This is the right place to get the lowdown on the anatomy of the Cryptonight virus attack on Mac and fix the annoying problem in several simple steps.
The current cryptocurrency ecosystem is seeing a huge spike in light of the steady increase of Bitcoin value that seems to be getting blown out of proportion, frankly speaking. Anyway, the unlimited opportunities associated with unregulated digital cash have given rise to the new gold rush, with its benign and shady facets. One of the ways to succeed in this competitive cyber environment is to mine coins. In layman’s terms, it means using computing power to solve complex mathematical puzzles which, in turn, bolster the security of the so-called cryptocurrency ledger. There is, however, a thin line between legitimate and malicious cryptocurrency mining. While some people and companies invest in hardware to do it, others go an easier route and leverage malicious code like Cryptonight to get rich.

How exactly does this questionably ethical scheme work? Once the above-mentioned infection, also referred to as JS:Cryptonight [Trj], takes root on a Mac computer, it parasitizes on the machine’s processing resources such as CPU and GPU. The motivation for doing so is to mine cryptocurrency known as Monero. The nefarious part of this whole tactic is that the code harnesses one’s hardware power without asking for the user’s consent. As a result, the Cryptonight virus has an appreciable system footprint. The Mac will start running much slower than usual, seemingly for no apparent reason.
The only red flag some users encounter is that their antimalware solution recurrently displays security alerts reporting JS:Cryptonight Trojan on their Macs. According to these notifications, the culprit’s location path is private-var-db-uuidtext (see screenshot above). Some AV vendors, though, have admitted this is a false positive due to macOS changes made in the course of the latest update. In particular, Apple may have created a new file that exhibits the behavior of an unauthorized cryptocurrency miner, and the security suites’ heuristics identify it as a threat.
One way or another, the JS:Cryptonight entity does not belong on a healthy Mac. But how does it get inside in the first place? The infiltration vectors may vary, but it’s most likely that the user ‘caught’ the pest when downloading some programs from uncertified web resources. Cybercriminals are known to leverage application bundling heavily, where a malicious app slithers its way into a Mac alongside a legit one so that the user doesn’t know. Once on board, the Cryptonight virus invokes commands to launch stealthy JavaScript code that exploits the machine’s resources to mine Monero cryptocurrency while running in the background. Luckily, the removal of this infection is a no-brainer. The part below will walk you through this process.
Cryptonight malware manual removal for Mac
The steps listed below will walk you through the removal of this application. Be sure to follow the instructions in the order specified.
• Open up the Utilities folder as shown below
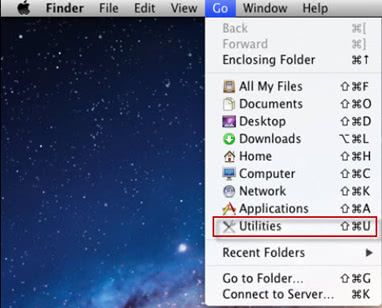
• Locate the Activity Monitor icon on the screen and double-click on it

• Under Activity Monitor, find the entry for Cryptonight, select it and click Quit Process
• A dialog should pop up, asking if you are sure you would like to quit the troublemaking process. Select the Force Quit option
• Click the Go button again, but this time select Applications on the list. Find the entry for Cryptonight on the interface, right-click on it and select Move to Trash. If user password is required, go ahead and enter it

