Computer security expert and researcher Remy Baumgarten presents a tool for Mac malware analysis called Mach-O Viz at Decon 21 event.

Good afternoon everybody! I’m Remy Baumgarten, I work at ANRC Services; and today I’m going to present a tool I’ve been working on for a little while now, and I hope you enjoy it.
A little bit about me. Again, I work for ANRC Services; I mostly do mobile malware talks. Here’s a few of the conferences I’ve done my talks at (see image below). Presently, I am doing R&D at ANRC, mostly with iOS/Android. I also do security instruction for the Company as well. Before that I was a senior consultant on the malware team at Booz Allen Hamilton. And before that I was intern at Secure DNA.

So, why a new tool? There’re a lot of different tools out there that come out all the time. And I believe that there’s a gap that I wanted to fill, especially in the area for Mac malware analysis. I also believe that visualization is a great way to learn how complicated things work, and that’s one of the reasons we created this tool Mach-O Viz. There’re also not many security products out there to analyze Mach-O files – there are a few, I’m going to show you them; I’m going to show you what I’m trying to fill the gap in with. There’s also lack of web-based free reverse engineering tools to use on any device; most of the tools require that you use Windows or Linux or Mac. In this case you could use it on iPad or Android-based device, which is pretty unique. There’s also a strong need, at least from what I hear about, for the ability to quickly identify malicious files and automatically create snort signatures on the fly, especially to people without much training.
Some of the tools that I’ve used that I really enjoy and which gave inspiration to this project are IDA Pro, otool, class-dump, Machoview, ptool, otool-ng, and hopper. A few of these, especially Machoview, have been really helpful in making sure that everything I was doing was correct. So, with this chart (see image below) – some of it is arguable though I did the best that I could to my ability – there’re five categories here: making it graphical, having multiple architectures, making it network security aware, easy to understand, and easy to use.
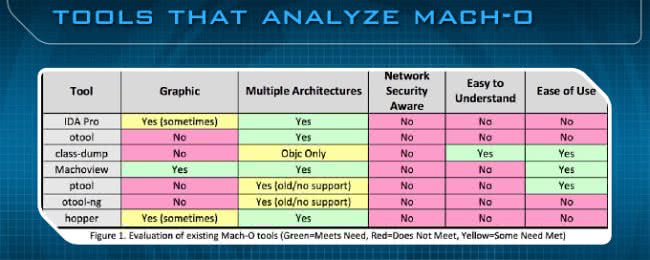
Basically, the goal of the project is to combine the features of all these programs and speed up the process, plus, add this network security element to the mix. Ultimately, at the end of the day, the goal is to help the network defender understand the Mach-O file format better and provide an effective and efficient way to analyze a particular binary for malicious behavior.
With that, introducing Mach-O Viz in beta (see image below): it presents a Mach-O binary in a visual format. For those of you that don’t know what a Mach-O file is, it’s basically the file format used on iOS and Mac devices. If you’re familiar with Windows, you’re going to see PE file format, and for Linux it’s going to be the ELF file format. Basically, Mach-O Viz makes it easier for anybody to see visually how the file is constructed. It might not be that new of a concept: for example, in IDA Pro there’s a little band at the top that shows you the entire file structure broken up. We took that a step further with this tool though, and you’ll see in a minute how that works.

So, you’re going to see the visual representation from the header through the load commands and into the corresponding sections and segments. It’s also interactive, so you could zoom into the segments for more detail.
In addition to that, we also wanted to create a back-end graph and visualization, plus an analytic system for graphing the binary’s disassembly – very similar to what you’re going to see in IDA or hopper, if you’re familiar with them. Currently, we’re only supporting these architectures right now: i386, x86_64 and ARM6/7; again, that’s only for Mach-O but we have the ability and would like to expand it, if there is enough interest, to other architectures. We also wanted to keep this program not only visual but also accessible – that means we could use a web browser and any other type of platform.
More design features: we wanted to keep the back-end as ‘Mac’ as possible, and by that I mean that when Apple updates its specs for the Mach-O file format, which it hasn’t very recently, the tool is automatically already updated because the system is keeping up to date with everything Apple is doing. The whole tool is working in its native environment, and by that it’s always updated and relevant by default. We also get to gain access to the LLVM disassembler for the most accurate assembly we could feed into our analytics engine. We also make use of many of the open source utilities that Apple provides, and many other open source utilities for this project as well.

