Remove System Spot (SystemSpot 1.0) Mac adware to revert to normal web browsing, stop annoying popup ads, and thwart personal data harvesting going on in the background.
A seamless web surfing experience is an awesome thing, no doubt. When adware comes into play, though, harsh deterioration of one’s entire browsing is imminent. Although this category of Mac threats isn’t considered severe in terms of the damage, the nuisance effect is very prominently manifested. Out of the numerous widespread families of PUAs (potentially unwanted applications), which is another common term denoting the adware phenomenon, one species really stands out. SystemSpot, its latest knockoff released in the new decade, is an example of how this cybercrime model works. Just like its precursors IdeaShared, FormList, CoordinatorPlus and many others, its distinctive trait is the green app icon featuring a magnifying glass image inside. It also takes after its clones in that the application name may have a version number next to it, so it could be SystemSpot 1.0 or similar.

The bulk of this malicious entity’s disruption potential is concentrated in the victim’s web browser. The bad news for those infected is that SystemSpot is a cross-browser Mac virus and therefore it runs on Safari, Chrome, and Firefox in the exact same way. It determines which one is the user’s default choice and force-installs its sketchy extension on it. This intrusive helper object then invokes a series of commands that override the original preferences and trigger obnoxious popup activity. A conspicuous element of this impact is that the homepage, search engine and new tab page customizations are replaced with a pseudo search provider or URL affiliated with an advertising platform. The outcome is a loop of redirects the victim is dragged into without a slightest hue of consent. In some cases, the landing page is a legit web resource such as Bing or Yahoo, but this is just a distraction trick as the browser covertly resolves a number of ad networks before it gets there. The goal of this foul play is to generate fraudulent revenue by redistributing the normal web traffic originating on the plagued Mac.
Another big issue with SystemSpot virus is that it perpetrates an extremely irritating ads injection artifice. This is one more objective the harmful extension is preassigned to fulfill. It causes the compromised web browser to display an extra layer of content across the sites the user goes to. This virtual coating hosts sponsored materials that come in the form of banners, interstitial adverts, coupons, popup ads saying “Brought by SystemSpot”, and in-text links. The amount of this third-party information can get too large for the user to view the whole web page structure and presentation properly, not to mention that the splash screens being furtively opened in the background all the time become a burden for the infected Mac and lead to system slowdown. The hyperlinked text ads scattered here and there are also a drag because the victim can accidentally click them, only to be forwarded to a worthless offer that can be difficult to close. It’s also unnerving that the adware collects personal data to show targeted advertisements.
Although SystemSpot virus may seem to infiltrate a Mac out of the blue, there is a good deal of user involvement in this process. However, this isn’t an informed decision type of thing. The operators of this threat attach the payload to other applications that arrive in bundles. On the face of it, the installer looks regular and harmless but its “recommended” or “express” (default) option doesn’t cover all the components, making the unsuspecting user focused on the benign one only. As a result, the PUA is installed along with a harmless program as long as the would-be victim opts for the quick setup mode. In light of this growingly common infection vector, it’s a good idea to select the custom installation option that will list all the items and provide a way to deselect the ones that appear fishy. In case the SystemSpot distribution hoax has worked out and the virus is already onboard, here is what to do to get rid of it and fix the affected web browser.
SystemSpot virus manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
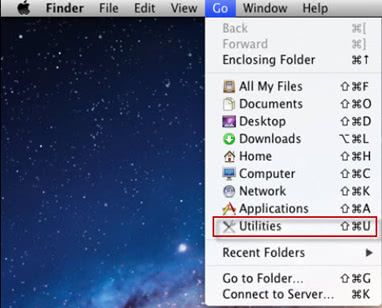
- Open up the Utilities folder as shown below

- Locate the Activity Monitor icon on the screen and double-click on it

- Under Activity Monitor, find a process named SystemSpot, select it and click Quit Process
- A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
- Click the Go button again, but this time select Applications on the list. Find the SystemSpot entry on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it

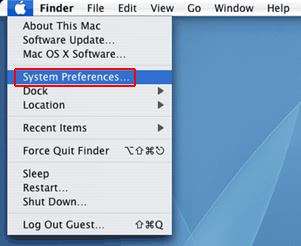
- Now go to Apple Menu and pick the System Preferences option

- Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the box is started up. Locate SystemSpot or other potentially unwanted object there and click on the “-“ button
Get rid of SystemSpot App activity and ads in web browser on Mac
To begin with, settings for the web browser that got hit by this virus should be restored to their default values. The overview of steps for this procedure is as follows:
- Reset Safari
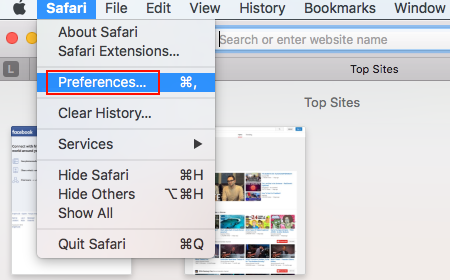
- Open the browser and go to Safari menu. Select Preferences in the drop-down list

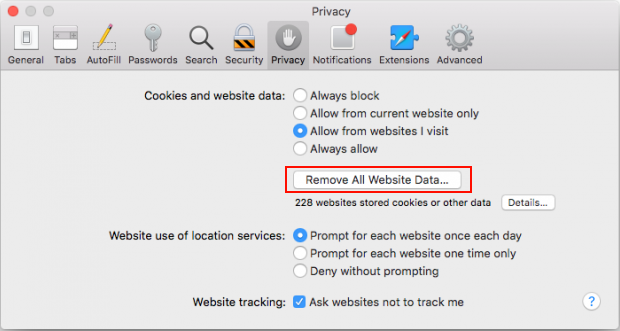
- Once the Preferences screen appears, hit the Privacy tab at the top. Find the option that says Remove All Website Data and click on it

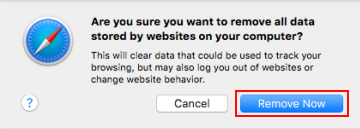
- The system will display a confirmation dialog that also includes a brief description of what the reset does. Specifically, you may be logged out of some services and encounter other changes of website behavior after the procedure. If you’re okay with that, go ahead and click the Remove Now button

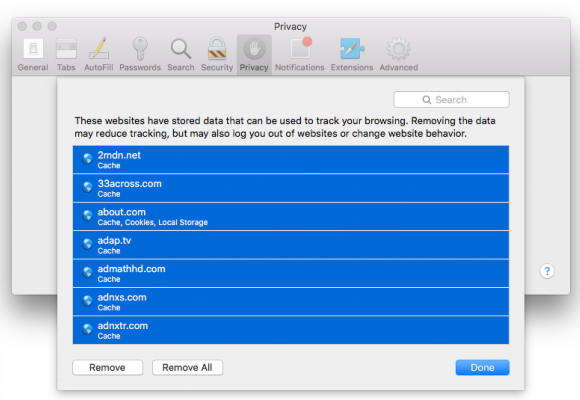
- In order to selectively clear data generated by certain websites only, not all of them, hit the Details button under the Privacy section of Safari Preferences

- This feature will list all websites that have stored potentially sensitive data, including cache and cookies. Select the one, or ones, that might be causing trouble and click the appropriate button at the bottom (Remove or Remove All). Click the Done button to exit.
- Open the browser and go to Safari menu. Select Preferences in the drop-down list
- Reset Google Chrome
- Open Chrome, click the More (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down
- When on the Settings pane, select Advanced
- Scroll down to the Reset settings section. Under the Restore settings to their original defaults option, click the Reset settings button

- Confirm the Chrome reset on a dialog that will pop up. When the procedure is completed, relaunch the browser and check it for malware activity.
- Reset Mozilla Firefox
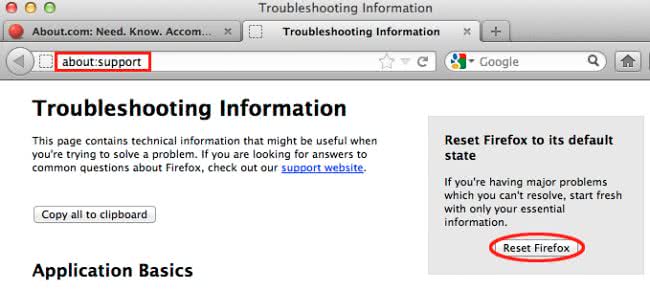
- Open Firefox and select Help – Troubleshooting Information
- On the page that opened, click the Reset Firefox button

