Apple pulls the plug on a macOS Big Sur feature that gave its proprietary services the green light to get around third-party security and privacy tools.
macOS 11 Big Sur has been the talk of the town since last summer’s WWDC event when it was announced as the biggest overhaul of the famous operating system in more than a decade. While bringing an all-new look and feel along with a handful of feature tweaks to the Mac, this release has also become a subject of criticism among security professionals. One of the most impactful slip-ups boiled down to a bizarre feature called ContentFilterExclusionList. Originally spotted by white hats last October, it allowed Apple’s apps to bypass a number of security and online privacy utilities installed by users. These included third-party firewalls and virtual private network (VPN) solutions.
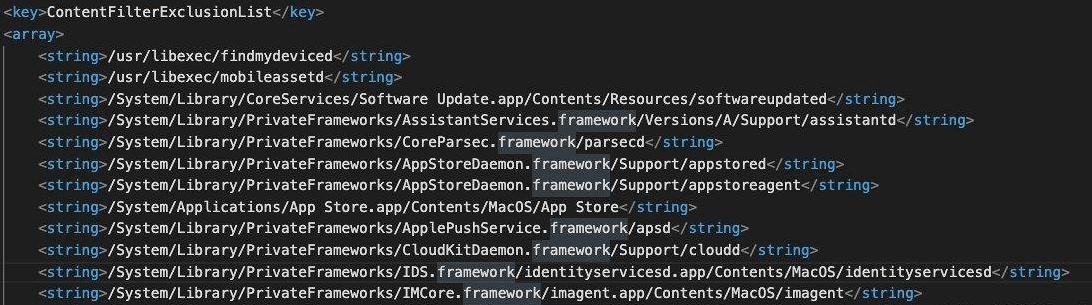
What is ContentFilterExclusionList, anyway?
Simply put, the feature introduced a paradigm in which Apple’s major services such as the App Store, iCloud, and Maps ended up on a list of exclusions that specified which processes could slip below the radar of mainstream macOS tools tasked with monitoring and filtering web traffic. Researchers who spotted this oddity considered it a disastrous move – not because they feared Apple would abuse this privilege of their proprietary services. Instead, the main concern was that Mac malware authors could stealthily inject their code into these trusted apps, only to get the infections running with mind-boggling permissions. Plus, there was a risk of users’ IP addresses and geolocation details being exposed even if they leveraged VPN to step up their privacy online.
The good news
The ContentFilterExclusionList component is missing in macOS 11.2 beta 2, seeded to developers on January 13. It means that Apple has eliminated the whitelist of overly privileged apps, and therefore its services won’t be able to get around essential security and privacy instruments provided by third parties anymore.
In a recent commentary on this matter, the Cupertino company explained that this vexed feature was an interim measure accompanying a transition from the Network Kernel Extensions (NKEs) ecosystem to an improved counterpart called Network Extension Framework. In other words, Apple software developers had simply lacked the time to complete this shift and address all the compatibility-related flaws of their apps before macOS Big Sur public release, which took place last November.
Now that it’s sorted, firewalls and security suites will do their thing no matter what app – Apple’s or not – is being inspected. Furthermore, macOS VPNs should conceal their users’ sensitive data unconditionally.
