Read previous part: Reverse Engineering Mac Malware 2 - Mach-O Binaries
The issues described and analyzed in this part are all about dynamic analysis of Mac apps, including virtualization, application tracing and applicable tools.
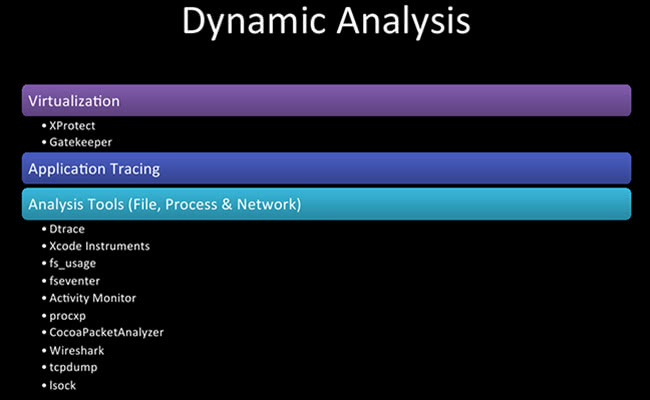
So, some dynamic analysis – now we are getting into where we are throwing it up in a VM, executing it and fooling around a bit to see what it does.
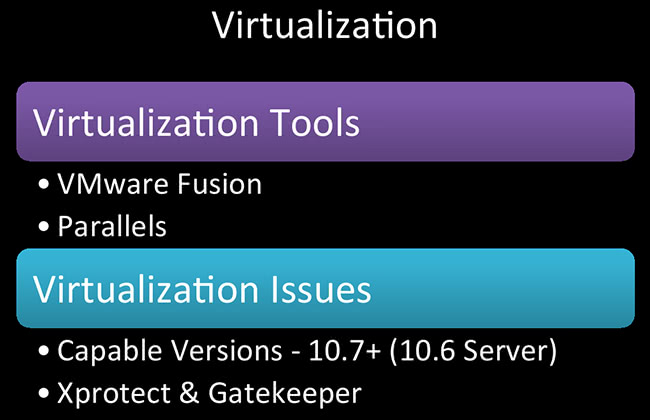
Virtualization, VMs for Mac – relatively a good thing. Apple did not want to do this. As of 10.6 server, you can virtualize that; as of 10.6-not server, you can’t do it. But everything 10.7 and above, you can virtualize in VMware Fusion, Parallels, there are probably some other programs out there. I don’t know if you can do it in VirtualBox. I hear VMware ESXi runs really well in a Mac Mini. So, yeah, you got options there. It’s something that you didn’t have until 10.7 came out about two years ago, so this is relatively new. This works great for research, too. I have so many Mac VMs it’s ridiculous.
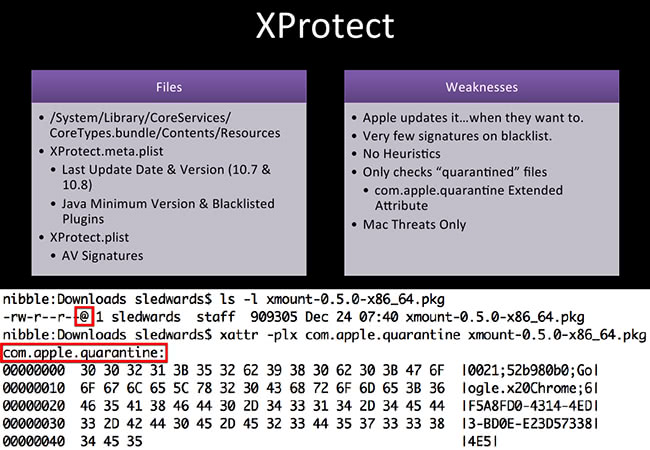
So, we have XProtect. XProtect is a signature based antivirus product built into OS X. This is Apple’s AV. Here’s a couple of the files you might want to look at, like /System/Library/CoreServices; XProtect.meta.plist, when it was last updated and what version it’s at; there’s a couple of blacklisted plugins, so all those Java plugins where Apple is like “Oh, no, no, you cannot run that, that is bad.” I know it’s bad, a lot of Java, a lot of Flash. The other one is XProtect.plist file. This one will contain all your signatures. The last time I checked I feel like it was 30 something items with, maybe, multiple signatures underneath that. So, as compared to a professional AV product or a free AV product by a third party, they are very small in terms of signatures.
