Get detailed analysis of the ransom scam via apple.help@post.com or pass.apple@mail.com and unlock hijacked MacBook, iPhone or iPad without wasting money.
As far-fetched as it may sound, one of the most popular techniques for hacking an Apple device boils down to performing certain manipulations via a specific page on the vendor’s official support portal. The only prerequisite is to have a potential victim’s Apple ID and password to log into the service. Intrigued? This is exactly the way threat actors are locking down numerous users’ iPhones, iPads or MacBooks remotely. Those affected discover that their device has become inaccessible out of the blue, with a lock screen asking for a 4-digit PIN to sort things out. To get this PIN, victims are instructed to send an email to apple.help@post.com or pass.apple@mail.com.
Let’s now scrutinize the anatomy of this hijack. First, a cybercriminal gets hold of one’s Apple ID and the corresponding password to access a prey’s personal Apple account. It’s hard to say for sure where crooks get this information. Some security analysts argue that the source can be a dump of these credentials via Dark Web forums. Another guess is, the felons brute-force the passwords or deploy dictionary attacks to figure them out. One way or another, someone motivated by financial gain trespasses on one’s Apple account. Then, they enable a feature called “Find My iPhone” on behalf of the hacked user. This functionality allows locking a device remotely. Furthermore, the perpetrator enters a custom message to be displayed on the screen of the gadget.
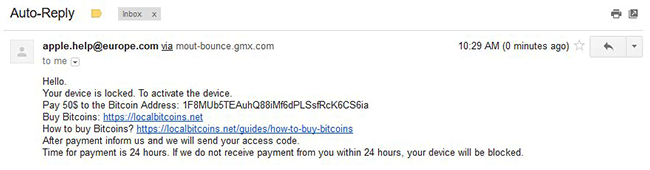
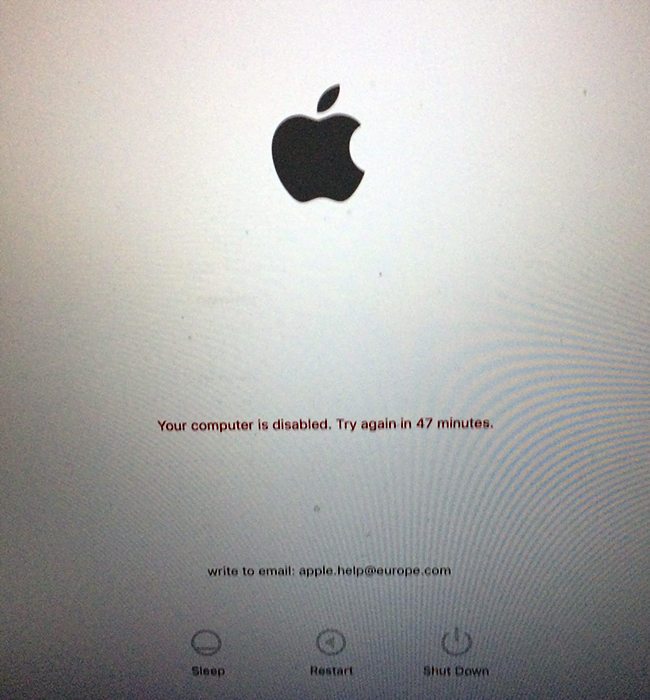
The wording tends to be as follows, “Lost iPhone. Write to email: apple.help@post.com.” Another variant of the lock text displayed on MacBooks goes, “Your computer is disabled. Write to email: apple.help@europe.com.” Note that the email addresses are interchangeable for different types of jacked up devices. If you try and enter a random code, the screen will simply say, “Wrong passcode. Try again.” Of course everyone’s next move is to shoot a message to the indicated address. Once this is done, the victim gets auto-reply (see screenshot above) that says, “Hello. Your device is locked. To activate the device. Pay $50 to the Bitcoin Address: [hacker’s Bitcoin wallet]. After payment inform us and we will send your access code. Time for payment is 24 hours. If we do not receive payment from you within 24 hours, you device will be blocked.”
Ultimately, the user is coerced into paying money to get their device unlocked. One of the main takeaways from this type of incursion is that no malicious code is involved in it. Instead, it’s all about a handy feature abused in the worst way imaginable. The good news is, there is no need to submit any Bitcoins to the sleazeballs. See the workaround below.
Unlock iPhone hijacked via apple.help@post.com / apple.help@europe.com hoax
As per the anatomy of this con, an efficient workaround is to reset the iCloud login credentials. To do this, go to iforgot.apple.com on a computer or other non-infected device and follow the steps below:
• Select the option that says "Forgot Apple ID?"
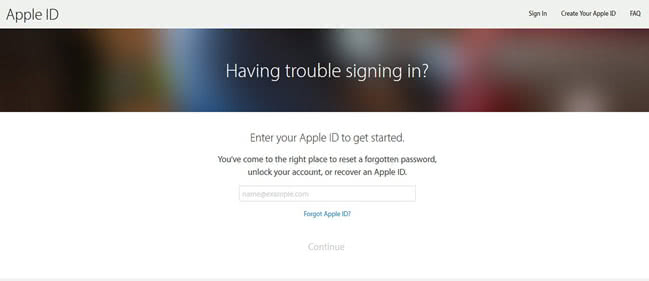
• Enter the requested details, including your first name, last name and email address and click Continue.
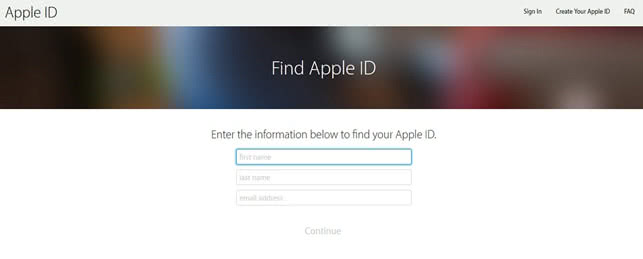
• Fill out the personally identifiable information as instructed and answer security questions you had configured when creating your Apple ID. Alternatively, you can select the "Get an email" option and receive an email to reset your password.
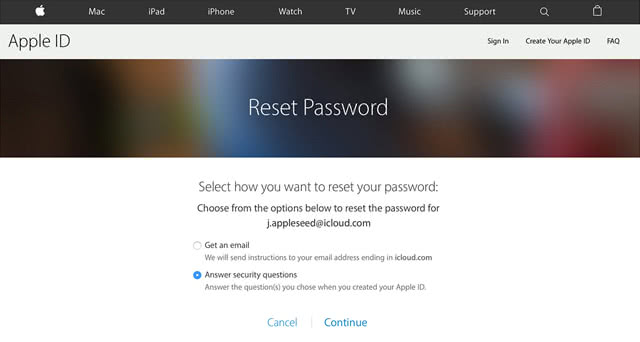
• Follow any further directions until you reset your iCloud password. In some cases, you may have to give Apple Support a phone call to explain your issue and get the reset job completed.
• Use the new password to regain access to your iOS or macOS device.
If your Mac has been locked down with the apple.help@post.com / apple.help@europe.com ransom message, it’s quite likely that it already has viruses like Mac ransomware 2017 or spyware on board. This is why it’s in your best interest to check your Mac for malicious code with the Combo Cleaner security tool.
Prevent Mac lock alert extortion using Combo Cleaner security suite
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove Apple.help@post.com / apple.help@europe.com email scam virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the Apple.help@post.com / apple.help@europe.com email scam issue using Combo Cleaner:
- Download Combo Cleaner installer. When done, double-click the combocleaner.dmg file and follow the prompts to install the tool onto your Mac.
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy. The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
- Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
- Click the Start Combo Scan button to check your Mac for malicious activity as well as performance issues.

