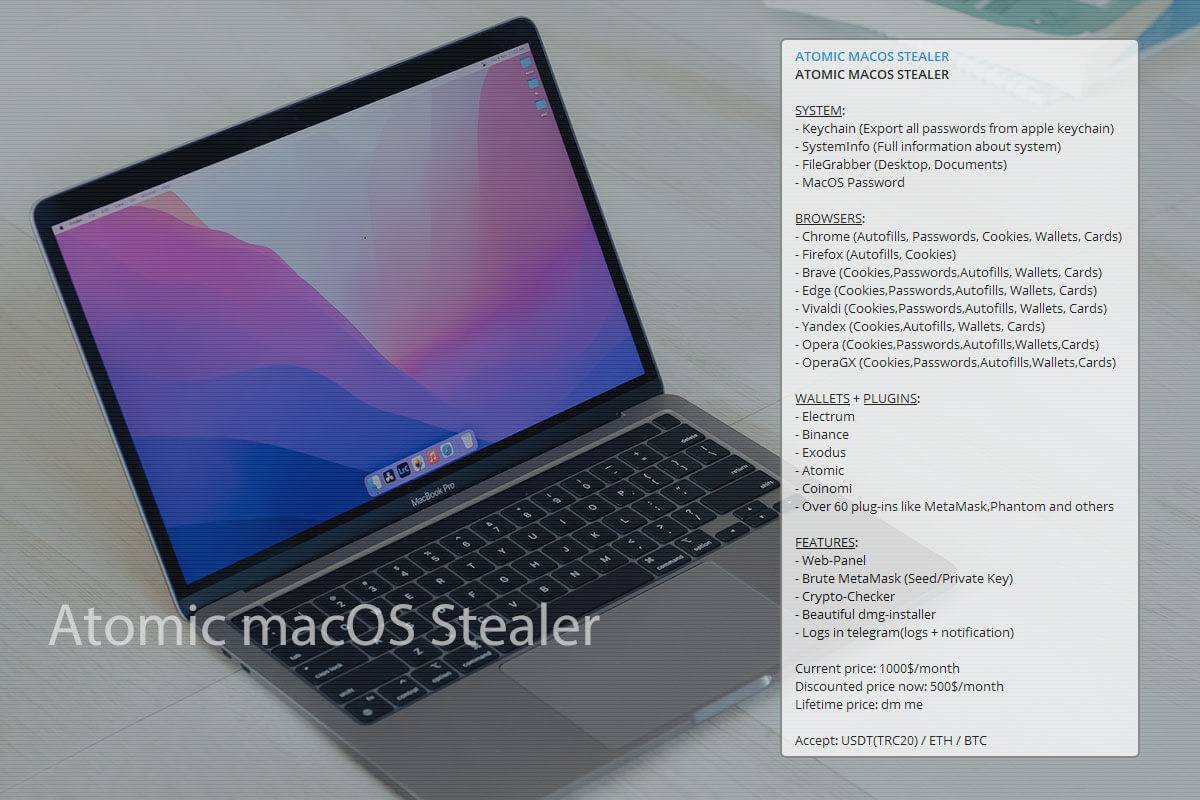
Mac users should be on the lookout for a new sneaky strain of malware called Atomic that harvests sensitive information and quietly sends it to its operators.
Analysts at threat intelligence company Cyble have recently discovered that cybercriminals are advertising new info-stealing malware called Atomic macOS Stealer (AMOS), which as the name suggests, zeroes in on devices with macOS under the hood. The malware is distributed through Telegram, with the subscription fee amounting to $1,000 per month.
For this price, buyers receive a DMG file (Setup.dmg) containing malware written in Go and designed to steal passwords from Keychain, files from the local file system, passwords, cookie files, and banking data stored in browsers. In addition to that, AMOS attempts to retrieve data from more than 50 cryptocurrency extensions and wallets, including Binance, Coinomi, Electrum, and Exodus.
Criminals gain access to a web panel for convenient management of victim data, the MetaMask brute-forcer, as well as a DMG installer. They also have the ability to receive stolen information directly through Telegram.