So, these are some of the weaknesses with XProtect: Apple updates it on their own terms, and they update it silently, you don’t know it’s happening unless you are capturing with Pcapture or something like that. There are very few signatures, no heuristics, and it only checks “quarantined” files, so that’s the key. On the screenshot down here, if you have ever looked into Terminal before - and some people who are new to Mac might not know this - with that little @ symbol you can do long listing in Terminal. That means you have extended attributes. Mac loves attributes. There’s so much metadata, there are dates, there is so much forensic goodness. You can totally nail people with their metadata; they do not know it’s there.
One of the examples here is the com.apple.quarantine. When you launch an executable and it has this extended attribute attached to it, it will run it through XProtect, run it through the signatures and see if it matches any of those signatures. In the next slide I’ll show you what will pop up. So, com.apple.quarantine quickly just tells you where it was downloaded from, when it was downloaded – just where and when and some other identifying information.
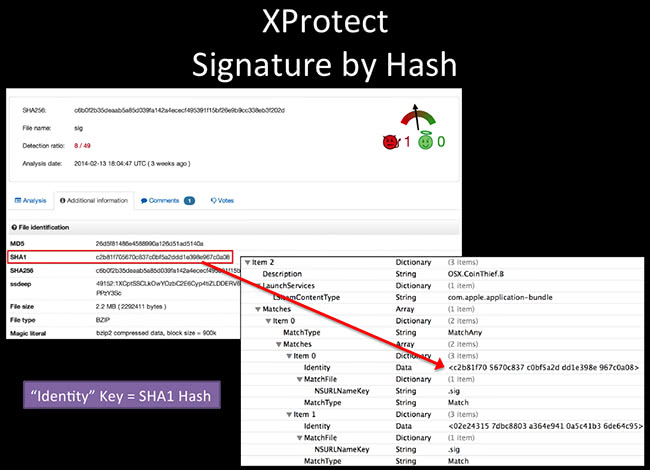
This is the XProtect.plist file. This is an example of CoinThief. That one came out just a few months ago. That was the Bitcoin miner, so it steals your wallet. I’ve really wanted to try and find a sample of that, so I have one by now. So this one, if you take out the Identity data here – that is just a SHA1 hash of the files that it’s looking for. No heuristics, it’s only looking for a hash. If this executables matches that hash, it won’t execute it – good to go. You can change your hash quite easily, so it does protect that well.
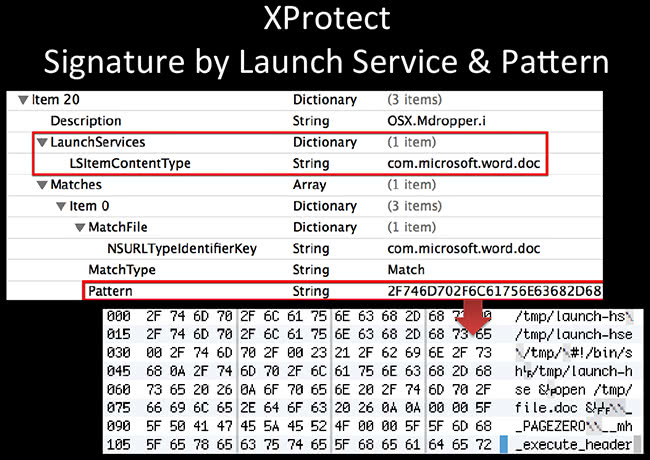
It also looks for things that get executed along with it. This one is an example of Mdropper. It’s looking for, you know, when you launch Microsoft Word. And then if you extract this pattern down here, it’s also looking for script contents, so tmp/launch, bin/sh and file.doc. What it does is it looks like it’s opening up a document and in the meanwhile it’s pwning you in the background.