Get rid of SystemSpot using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove SystemSpot virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the SystemSpot issue using Combo Cleaner:
- Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
- Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
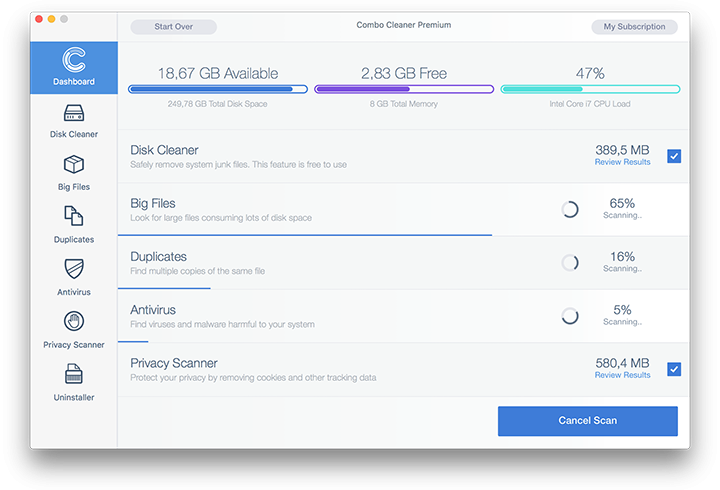
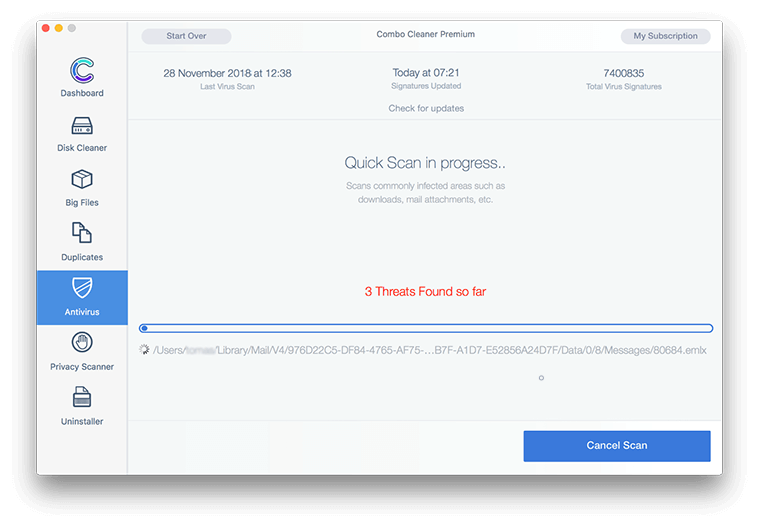
- Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.

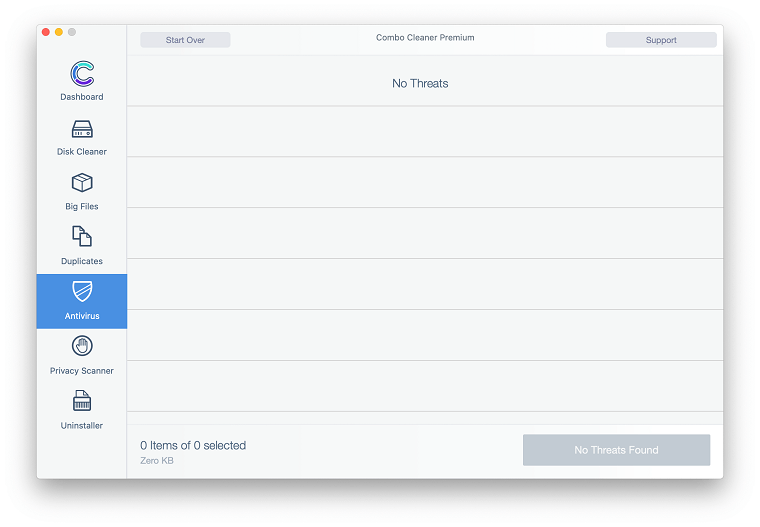
- Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).

- In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove SystemSpot threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.

- Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.