Learn how the OSX/Dok Mac malware spreads, how it manifests itself when inside a machine, what objectives it pursues, and how to remove it from infected Mac.
Prior to the emergence of OSX/Dok menace, Mac malware overall had not been nearly as much of an issue. Also referred to as OSX.Dok, this stealth and highly harmful application poses a serious threat to a victim’s privacy. It is involved in a large-scale identity theft scheme via intercepting one’s online traffic. With this whole sophistication in place, the baddie spreads in an old school way. In particular, it is mostly making the rounds in Europe with deceptive email messages impersonating tax administration. The contagion proper is a file named Dokument.zip enclosed in these phishing emails. When an unwary recipient tries to open this file, a dialog prompt actually says it’s an application rather than a document. However, not everyone reads those popups, so chances are the malicious app is fired up.
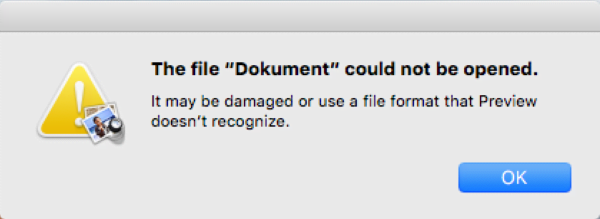
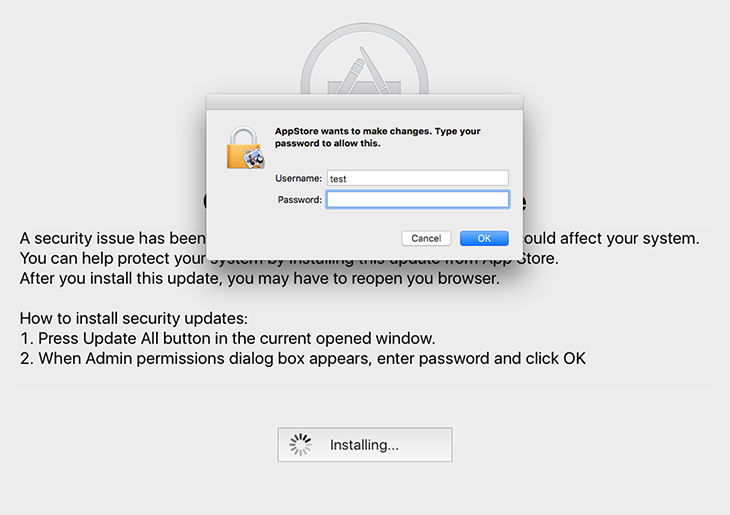
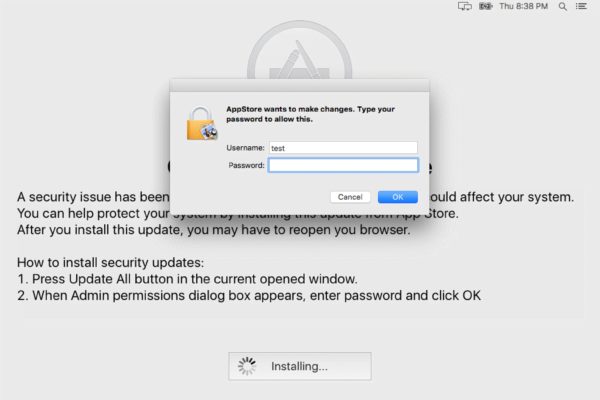
The further attack chain engages another alert that says the file may be damaged. No matter how many times the victim clicks the OK button, it won’t go away for a while. This is a trick aimed at distracting the user from the bad things going on backstage. The malware adds a new rogue application called “AppStore” to the Users/Shared/ folder and login items to make sure it is launched upon every Mac machine startup. This process is followed by a spoof “OS X Updates Available” message occupying the whole screen. It says, “A security issue has been identified in a OS X software product that could affect your system.” Having clicked the “Update All” button on there, the plagued person will be presented with an authentication prompt on behalf of the phony AppStore program requesting the administrator password. If the password is entered, OSX/Dok gets root privileges on the system.