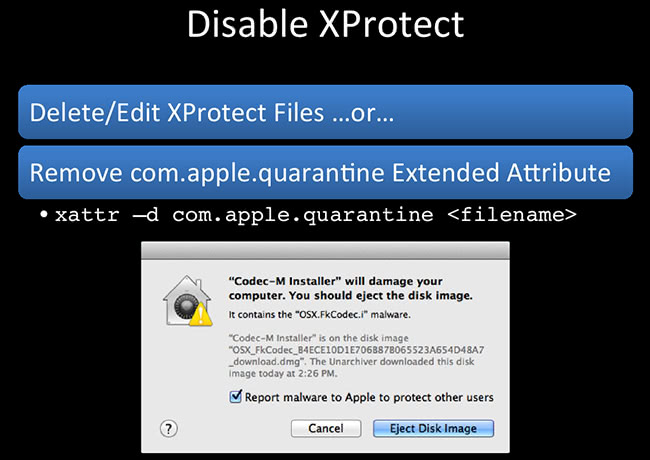
So, Xprotect – you should only disable it on your VMs, don’t do this on your real box – it is crappy, but you should have it running. A couple of things you could do here: this is the box that you might get; I tried to open this Codec-M Installer. This is the warning that you get, it says “No, I’m bad, don’t open me.” Okay, how can you run this thing? Delete or edit the XProtect files, you can remove all contents of it. If it’s an offline VM it shouldn’t be updating anyway, so hopefully it should not have any issues. Or you can just kill off the com.apple.quarantine extended attribute: xattr is a native tool. Basically, it interfaces with extended attributes - you can print them, you can delete them, you can create them; pretty nice utility. So, -d will delete the quarantine and you should be good to go.
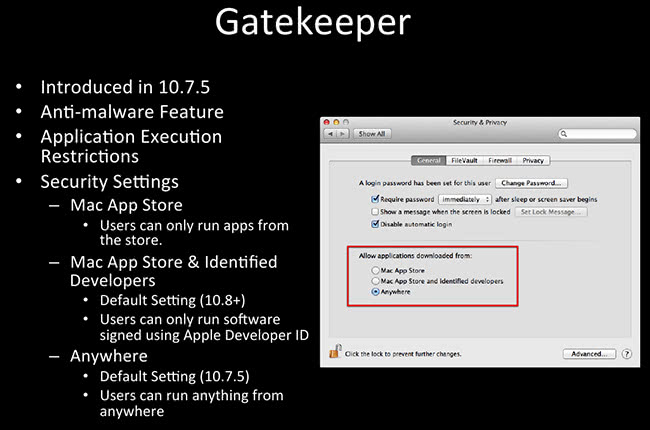
Gatekeeper has an anti-malware feature. This came around in about 10.7.5, and it restricts the execution of certain programs. So you get three options. On the screenshot here, you can see it’s the Security & Privacy preferences panel, you get three options: “Mac App Store” (run only things from Mac App Store). The second option is “Mac App Store and identified developers”. Remember the KitM? It’s still going to run this way. This is the default as of 10.8, so you are still going to get owned by the KitM (Kumar) malware. There’s also the “Anywhere” option, which I of course have selected. “Anywhere” means you can run anything from anywhere, it doesn’t matter what. So be sure to select this option so that Apple runs some of this malware.
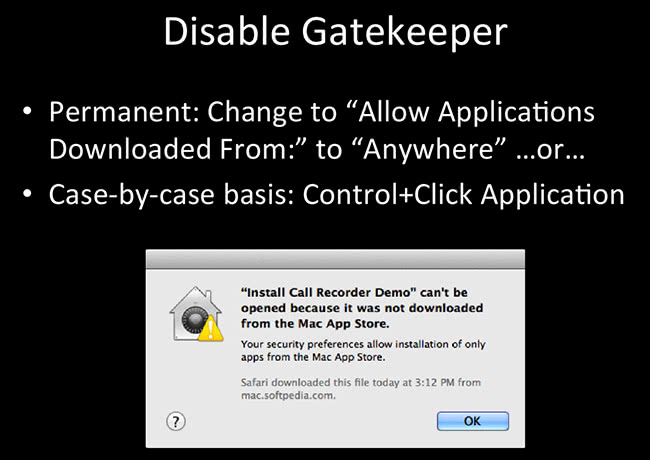
I got this message when I tried to install some weird “Call Recorder Demo”, some crazy thing that I downloaded from Softpedia. There’s so much malware on Softpedia. So I changed the “Allow Applications Downloaded From: …” to “Anywhere”, or on a case-by-case basis you can Control+Click and execute the application, click OK – and it will execute.