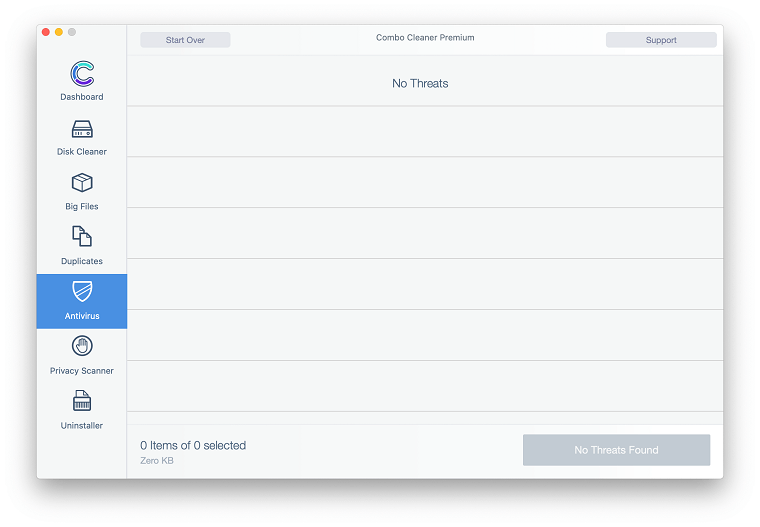
- Examine the scan results. If the report says “No Threats”, then you are on the right track with the manual cleaning and can safely proceed to tidy up the web browser that may continue to act up due to the after-effects of the malware attack (see instructions above).

- In case Combo Cleaner has detected malicious code, click the Remove Selected Items button and have the utility remove Apple.help@post.com / apple.help@europe.com email scam threat along with any other viruses, PUPs (potentially unwanted programs), or junk files that don’t belong on your Mac.

- Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.