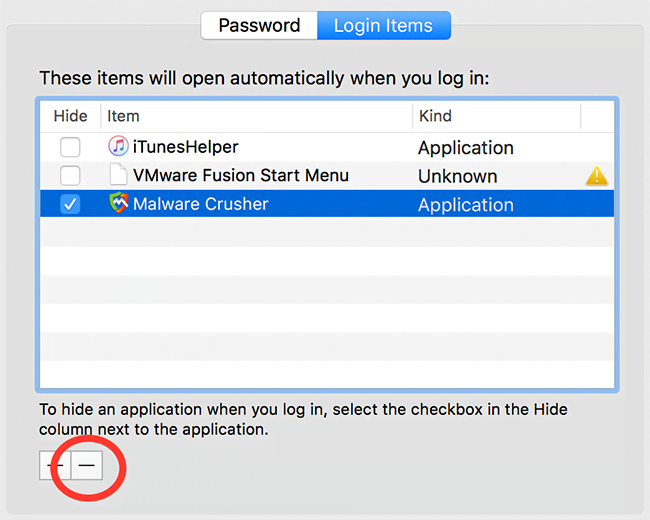
• Now go to Apple Menu and pick the System Preferences option
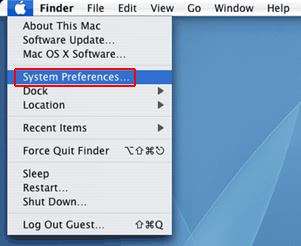
• Select Accounts and click the Login Items button. The system will come up with the list of the items that launch when the box is started up. Locate Cryptonight there and click on the “-“ button
Use automatic tool to uninstall JS:Cryptonight malware from your Mac
Unless you are a power user, you run the risk of failing to find and delete some components of this infection on your own. Overlooking dodgy LaunchAgents, LaunchDaemons, and malicious configuration profiles means that the threat will continue to cause problems. A more efficient alternative to manual cleanup is to use MacBooster 8, an application that will scan your Mac for issues and fix them automatically.
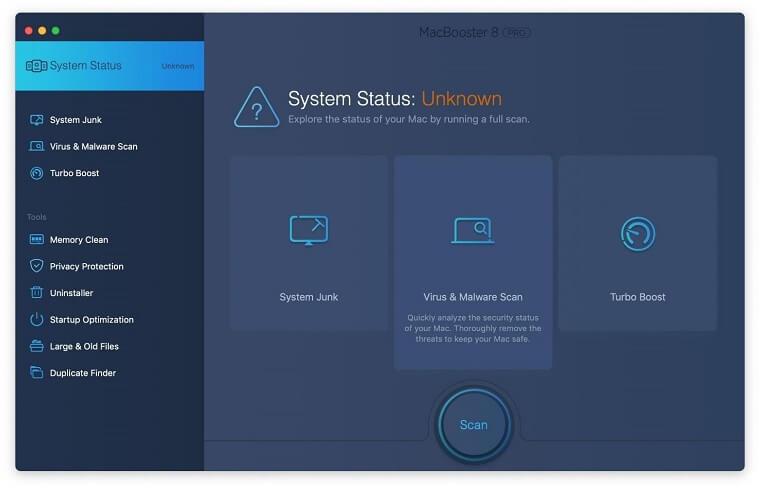
The app comes with a competitive toolkit that includes Virus & Malware Scan as well as a decent range of optimization features. Therefore, not only does it identify and vanquish mainstream Mac viruses but it also releases disk space and memory so that your computer gets a performance tune-up. Here’s how to go the route of JS:Cryptonight Trojan removal with MacBooster:
- Download and install MacBooster 8.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Pro version of MacBooster.
- Open the app. When on the System Status screen, click the Scan button to check your Mac for viruses, junk files, and memory hogs.

- Once the scan is completed, inspect the report to see what security threats and performance issues have been found. To get rid of the detected items, click the Fix button at the bottom.

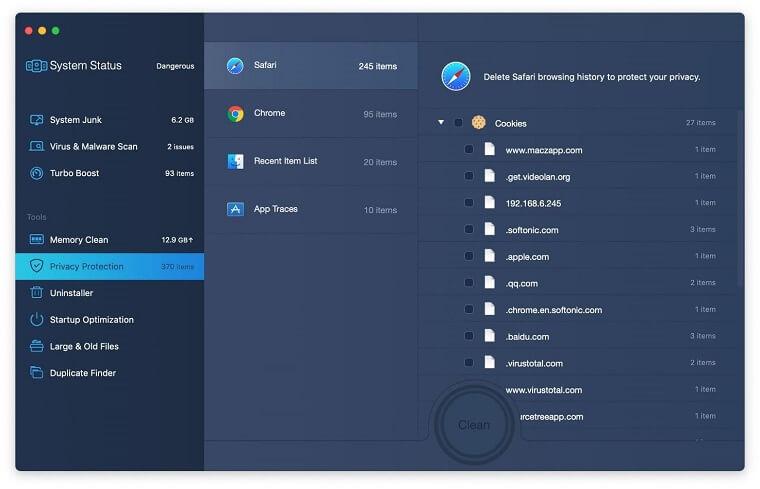
- As an extra step, you might want to make sure that the JS:Cryptonight Trojan infection leftovers are no longer riddling your web browser. This can be the case in an adware scenario. Proceed to the Privacy Protection feature in the left-hand sidebar, select the default browser in the list, and click the Clean button.

- In case your web browser is still acting up, follow the steps provided in the previous section of this guide to get rid of the adverse web surfing interference for good.