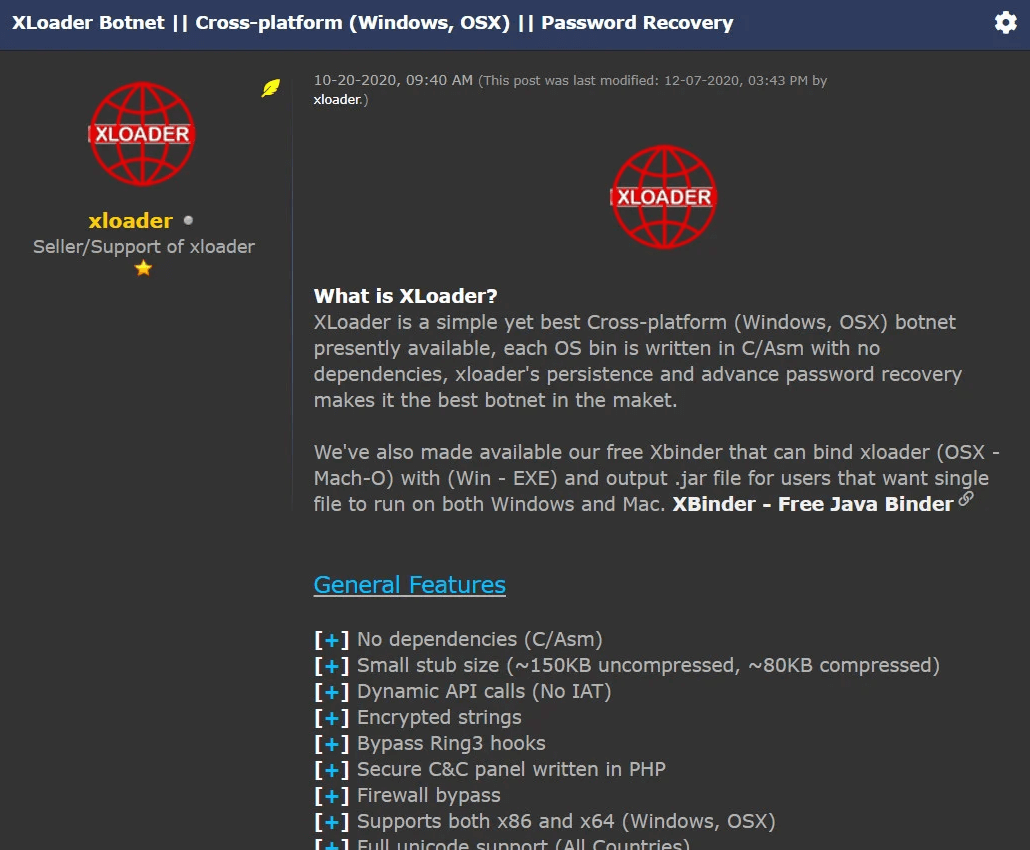
A sneaky malware strain called XLoader is being actively promoted on hacking forums as a cross-platform data stealer with advanced capabilities.
Those who aren’t new to cybersecurity might be aware of a long-standing threat dubbed FormBook. Seen in more than a thousand cybercrime campaigns over the past several years, it is widespread Windows-only malware that steals sensitive information and allows its masters to control its behavior via commands from a remote server. In February 2021, researchers came across a FormBook spin-off called XLoader, which has since gained significant momentum on the dark web. One of the key reasons for its growing popularity among black hats is that it has extended its grip to macOS, a platform on the receiving end of numerous exploration vectors these days.
A dynamically escalating peril with unique features
XLoader follows in the footsteps of its prototype by being able to retrieve the victims’ sign-in credentials, quietly take screenshots, record keystrokes, and run arbitrary executable files on hosts. It steals passwords from the leading web browsers, including Mozilla Firefox, Google Chrome, Opera, Edge, and Internet Explorer, as well as several mainstream email clients such as Microsoft Outlook, Foxmail, and Thunderbird. XLoader authors advertise it as a lightweight botnet infection that has no code assembly dependencies, makes dynamic API calls, and circumvents the common protection barriers such as firewalls and Ring3 hooks to fly under the radar.
As mentioned previously, this sample’s game-changing advantage over its predecessor is that it can run on both PCs and Mac computers. Furthermore, it supports x86 and x64 operating system architecture to maximize the attack surface. One more feature playing into attackers’ hands is the ability to generate a single Java Archive (JAR) file that combines EXE and Mach-O executables so that the info-stealer can be deployed inside Windows and macOS environments seamlessly.
XLoader is available on a software-as-a-service basis. It means that interested parties can rent it for a fee, which currently amounts to $49 per month for the macOS version and $59 per month for the Windows build. The criminals in charge maintain a centralized C2 infrastructure to hold sway over the uses of their code.
How can Mac users stay safe?
According to analysts’ insights into the XLoader campaign, it left its footprint in 69 countries from December 2020 to June 2021, with the majority of infections recorded in the United States. Since the distribution rate is that high, the defenses come to the fore. The deeply obfuscated components of this malware are problematic for the average Mac user to spot, not to mention that it runs without raising any conspicuous red flags.
One of the few ways to identify an ongoing attack is to scrutinize the contents of the ~/Library/LaunchAgents folder. Dodgy files dropped by XLoader will typically have random-looking names. If found, these items should be trashed immediately. An extra layer of protection is to use a trusted anti-malware tool that adds heuristics and signature analysis to the detection logic.