The next phase of the compromise revolves around installing a number of tools onto the target Mac. The first one is a command-line setup solution called Homebrew. The latter then downloads and installs some additional utilities, including Socat and Tor. There is a strong reasoning behind OSX.Dok doing this – it leverages said tools to route all of the victim’s regular and SSL-protected Internet traffic via a malicious server operated by the crooks in charge. These changes can be seen under Network – Proxies, where the proxy configuration value defaults to a wrong URL. To enhance its interference with web surfing and man-in-the-middle attacks, the malware also adds a new valid root certificate called “COMODO RSA Extended Validation Secure Server CA 2” and installs two LaunchAgents, com.apple.Safari.proxy.plist and com.apple.Safari.pac.plist.
At the end of the day, OSX/Dok gets sufficient privileges to harvest the victim’s personally identifiable data (PID) online, including passwords they type on sites, and manipulate proxy settings to inconspicuously substitute genuine web pages with malicious replicas. Although troubleshooting isn’t easy in this case, you can remove the malware by sticking to the following step-by-step removal tutorial.
OSX/Dok manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the order specified.
• Open up the Utilities folder as shown below
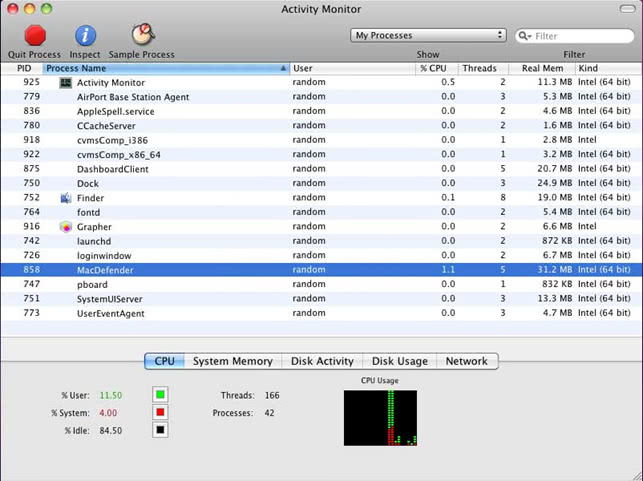
• Locate the Activity Monitor icon on the screen and double-click on it

• Under Activity Monitor, find com.apple.Safari.pac.plist, com.apple.Safari.proxy.plist (or other dubious-looking objects), select them and click Quit Processfor each