This (see image above) is the main page of what the application looks like when you go to the website. At the very top you’re going to see a few different things that you can take a look at. The first is the Instructions. Then there’s the White Paper, which I highly recommend you read if you want to really see how to use the application; there’re about three malware samples that are walked through step by step, and this will show you exactly all the features and how to use it. There’s also FAQ and Contact information.
Essentially, all you need to do is upload your binary by clicking on the Upload File button. But before you do that, there’s something I want to mention. This is an actual diagram of an IPA (see image below), which stands for iPhone application, or iPad application; and, essentially, it’s a Zip file. So, if you change that IPA to a Zip and then you extract it, and then open up the payload folder, and then you right-click, you could show package contents, and then inside that you’re going to see an entire directory containing database files, resources, and the actual binary itself.
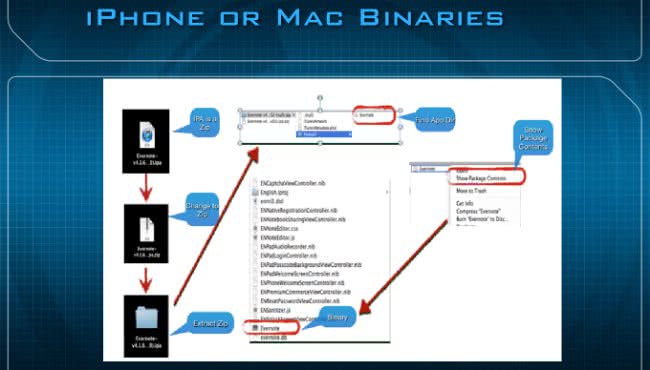
If you’re dealing with one of these binaries, especially, in this case, on the iPhone, you’re going to see two architectures: for Facebook you’ll see ARMv7 and ARMv6, both are Mach-O ARM executables.
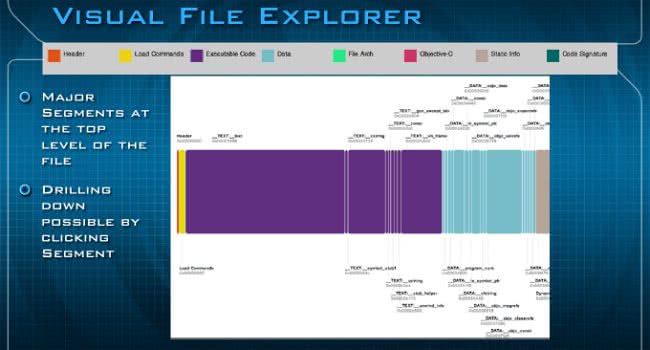
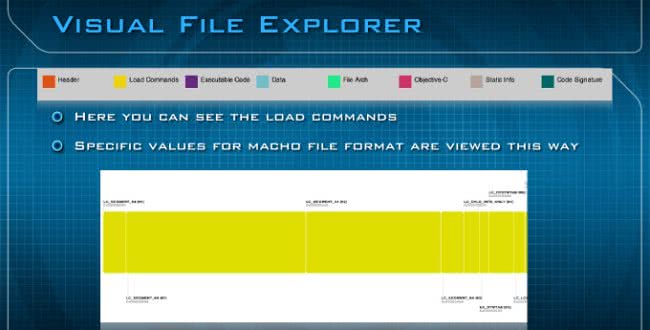
The very top of the application is actually divided in two different parts. This is the Visual File Explorer (see image below), and at the very top you can see that there’s a key that will show you what all the colors mean along the way. So, at the very top you’re going to see the Header, the Load Commands, Executable Code, Data, File Arch (architecture), Objective-C, Static Info, and Code Signature. By clicking on any of these major segments, you basically could drill down to get further information about what is going on inside that file format.
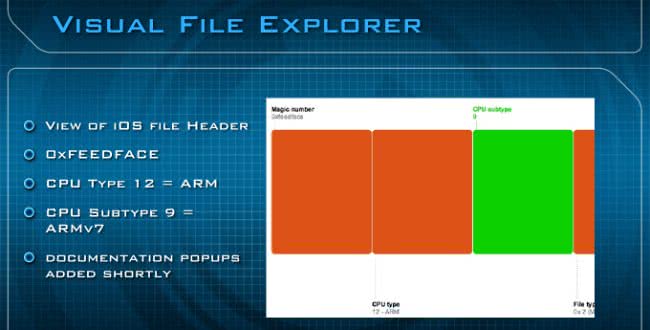
In this example (see image below) I clicked on the file header itself, and you can see the magic number right there, it’s feedface; and then the CPU type which is 12 and the CPU subtype which is 9 – that basically just stands for ARMv7. In the future we’re going to add documentation popups, so if you get to hover over anything it will give you more information about what exactly you’re looking at in the Visual File Explorer.
This is the Load Commands (see image below), another view of what it looks like when you’re drilling down into different parts of the file format itself.
Read next part: Combatting Mac OS X / iOS Malware with Data Visualization 2