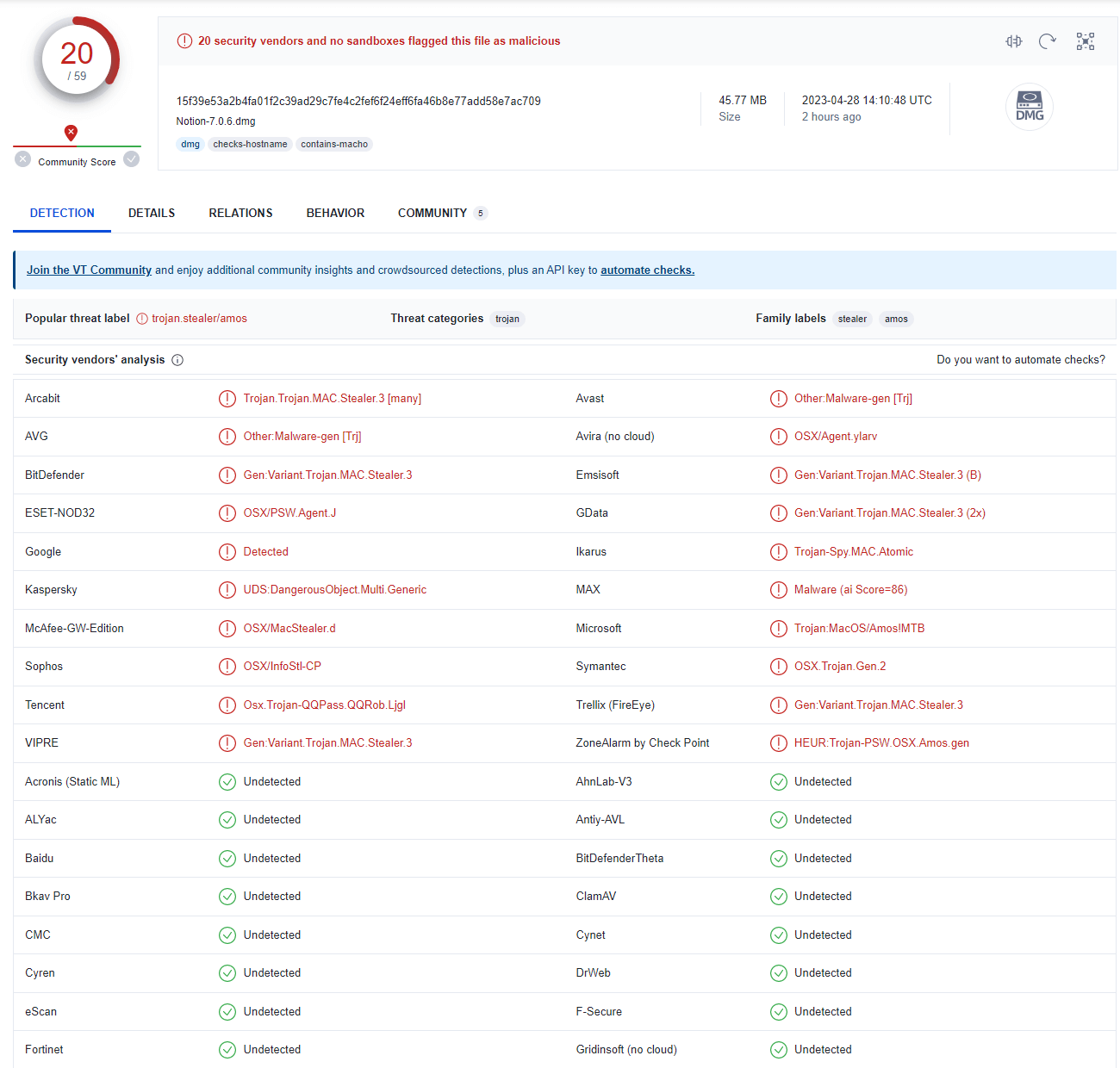
It should be noted that at the time the researchers' report was published, the malicious DMG file flew practically undetected by security products listed on VirusTotal. The distribution of Atomic is entirely the prerogative of its "buyers", which means that the infection vectors may include phishing emails, malicious ads, social media messages, SMS, black hat SEO methods, torrents, and much more.
When the malicious DMG file is executed, the malware displays a fake window for entering the system password, which allows its operators to obtain elevated privileges in the victim's system and proceed to collect data behind the scenes.
Interestingly, cybersecurity experts from Trellix, who also examined this malware, noticed that the IP address associated with Atomic’s Command and Control (C&C) server and the build name are similar to those used by another malicious application dubbed Raccoon Stealer, which suggests that the same threat actors may be behind both threats.