• A dialog should pop up, asking if you are sure you would like to quit the above LaunchAgents files. Select the Force Quit option
• Click the Go button again, but this time select Applications on the list. Find the entries for Homebrew, Socat, and Tor on the interface, right-click on them and select Move to Trash. If user password is required, enter it
• Now go to Apple Menu and pick the System Preferences option
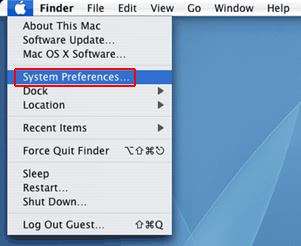
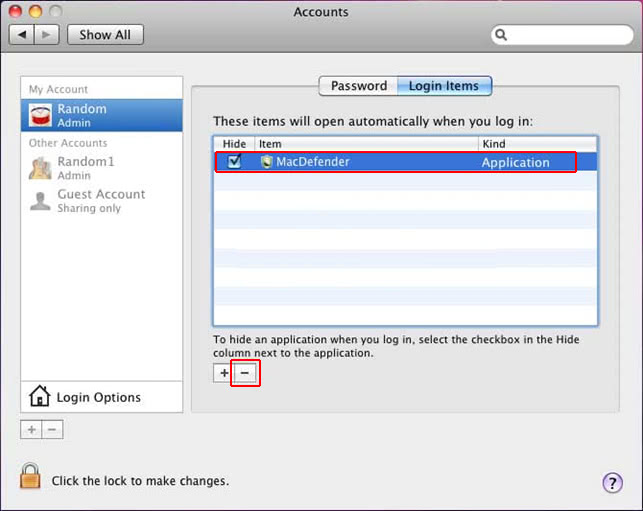
• Select Accounts and click the Login Items button. Mac OS will come up with the list of the items that launch when the box is started up. Locate com.apple.Safari.pac.plist, com.apple.Safari.proxy.plist or other suspicious entries there and click on the “-“ button
Get rid of OSX.Dok virus using Combo Cleaner automatic removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove OSX/Dok malware virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the OSX/Dok malware issue using Combo Cleaner:
- Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
- Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
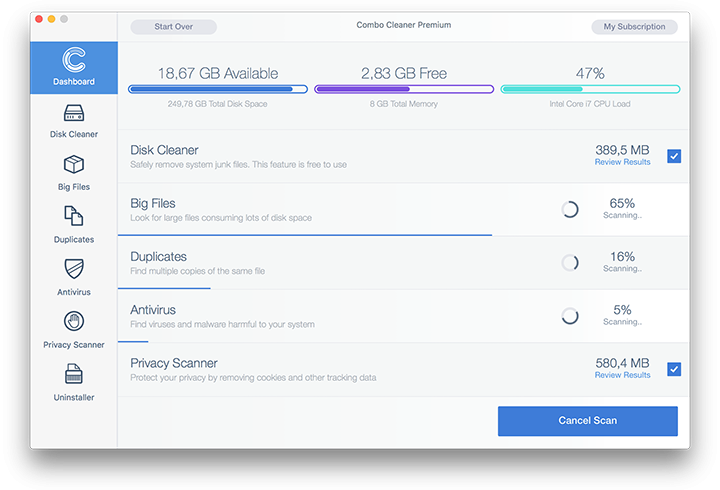
- Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.

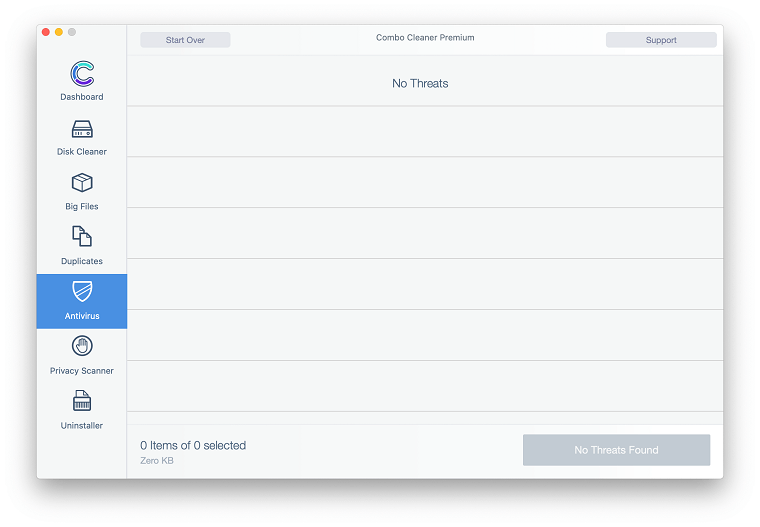
- Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).

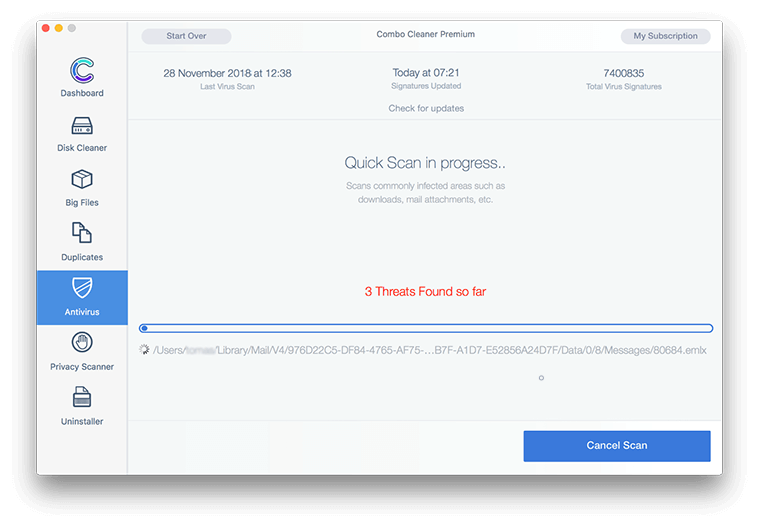
- In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove OSX/Dok malware threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.

- Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.