Ethical hacker has recently earned a fortune for finding three exploits in Safari that might allow a real attacker to access the camera on iPhone or Mac.
A security enthusiast who thinks and acts like a real attacker is a godsend for technology companies who want to assess their products for weaknesses. Apple has resorted to such outside services for years, but with that caveat that the range of participants in their bug bounty program used to be restricted to “select” researchers. Furthermore, it covered iOS devices only. Things changed in December 2019 when Apple made these initiatives open to the public. Depending on the severity of a discovered security imperfection, the maximum reward can range from $200,000 to $1 million.
An analyst named Ryan Pickren was one of the first to try his hand at vetting the tech giant’s products and has been successful enough in these efforts to earn $75,000 for his work. He unveiled seven zero-day exploits, three of which could allow a real-world perpetrator to gain unauthorized access to the camera feature on both iDevices and Macs.
For the record, a zero-day is a software vulnerability that hasn’t yet been documented by the vendor or third-party research entities. However, it could already be a part of cybercriminals’ toolkit, which potentially entails elevated risks to end-users’ security and privacy. Ryan Pickren was able to pinpoint loopholes in the way Safari implements the Uniform Resource Identifier (URI) Syntax parser. It’s noteworthy that both mobile and desktop versions of the web browser are susceptible to the same bugs. Apple is using a reasonable model where any app that wants camera and microphone permission displays the appropriate request dialog and it’s up to the user whether or not to grant this privilege. Essentially, the logic of the attack is about taking advantage of a previously unknown exception to this rule and thereby getting around the regular authorization workflow.
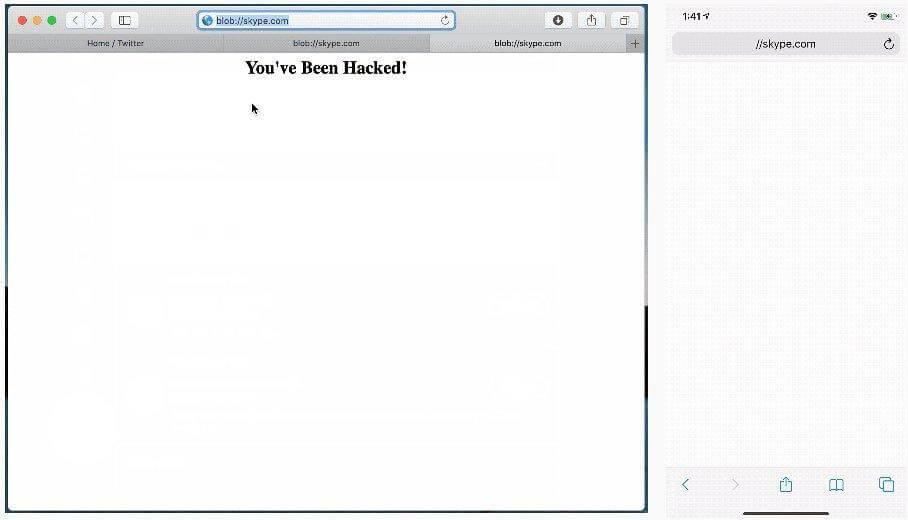
Pickren found a way to hoodwink a user to visit a malicious website in Safari, which became the launchpad for the hack. The landing page is disguised as skype.com, although the URL contains a few extra symbols misinterpreted by the browser as valid ones. The spoofed site is predefined to execute a series of sketchy scripts that pave the attacker’s way toward switching on the device’s webcam remotely and accessing the captured graphics without the user’s awareness. Moreover, the abuse of the mediaDevices Web API on macOS makes it possible for the hacker to additionally access the screen sharing feature.
The researcher reported these flaws in December last year and Apple promptly validated them. It took the company several weeks to roll out a fix for the most severe camera kill chain zero-day. The camera loophole was patched in Safari 13.0.5 in late January 2020 and the rest of the exploits were addressed with the release of Safari 13.1 on March 24.
Meanwhile, some security analysts find it odd that safeguarding the webcam is mostly considered a priority in regards to laptops and desktop machines only. Mobile devices can be much more “verbose” in this context because users always keep them at hand. Furthermore, Pickren’s proof of concept shows that black hats can piggyback on zero-day exploits to target iOS and macOS devices alike, so vendors should rethink their protection strategies to have both realms equally covered.
