The recent releases of iOS 14.4 and iPadOS 14.4 fix three security loopholes that, according to Apple, may have been used in real-world attacks.
The roll-outs of the latest operating system versions for iPhone (iOS 14.4) and iPad (iPadOS 14.4) unearthed a number of security flaws affecting earlier builds. Apple has acknowledged this by including the corresponding details in its release notes regarding the security content of both platform updates. What’s more unsettling is that, according to the document, malicious actors may have exploited these bugs to compromise vulnerable devices and run dodgy code behind the scenes.
On a side note, Apple is typically reluctant to admit slip-ups that could expose its customers to black hats’ shenanigans. The recent public disclosure in question is a somewhat unexpected, yet welcome move that should encourage users to stay in the clear by updating their mobile devices to the newest version.
What’s known about these vulnerabilities so far?
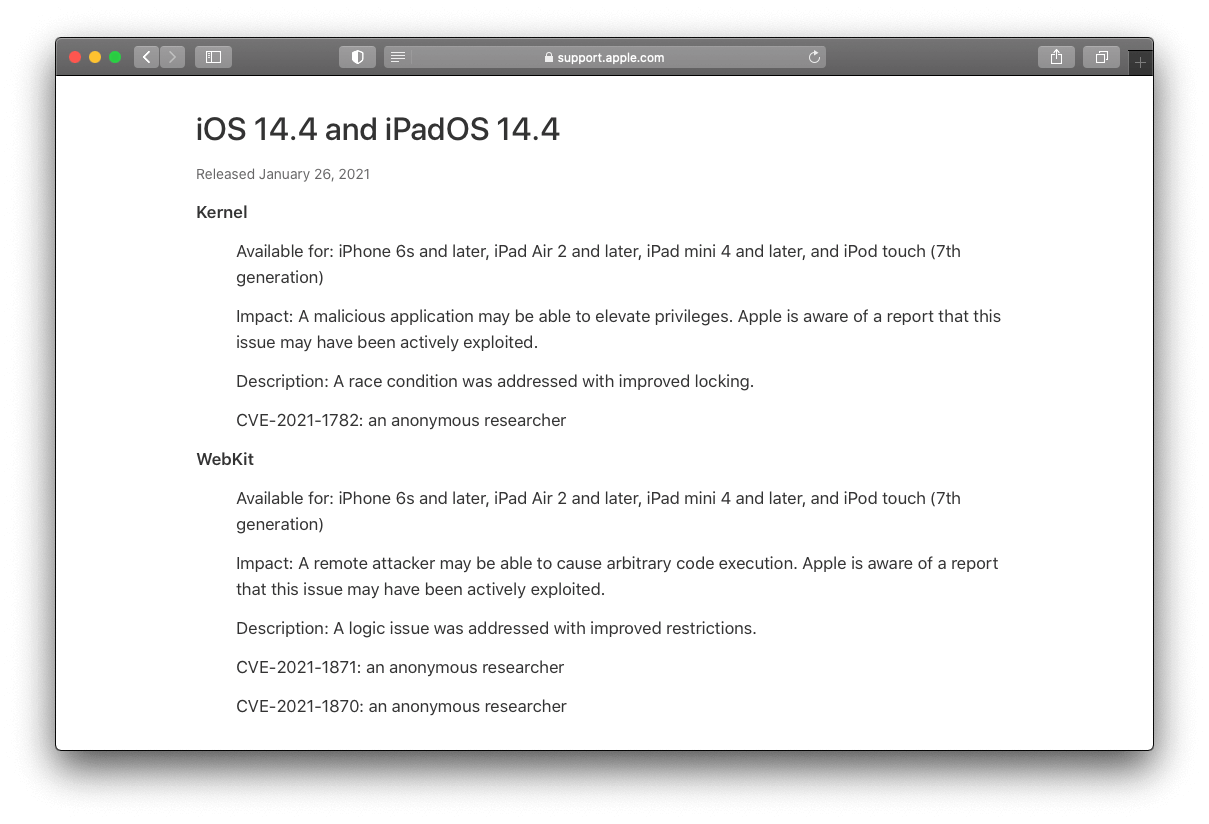
One of the three issues addressed in iOS 14.4 and iPadOS 14.4 is an imperfection in the Kernel, the foundation of the entire operating system. Catalogued as CVE-2021-1782, it allows an offensive application to create what’s called a race condition and thus to elevate its privileges on a device running unpatched versions of the operating system.
The other two vulnerabilities could undermine the integrity of WebKit, Apple’s proprietary browser engine at the heart of Safari. These are tracked as CVE-2021-1871 and CVE-2021-1870. The main sketchy implication of both comes down to arbitrary code execution. This form of exploitation is a common launchpad for injecting malware, which could be an element of a larger infection chain aimed at device takeover.
Judging by Apple’s support documentation, all these loopholes were reported by an anonymous researcher. The company hasn’t provided any further details on the bugs, stating that the investigation is still underway. To avoid being compromised, owners of iPhone 6s and newer, iPad Air 2 and newer, as well as iPod touch 7th generation are urged to head to the “Software Update” section of the Settings app and apply the patches as soon as possible.
In mid-September 2020, Apple published a similar report about a high-severity privilege escalation flaw addressed in an update for iOS and iPadOS. The fact that the iPhone maker does its best to stay on top of such security issues is certainly comforting. But, this isn’t the silver bullet in and of itself, with the rest of the attack countermeasures being up to the users who shouldn’t postpone important updates.