Application tracing – I have a slide on this because it’s pretty much the basis of all the analysis tools. Has anybody ever heard of Dtrace? So, application tracing is low-level logging, it’s incredibly verbose, has a lot of information a lot of people may not understand, so I’ll try to simplify it for you. It’s usually meant for debugging and programming folks, but it’s super-useful for reverse-engineering as well. A couple of software samples that use it are, definitely, Dtrace, fs_usage which is a default native program, and the Xcode Instruments application.
Dtrace is great! This came around 10.5, it’s built in, it’s designed by Sun Microsystems. There’s a whole book on it I highly recommend. It’s a hefty book. If you want to know anything about Dtrace, go to dtracebook.com, go ahead and get the book, it will be very worthwhile for you. I’ve been making my way through it, there’s tons of information there. They have code samples, and you can download the code samples on the website here. This lets you interface with a lot of the low-level stuff: network, file system, CPU, memory. So even if you are doing research that’s completely non-reverse engineering but more system research, this has the stuff that you really want to learn. It’s very awk-like, so anybody who does old-school awk stuff can still use it and program in it quite easily.
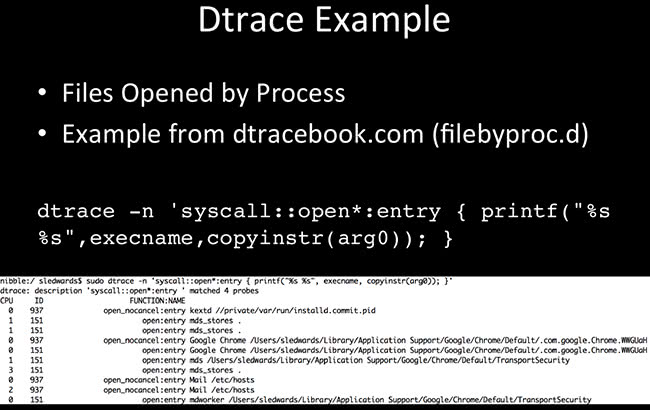
One of the examples here: this is an easy one-liner. This is files opened by process. You execute malware, you want to see what processes are opening and what files are opening. So, quick little things like syscall::open, and on the screenshot here we have CPU, probe ID (the function that it’s probing or looking for), the application, and the file that it’s opening.
Xcode Instruments is the GUI version, and I’ll use the term “version” loosely because it has as much functionality as Dtrace, but Dtrace is a small part of the Instruments as a graphical version of it, but it has a lot more functionality built into it. You can look at this and play around with it for hours, it’s really neat. Most people don’t know it’s there, it’s installed with Xcode. I think you can actually install it separately, it’s called Xcode Tools. You can get to it through one of the Xcode Open Developer Tool instruments.
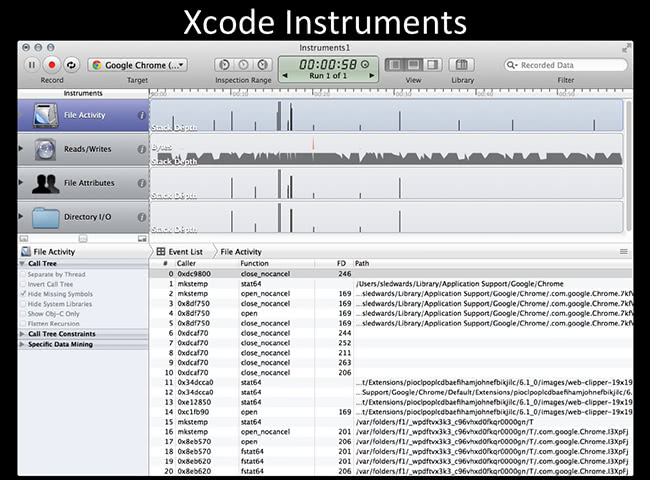
This is a screenshot of what it looks like. It shows you a graphical version of how many files; it shows you peaks and valleys; timestamps and things like that. Quite useful. You can even write Dtrace scripts within Xcode to execute in Xcode. So if you want a pretty shiny version of it, it’s very useful to use.
Read next part: Reverse Engineering Mac Malware 4 - File Analysis