Follow the instructions step by step to cease the troublesome web traffic rerouting to wbredirect.com by effectively removing the malware that causes them.
XcodeGhost has been in the news a lot lately, which is natural because it is believed to be the most sophisticated and massive attack against App Store users. The fraudsters have come up with a method to affect several parties involved in application-making, distribution and use in one shot. Most of the contamination reports have been coming from China as the malicious code was prevalently injected into apps that enjoy popularity in said country. These include WeChat, Didi Kuaidi, CamScanner, China Unicom Mobile Office, Angry Birds 2 and many more, with the accurate total quantity unknown at this point, ranging from 30 to 300. In any event, as per the cumulative user base that’s potentially subject to this compromise, millions of iPhone and iPad users might be in trouble.

The assault has been heated up by wrong choices that iOS app creators were making. Instead of sticking to official version of the Xcode integrated development environment, some authors would download and use a re-engineered variant, known as XcodeGhost, from the cloud file sharing service provided by Baidu. The why’s for this decision should probably be viewed in the context of Internet connection speed and bandwidth in some parts of China, where developers prefer downloading a smaller file over a certified big one. Consequently, all apps built and compiled with the spoof IDE pose a potential risk to anyone downloading them.

When the twisted version of WeChat, CamScanner or random affected app ends up on an iOS device, it acts in a malicious fashion while looking perfectly normal on the outside. These applications harvest information about the gadget, including the network type, the UUID, device name, language and country. The collected details get encrypted and uploaded to the criminals’ C&C. Although the list of privileges to access this sort of data is fairly common for the average iOS apps, things may go awry if the info goes into the wrong hands. One of the most disturbing characteristics of the malware is its ability to read data stored in the clipboard, making the danger of sensitive information theft real, in particular when a password management tool is used on the device.
The countermeasures for XcodeGhost attack are pretty simple. First off, the iOS user should find out if their installed apps are infected – an automatic scanning solution can do the trick. Secondly, all apps flagged ‘malicious’ are to be uninstalled as soon as possible. The products can be reinstalled later on, once the healthy versions become available.
Get rid of XcodeGhost virus using Combo Cleaner automatic removal tool
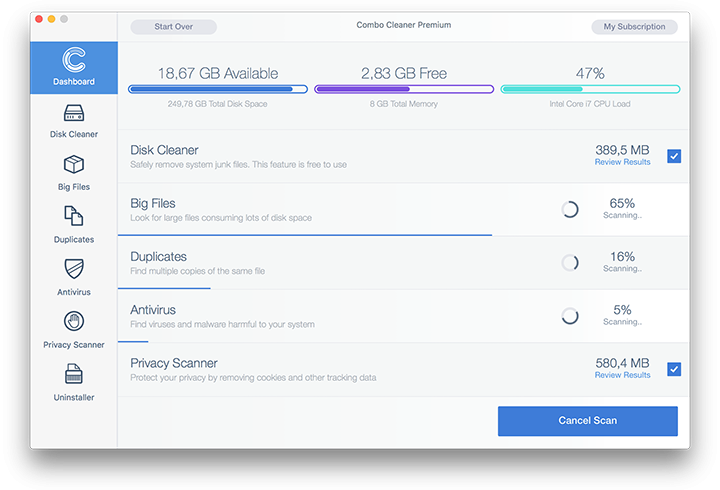
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove XcodeGhost malware (Xcode Ghost) virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the XcodeGhost malware (Xcode Ghost) issue using Combo Cleaner:
- Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
- Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
- Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.

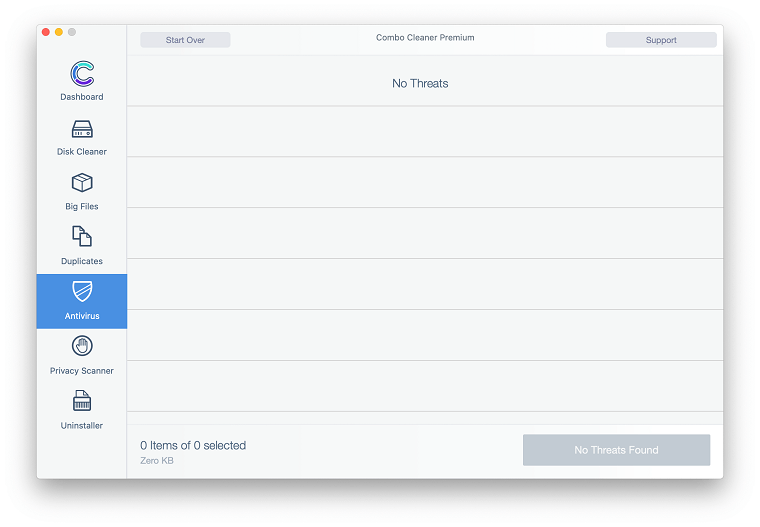
- Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).

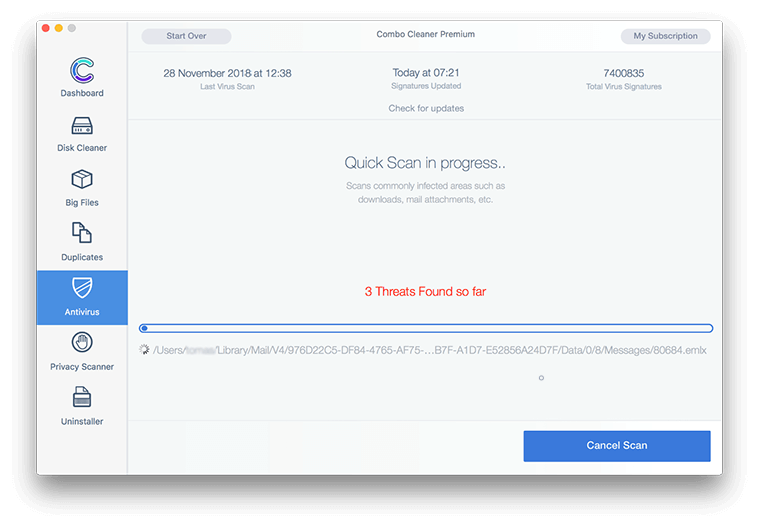
- In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove XcodeGhost malware (Xcode Ghost) threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.

- Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.